In Linux and other UNIX-like computer operating systems, the root account is the administrator account. A user with root privileges can perform many tasks that a standard user account cannot. In current editions of Fedora 17, the idea of a disabled root account is a foreign one.
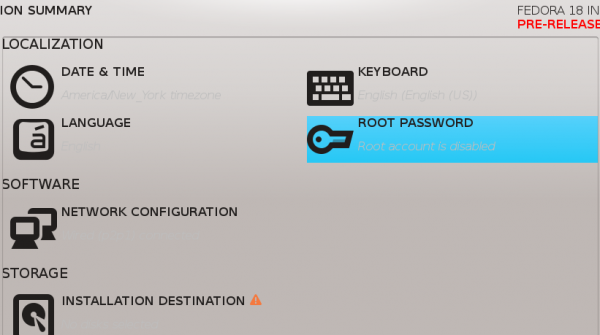
But come Fedora 18, the next stable release, the root account will be disabled by default. It is one of the many new features of Anaconda, the Fedora system installation program. That at least is what you see in the just released Fedora 18 Alpha.
In this screen shot, which from the main interface of Anaconda, you can see below the ROOT PASSWORD button, though not readily legible, a 4-word phrase that says, root account is disabled.

Clicking on the root account button in the previous image automatically enables it, provided you specify the password.

With the root account disabled, the user created during the installation process is assigned to the Administrators group by default. This, of course, gives this user all admin privileges.

For visitors looking to get a site online this web hosting review site provides reviews of cheap, reliable hosting companies all of which operate in a Linux environment.
The thing that I do not understand is, why is it even necessary to disable the root account? Is there any disadvantage to having a system with the traditional root account enabled? I cannot think of any reasonable one, can you?




Disabling root is just more security through obscurity. It doesn’t really make the system more secure — in fact by encouraging the proliferation of superuser accounts (via sudo) I would argue it makes the system marginally less secure. It’s an idea that sounds good at first but actually turns out to be one more complication in an already overly complex system. The real answer is better audit logging and, most importantly, changing the root password periodically (maybe even without advance warning). It is much more practical (and efficient) to keep track of password expiration and usage of one superuser account (root) across 100’s of machines machines than 20 or 30 on the same number, which is actually on the low side for the number of sysadmins who might need root privileges in many enterprise shops.
Hello everyone! I’m new to Fedora 17, and I’ve an issue. I cannot become root in Terminal. I type su – … but I cannot type in my root password. It’s as if my keyboard does not work — but I can type anything else in Terminal just fine.
Can somebody *please* help?
THX!
lmao
you should get a password: prompt but when you type you won’t see asterisks.
su – expects a command following the –
It was waiting for a command.
just enter su
@Leslie… actually, the hyphen tells su to use the target user’s environment variables instead of the current user’s.
While I’m not 100% sure we still do this due to some issues that cropped up, there is a definite security benefit to disabling root on networked systems that have remote access such as sshd enabled – would be attackers know most systems have a root so they try to brute force the root password in remote attempts to access the system. It’s harder to know the user names on a system that are not root and are remotely accessible (although of course entirely possible to figure out with enough cleverness on the attacker’s part and a little less mindfulness on the user’s part.)
Disabling root just because it will make it difficult for brute-force attacks is called “security by obscurity.” It does not work. It’s a lazy attempt at securing a system.
Take a look at the out-of-the-box configuration of PC-BSD. The root account is there, SSH server is running by default, but a software that monitors and stops brute-force attacks is installed by default. That’s how to keep a system secure.
But it’s good to see that root password is required in the the beta edition.
Security comes in layers. Disabling ssh root access is standard and reasonable. But you’re right. A mechanism to prevent brute force attacks and strong passwords are also required.
NO matter what system I have tried, root is not disabled in terminal mode. And sudo su provides root access. If you do the following:
sudo su [enter]
password xxxxx [enter]
#now issue the password command
passwd xxxxxxxxx <— roots new password
Repeat xxxxxxxxx
And there you have changed roots password.
This is the way you do it for Ubuntu. Fedora has the password set during installation.
Ubuntu security danger.
if you do
echo $PATH
you will see as the very first entry,
/home/yourlogon/bin: and the rest of the path entry
Therefore a hacker can put a file into your bin directory and it is immediately potentially executable. (chmod 111 program) or (chmod +x program)
In /bin, program could replace a system command because it appears first in the $PATH
safer is for this entry to be appended to the $PATH.
OK, so here is a thought for you.
You need to manouver files around in your system. Some or many of these files are not your own, but you want to move, copy, or delete them without the danger of making a typo error. The question to answer is "Are you better off doing this via File Manager in Root, or via the root logon and the command line.
Command line typical errors
rm *.c
vs rm * .c
In the latter case you delete the files within the entire directory
In the former case, you really were deleting all the files that end in dot c.
GUI for Root is preferable to preventing errors. You must only discipline yourself to not use the web browser while in root.
If the Root logon is not to be used, do not allow anaconda to ask for the root password.
With Fedora, it is a catch 22. If you screw up Firstboot, at least one will have the root password in order to effect corrections.
If you need to change ownership of files, you need the root level for the administrator.
Therefore, we assume some intelligence and we allow, but do not publicize the root use of GUI interface.
Sudo nautalus . provides root access in GUI mode. therefore it is counter productive to block GUI root access.
Sorry to reply in January, but Fedora 19 is soon here and I would want Fedora 19 to follow the implementation rules of Fedora 18
Finally!
That probably was single most visible annoyance which prevented my migration from ubuntu.
Having to remember separate password is plain useless – especially considering that enabled root account is immediate security threat: when it’s disabled attacker got to figure out username first.
Keep up the good work, Fedora team!
I hate the idea of disabling the root account and putting the first user into the admin group. It’s an idotic Windowism. *nix has been server very well by forcing a separation between root privileges and user privileges. When you do an administrative task you should have to think about it, requiring a separate root password enforces this.
I always enable a gui root account. It is safer to use it than being all the time forced to a command line account.
If I had files that were of differentnames, but with a common extension, (*.doc or *.txt), I could sort the view in a window, or use a filter, and then check off the ones I wanted to delete. Pretty easy, and fast.
In command line. I may want to delete all my files that are of type ab…..txt or all the text file.
The usual command is rm *.txt (I know, I should use rm -i )
but what happens when you mistype at 11:30pm, after a full day being busy and you quickly enter
rm -f * .txt
The message returned is cant find .txt but all the files and sub-directories are wiped clean. Wow, get out the backup, we need to restore.
GUI interfaces for management of Linux make for fewer errors and shorter management task times.
There are times for both GUI and command line. The challenge is to see how, via a GUI interface, we could write and run scripts, or do terminal commands without entering terminal mode.
The usual
GUI root account for deleting .doc files? Really?
Even IF there would be any valid reason (apart from package management) to start a GUI application with root privileges, it’s really easy to get it via “kdesudo dolphin” or similar.
But Firefox or Kmail as root – never ever.
Thanks for the article
Thats a really big change. You have to click once, before root is enabled.
I like sudo. With sudo I can run things like Truecrypt or little scripts from desktop without password. And if there is one user in the admin or wheel-group it is much the same as traditional root. Maybe you should not use this user for daily desktop-usage because its password is root-password. I also prefer su more than wheel-group or admin-group because it is shorter to type su than sudo -i. 😉
Disabling root on a Linux distribution creates a completely unnecessary hassle for a user. Whenever I run I install a Linux distribution with a disabled root I immediately enable root so that I can customize the distribution to my taste.
The logic of why anyone would want to disable root completely escapes me.
——————-
Steve Stites
a simple reason: you’ll have only one password to be created/remembered.
this article shows how to disable root user during the installation.
I just finished a fresh install and now i’m breaking the wall with my head 🙁
I’d like to know how cani now ( *after* the installation) disable root login , so that i can switch to sudo.
I usually prefer root + normal user, but since i have more than 1 pc i need to keep password creation/remembering as little as possible.
I believe you want to setup sudo with your account as administrator, and thereafter, disable root logon.
With your root logon,
do enter visudo
Look for the line(s) that are #%wheel ….
With Debian, the #%sudo replaces #%wheel.
Remove the comment on the %wheel line that you like.
One line gives you limited access with a password always required,
The second entry gives you root access without the need for a password.
After you save and exit,
add the wheel (or sudo) group to your user.
logout from root.
log into your account, which is now the administrator account. You can of course create several administrator accounts.
Now, I have never mangled the root password, as Fedora needs it for certain hardware changes (mount, for example).
However, I believe you can lock root, though I never tried it.
issue the sudo su
this should put you into root pid 0,
(check with the command id
Thereafter, you need to garble the password account to force you to always use sudo.
situation:
pc + notebook
root partition is encrypted
if i manage do disable the root user, i need to keep in my memory ‘only’ 4 password.
if i keep the root user enabled i have to create and remember SIX password.
The reason root is disabled is because a lot of people do everything as root and they end up hosing their systems. Windows users do everything as an administrator. That’s why you have so many easy to use and compromised windows systems. Use sudo.
“The reason root is disabled is because a lot of people do everything as root…”
You just betrayed your ignorance on this particular subject. Btw, where did you get that info from?
I installed Ubuntu for a friend; I really disliked to work with sudo, so I enabled the root account. In Ubuntu, you can do this by typing “sudo passwd root” and entering a root password. If you can do this in Fedora 18, then disabling root by default may not be a bad idea; if you cannot, then disabling root is a terrible idea.
Sudo sucks! Why must I be protected from myself? I really hate how the use of sudo has spread like it has. Many of us think there was nothing wrong with the old method. I’ll pass on Fedora 18…
Sudo is a way of not working all the time backed by root privilege. If you can do it malware pretending to be you can do it also. It is a safety feature.
If you want to be root all the time, run windows 98.
Before you say there is no malware for Linux – If everyone ran backed by root privilege the malware writers would be on us in a clock tick.
You fail to realize, that because you’re not using sudo, doesn’t mean you’re running as root all the time. I simply login to be root the old way, using the ‘su’ command and do my dirty work, and exit it when I’m finished. This is not running as root all the time.
Fedora is for home users and people who want to be guinnea pigs for RHEL. So why, as a home user, do _I_ need protecting from _myself_? The whole point of Linux is an OS that’s not dumbed down like Windows, yet this is exactly the OPPOSITE. It’s saying the people that install Linux are too stupid, and will bork their system, so we’re gonna protect them from doing that to themselves by disabling root by default and forcing them to use sudo, instead.
sounds good. but most people do not have your discipline. they run as root all the time. like windows users.
Anyway, if you really want Fedora for _personal_ use (I’m not talking about and enterprise environement) :
sudo su –
yum remove sudo
Else, Arch Linux is highly customizable, only essentials are installed initially, and sudo is not in the essentials.
Let me get this straight.
1) You have root disabled
2) You use ‘sudo su -‘ to make yourself root
3) You remove sudo so it can never be used again
4) Now, How do you install, & uninstall software, and do other administrative tasks???
Am I missing something in your logic??? ;^)
Well one can re-enable the root account in /etc/shadow, with an appropriate hash and shell :
sudo su –
vim /etc/shadow
yum remove sudo
Still don’t understand why should a user have a virtual nanny on his personal computer ! A user’s personal data is far more important than system files, we can always re-install. Would there be a feature preventing deleting personal data, i.e, protecting a user from himself as argued ?
I never use sudo, ever! I really don’t care if it is installed om my computer or not. I simply ignore it! There is NO REASON to remove it from a system. If multiple users are using a Linux system, some choosing to use su, and some choosing to use sudo, FINE!!! What is the problem???
I don’t use Ubuntu for many reasons, but one of my biggest objections was that they treat their users as irresponsible children, taking root away from them! If Fedora also follows this route, then they have lost my respect as well!
I’ll stick with Debian!
Once you remove root, then what is next??? Like censorship, it is a VERY slippery slope!!!
Bottom line:
LEAVE ROOT ENABLED, SUDO INSTALLED, AND LET’S MOVE ON TO MAKING THE LINUX DESKTOP UBIQUITOUS TO EVERYONE!!!
Again, I shouldn’t have to. I don’t need protected from myself, and considering this is Fedora, which is meant for the bleeding edge Linux proficient user, unlike distros like Ubuntu and Mageia, this is a slap in the face!
most users need soft little mittens on their hands so they don’t scratch their baby faces all up. 🙂
sudo is another way of making admins feel secure , its Tylenol
Agree !
Once the system is installed by a home user supposed to be protected against himself :
sudo rm -f /boot/*
He doesn’t even have to remember root’s password !
Different situation in the enterprise, where Fedora would not be, rather RH. There, sudo may help sys admins to protect the systems, i.e., themselves, not users.
“sudo rm -f /boot/*
He doesn’t even have to remember root’s password !”
/etc/sudoers:
Cmnd_Alias BAD = /bin/rm -f /boot/*, /bin/rm -f /boot/.*, /bin/rm -rf /boot, /bin/rm -rf /, /bin/rm -rf /*, /bin/rm -rf /.*
%wheel ALL = ALL, !BAD
now try that “sudo rm -f /boot/*”
it will fail with a nice little message that you are not allowed to do that
Are you **sure** you have covered **all** the stupid stuff?
No, of course not, my point was that you can add custom rules to prevent mistakes. Can every single possible mistake be caught? NO
Can many be caught with sudo that would have been missed by just running as root? YES
There is no way to prevent any system from accidents 100% of the time. There is a way to add security to systems and catch WAY more than with out the added security. A user/admin still has to use common sense and try not to do something that bad.
If a user installs Linux, and is the ONLY user/admin (as in a home computer or laptop), and they are determined to run **all** the stupid stuff… Then they should just enter the password for root the same as they have always done during install. Then immediately after root they can “su -” as they always have, and they can run the fun little system imploding commands that make their day if they like.
I am not really sure what the problem is. The **option** to set the password and leave root enabled is still in the installer just like it has always been. The only difference now is that you have the freedom of choice to NOT set it and use sudo. It is Linux after all, and it is about freedom and choice. 😉
“sudo rm -f /boot/*
He doesn’t even have to remember root’s password !”
/etc/sudoers:
Cmnd_Alias BAD = /bin/rm -f /boot/*, /bin/rm -f /boot/.*, /bin/rm -rf /boot, /bin/rm -rf /, /bin/rm -rf /*, /bin/rm -rf /.*
%wheel ALL = ALL, !BAD
now try that “sudo rm -f /boot/*”
it will fail with a nice little message that you are not allowed to do that
With a freshly installed system for a home user, there are no such restrictions.
In the enterprise, how much can you prevent a system-breaking command ?
sudo touch /boot/vmlinuz
sudo echo 0 > /bin/sudo
…
How many nice little messages will you have prepared ?
OK, so your contention is that running as root will stop any of those?
My point was you can add custom rules if you like or simply review the logs for sudo to see who did what. Neither of those can be done with just running root.
All of these comments designed to show how to possibly circumvent security that can be added to sudo (that simply DO NOT exist with root) prove that you are more into the argument than the point.
These things would be the fault of the admin. Make no mistake, as a home user you are the admin of your own machine.
Sudo is not meant to be a baby sitter for a bad admin. It is meant to be a better way to secure your system if you chose to be responsible and an audit trail that never existed for times when mistaken (or intentionally bad) commands break things.
Also, and for the last time… if you do not want to use sudo, simply set a password for root during install, that simple. No one had killed your puppy people. You have had to set a root password in every Linux install you have ever done, how is this one different? Other than giving you the *option* (as in choice/free/open) to not set it and use sudo.
At the end of the day, it is still there and you can still do what you are used to doing if you chose.
Please leave the root account alone! I know what I am doing!
LOL the very fact that you just said that proves that you obviously do not know what you are doing.
Seriously? What a dumb statement…
Maybe I was too short in my remark, so yes it might have seemed like a dumb remark.
Let me explain what I meant.
You see your teenage boy point a loaded gun at people and himself. You decide to make sure he (and others) remain safe and remove the bullets from his gun.
Your teenager says don’t take the bullets out of the gun, I know what I am doing…
Same thing really, just because he knows how to aim and pull the trigger does not mean he is responsible with it.
In this case though, the bullets are not taken from you, the gun can still be loaded and shot.
Root is not gone. It is still right there. Simply run “sudo su -” and you have full root exactly as you would had you typed “su -“.
This decision is more for safety and security because it stops hackers from getting in as root, and it teaches users good habits. 😉
Dumb
This sounds like the windows way of doing things.
Everyone has admin? This to me is not secure or wise, since Linux means security on the initial setup. Which has been compared to windows previously in many articles that said this is why Linux was more secure out of the box.
Bad move Fedora.
This is a lie that has been disproven in several comments here already. EVERYONE does not have sudo access by default!
Please read the other comments and also actually familiarize yourself with this tool.
SUDO is a tool that was designed to allow sysadmins to provide limited access to system functions to assistant admins.
Its primary usage is in large networks in business and education systems.
There are commands in Linux that require an actual admin login or password in order to execute. SUDO or even “SU” does not provide access to these few, specific commands.
SUDO is essentially an admin tool for users and systems that require a higher level of access control.
In a “normal” SUDO environment, certain users are provided limited access to preform specific commands to be executed in the course of their jobs. The use of SUDO to impart all admin level privileges to every user in the wheel account group is not the intended usage.
What happens in ubuntu or any other distro that makes sudo all encompassing is that you now have multiple access points of admin privileges. Should access be gained to anyone who has walked up to a computer account left open, risks are now increased that the session can be used for ill purposes.
If there are 5 users on such a system, there are now 5 points of access to full admin privileges. In a professional setting, this is not as much of an issue due to the training/education of those users in computer usage and work habits. In a home or other “average user” setting, this becomes an increased risk.
With the root account disabled, a hacker would have to know a user name on the box as well as the password, so it can be more secure–all else being equal.
I agree that setting up 5 users on a system with full admin privileges may not be a good idea. So don’t do it. You can use sudo to restrict the privileges to only what they need.
If nothing else, you can create a different “super user” account with all the privileges that you can su to. This would work just like “root”, except with a different name that would be less likely to be known to a hacker.
“There are commands in Linux that require an actual admin login or password in order to execute. SUDO or even “SU” does not provide access to these few, specific commands.”
“$ su” DOES ask for the ‘root’ password, elevating the privileges to ‘root’! What specific commands are NOT allowed through the use of ‘su’??? If there are any, in all my years of using Linux, and UNIX before that, I have NEVER encountered ANY of these alleged commands! ;^)
VLC. It does not start in a root environment.
It is stupid to start a media player with administrator privileges.
“Its primary usage is in large networks in business and education systems”
This is utter crap, do not believe this. Every distribution that I know has sudo installed by default and many have it even setup for you by default. If you choose not to use it, then that is you failure.
“There are commands in Linux that require an actual admin login or password in order to execute. SUDO or even “SU” does not provide access to these few, specific commands.”
Prove it, show me one… go ahead, I’ll wait.
“SUDO is essentially an admin tool for users and systems that require a higher level of access control.”
Replace the word SUDO above with root… it still holds true. So what exactly was the point in that statement?
“The use of SUDO to impart all admin level privileges to every user in the wheel account group is not the intended usage.”
Correct, that is why by default only the first user, created at install time, has sudo access.
“What happens in ubuntu or any other distro that makes sudo all encompassing is that you now have multiple access points of admin privileges.”
Please explain when “ubuntu or any other distro” has ever made sudo “all encompassing”. The user can do that but by default it is actually LESS encompassing than root as it is available to on 1 user. Simply put the single admin has EXACTLY the same privileges as root, and nobody use it because they are not in the correct group.
“Should access be gained to anyone who has walked up to a computer account left open, risks are now increased that the session can be used for ill purposes.”
BULLCRAP!
By default you HAVE TO ENTER YOUR PASSWORD TO USE SUDO.
Let’s say you change sudo to be passwordless (your fault mind you)…
This is different than logging in and walking away from your computer (left open) how?
Come on you do have to at least think people.
“If there are 5 users on such a system, there are now 5 points of access to full admin privileges.”
Again, this is not so by default. Only 1 user is given sudo access. The user set up during install! THATS IT 1, NO MORE NO LESS.
and finally….
“In a professional setting, this is not as much of an issue due to the training/education of those users in computer usage and work habits. In a home or other “average user” setting, this becomes an increased risk.”
2 points on this..
1. You wouldn’t know anything about a professional setting obviously… you clearly are not a professional
2. In a home user setting, having full root is WAY less secure. Not to mention harmful to the untrained users. It is easier to forget you are logged in as root and do things that should not be done as root.
By disabling (NOT REMOVING) users are forced to do what they should always do… NOT LOG IN AS ROOT. The sudo tool is made to escalate privileges as need and NOT run as root user when not needed. It is there to protect you. There is NOTHING that cannot be accomplished with sudo that can be with root.
“There is NOTHING that cannot be accomplished with sudo that can be with root.”
Not quite true. On the Scientific linux install I am using, the graphical tools prompt for the root password, instead of asking for sudo root access. For example, I just ran “software update” and it asked for the root password. Yes, I could go to a command prompt and type sudo yum update instead, but because of the silly design of the Graphical Environment, root is required if you don’t use the command line.
alt+f2 (or on command line)
Then type:
sudo pirut
Now you have your graphical “Add/Remove Software” tool with root privileges!
It will not ask you for a password now. 😉
Where there is a graphical menu item, there is a command that it runs…
Your aggressive tone is typical of users of a distro that starts with U and ends with buntu. Hope your not a Fedora user.
sudo, at least in Ubuntu, has a default timeout of 15 minutes. That’s a great security risk.
This is true only for the current terminal session. If you switch terminals, you have to enter the password again for each terminal.
The timeout does not exist for graphical applications. You will be prompted for your password for every modification to the system.