A security adversary posted at Red Hat’s security blog and referenced at US-CERT has warned users of the Bash shell of a “specially-crafted environment variables code injection attack.”
That means UNIX-based operating systems that use the Bash shell are affected. That includes all Linux distributions and Apple’s Mac OS X.
According to the blog post cited above:
… the vulnerability arises from the fact that you can create environment variables with specially-crafted values before calling the bash shell. These variables can contain code, which gets executed as soon as the shell is invoked. The name of these crafted variables does not matter, only their contents.
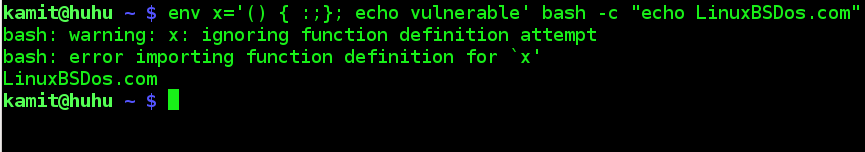
The flaw is said to have been fixed in Red Hat Enterprise Linux and a package that fixes it shipped for Fedora, but I am running a fully updated Fedora 20 KDE and the package has not comes across. To test whether your copy of Bash is vulnerable, issue this command: <strong>env x='() { :;}; echo vulnerable' bash -c "echo LinuxBSDos.com</strong>. If your Bash is vulnerable, you should see both echoed texts.
This screenshot shows the result of the test on my Fedora 20 desktop.

On my laptop running Linux Mint 17 Cinnamon, the test showed that it, too, is vulnerable. However, after updating it, the test passed. The following screenshots shows the results of the test before and after the updated was applied.
Bash test on Linux Mint 17 before code injection attack update.

Bash test on Linux Mint 17 after updating the system.

UPDATE: If you use Fedora 20, your only option, before an update is pushed through the system, is to patch it manually. To do that, type the following command, as root: <strong>yum localinstall https://kojipkgs.fedoraproject.org//packages/bash/4.2.47/4.fc20/x86_64/bash-4.2.47-4.fc20.x86_64.rpm</strong>. That came from this post. For other editions of Fedora, see this other post.




The article says, “That includes all Linux distributions…” It would be more accurate to say, “most Linux distributions,” or better yet, “virtually all Linux desktops and servers.” Most versions of embedded Linux don’t include bash and are not vulnerable. However, most distributions for customizable semi-embedded devices like the Raspberry Pi are/were vulnerable.
Yep, Red Hat has addressed that point in this update. Relevant paragraph:
it’s the final ” that is missed in your example…
env x='() { :;}; echo vulnerable’ bash -c “echo LinuxBSDos.com
on the last point of your command text, there is no this one “
thxs for your contribution, but in your command text is on the end a fail:
Must be:
env x='() { :;}; echo vulnerable’ bash -c “echo LinuxBSDos.com”
Greetings TLW
Why is it a fail? The text can be anything.