A Virtual Private Network (VPN) allows establishment of virtual connections between parties across a public network. As part of these connections, the identity of the communicating nodes is concealed and associated data traffic is secured. A network of such links offers secure access to remote locations across the Internet as if users were accessing a local private network.
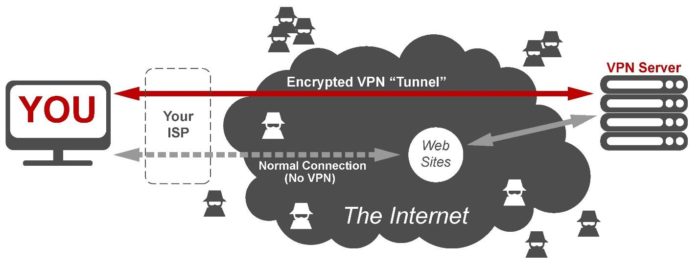
Figure 1: Visual representation of a VPN connection
Choosing A VPN Provider For Windows 10 – The market for personal computers is still dominated by the Windows operating system, with Windows 10 reaching a user share of roughly 40% of all PCs just three years after release. A number of unique vulnerabilities have been identified in Windows 10 along the years, such as those related to its native browser, to faulty .NET apps, or to Bashware (exploits that target the built-in Linux shell). Sometimes the only solution to ensure complete protection from such security gaps is to use a VPN, so one would inevitably wonder which Windows 10 VPN provider to go for and what the key selection criteria should be.
There is a series of key factors intrinsic to the VPN service itself that would normally inform this choice. These factors are:
- the type of encryption protocol best suited for the particular user – this is normally a trade-off between security and access speed/bandwidth.
- the number of simultaneous connections – this enables access by multiple devices.
- availability of a wide network of servers worldwide in order to allow efficient access to geo-restricted content but also to avoid traffic bottlenecks
- P2P friendliness – describes whether the service can work with torrent applications.
- logging policy – describes which data is collected and stored in logs (less sensitive data collected is better).
Coverage Of Multiple Operating Systems And Devices – Given today’s realities, a top VPN service would not be restricted to just one OS and one device (the one described on this site can cover up to six devices). Such services usually include:
- mobile apps for both Android and iOS devices.
- standalone applications for personal computers running macOS, Linux, and Windows.
- proxy extensions for browsers like Chrome and Firefox (these enable flexible cross-platform use).
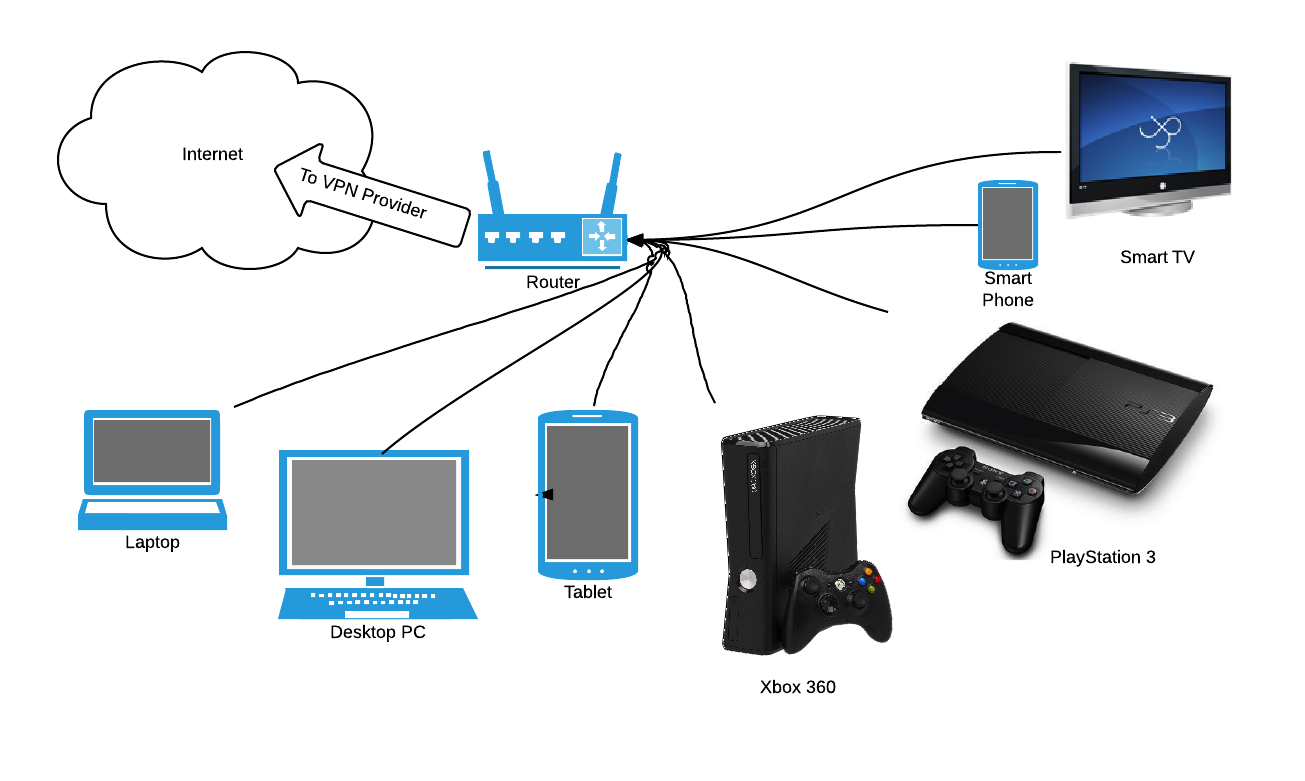
Another good strategy to ensure secure data access for multiple Wi-Fi-enabled devices simultaneously would be to set up the VPN on the router itself.
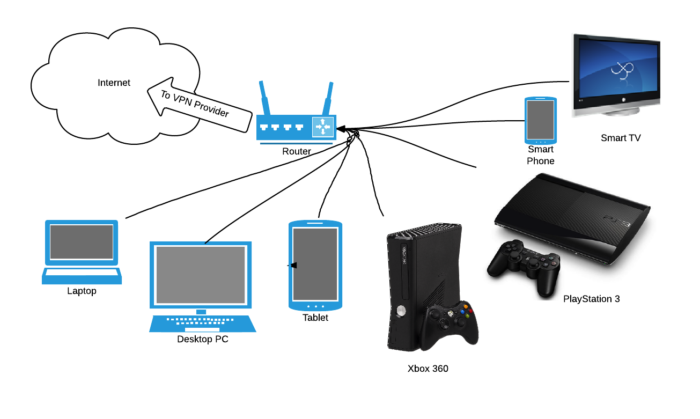
Figure 2: Setting up VPN on a router
Comprehensive Online Resources On VPNs – There are a few resources online where one can compare different VPN services and learn which of them works best with a given operating system, a given application, or even in a specific country. Bestvpnrating.com is an example of such a resource. It also contains a wealth of information on Internet privacy, enabling users to gain awareness of the current trends and state of the art in Internet security. cooltechzone is another online resource for free VPN services.
To conclude, not every computer user will need a VPN service, but for those that do, we’ve presented information in this brief article to make choosing the most appropriate one for your device and OS a bit easier. Whatever the cost, it’s a small price to pay when you need to enhance your security posture on the Internet.
This article has been published in accordance with linuxbsdos.com’s disclosure policy.