Remember PC-BSD? As a desktop, FreeBSD-based operating system, It’s effectively dead.
Here’s a summary of what happened.
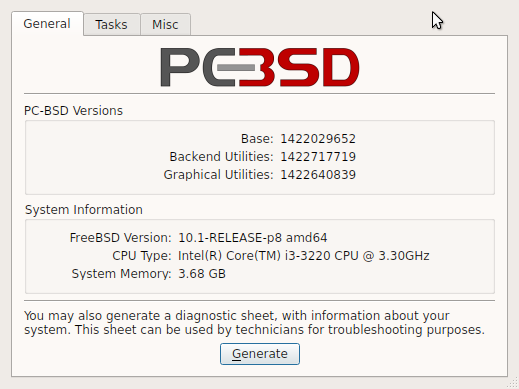
For a long time, PC-BSD was the lone, usable, for most users, BSD distribution targeted at desktop users, with KDE as the desktop environment of choice. And it remained that way until 2017 when the developers started their own desktop environment called Lumina. The first iterations were terrible. At some point there was a server-oriented implementation called TrueOS. By 2018, the direction of the project had changed, with the merging of both projects under the TrueOS brand. By the end of that year, the desktop end of the project under the TrueOS name was effectively dead, and by early 2019, the first edition of the project under the Project Trident name was released, still with Lumina as the desktop environment.
Not long after that, the developers had ditched the TrueOS/FreeBSD heritage and built the project atop Void Linux, an original Linux distribution with xbps as the package manager and runit as the init system and service supervisor. The first edition of Project Trident as a (Void) Linux distribution was released just last month (February 2020).
So that’s how PC-BSD died and was born again as a Linux distribution. I haven’t played with that first release, so can’t tell you how good or not-so-good it is, but I should have time to do so soon, now that I’m back to blogging. Eager to try it yourself? Head on to the Project Trident page for all the info you need to download and install it on your system.