ufw, the Uncomplicated FireWall, is Ubuntu’s user-friendly, command line frontend to IPTables, the command line utility for managing Netfilter, the firewall application built into the Linux kernel. It is installed not just on Ubuntu, but also on all Ubuntu-based distributions. As simple to use as ufw is, a graphical interface is even better, especially for new users.
This article, presents the three graphical interfaces for and managing ufw that I am aware of. If you know another that is not listed here, tell us about it. Note that this is not a tutorial on how to configure them, just a listing.
So, here they are, in alphabetical order:
- Gufw – This is the graphical client available on Ubuntu and Ubuntu-based distributions.This is Gufw’s interface in its enabled state.
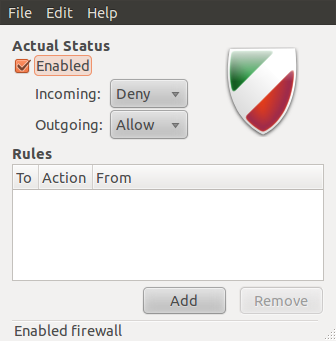
The Simple tab allows you to create rules with a port number defined. This makes it possible to create rules for services and applications not preset in the Preconfigured tab.
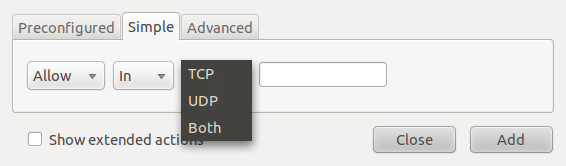
The Advanced tab makes it possible to create more specific rules using source and destinations ports and addresses. If you are looking for a guide on how to configure Gufw, how to configure a graphical firewall client on Ubuntu 10.10 is a good one.
- KDE Control Module-ufw – This is the K Desktop Environment’s firewall control module and it is typically installed on non-Ubuntu, (KDE) distributions.
The main window. The tooltip shows the outgoing policy options.

And this is the same window showing the logging levels.

The default rule adding window presents an interface for adding very general rules. It is the simple rule adding interface.

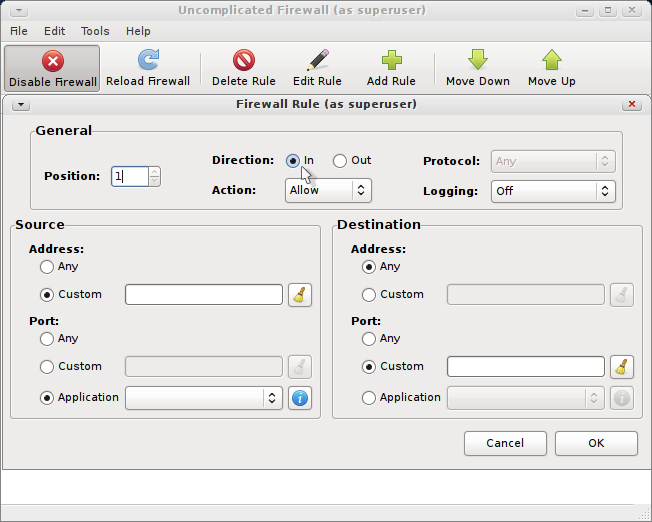
This is advanced window for adding rules. It makes it easy to add more specific rules. Stay tuned for a step-by-step guide on how to configure this graphical interface to ufw.

- ufw-Frontends – This is a PyGTK and PyQt interface to ufw. It is written and maintained by Darwin Bautista and it is the graphical firewall client installed on Sabayon 6 GNOME. This screenshot is the main window.

There is no simple or advanced rule adding window on ufw-Frontends, just a rule adding window. It provides all the options needed to add general or very specific rules. Stay tuned for a step-by-step guide on how to configure this graphical interface to ufw.




I guess my post was also a question….I thought Firestarter is just a GUI for UFW…but since I wasn’t sure, it was phrased as a possible question for confirmation
Firestarter is a separate project. No connection to UFW.
I wrote a bunch of application profiles (200?) for use with Ubuntu. They were submitted to the Ubuntu devs but there hasn’t been any progress in getting them in the repos.
http://jhansonxi.blogspot.com/2010/10/ufw-application-profiles.html
I have been using Firestarter actively on my Ubuntu 10.04 and 10.10 systems, and it works great. Firestarter also works in 11.04 as well, but a little work has to be done to enable Firestarter to successfully write messages to log files.
But that is not the same as saying that Firestarter runs atop ufw.
How about Firestarter? Isn’t that also a graphical end that runs on top of UFW?
You will have to show me some proof.
AFAIK, Firestarter was in active development at least 4 years before somebody came up with the idea of creating a Linux distribution called Ubuntu. And ufw is a recent addition to Ubuntu. I think it was in Ubuntu 8.04 (2008) that ufw made its debut.
So, unless Firestarter’s developers changed its codebase to that of ufw after 2008, my response to your comment is, nyet.
But I could be wrong.