Prey is a cross-platform (Android, Linux, iOS, Mac OS X, and Windows desktop) anti-theft tracking software that, when installed and activated on a supported device, makes it possible to remotely locate, lock, wipe and recover it, if it’s stolen or missing.
It’s a good piece of software to install on your Linux computer, whether that computer is a desktop or a notebook.
And the best part is, it’s free software, with the source code hosted on GitHub. If you’re curious, you may view the source code of the various components at github.com/prey.
So how does Prey work?

Simple. You set up an account at https://preyproject.com/, then install an agent on your computer or computers that you wish to protect. It doesn’t necessarily have to take place in that order, but both tasks must be completed for the service to work. The service has a free and a Pro version, which starts at US$5.00/month.
Once the device is activated, you can begin to monitor it from the browser-based interface. If the device is stolen or missing, you can take a number of actions from your account, like lock or wipe it. Snapshots of the desktop or of whoever is sitting in front of the device can also be taken.
Provided your computer has WiFi access, Prey can geolocate it, which will help in its recovery. Many such recoveries have been reported from around the world, including from countries like Chile, Iran and South Africa.

So you see, Prey is a very useful piece of software.
Since Prey works only after the computer is powered on, what happens if the computer’s hard drive is encrypted?
In that case, the new “owner” of the computer will not be able boot into the system, which means (s)he can’t access your data. The flip side of that is the Prey agent can’t call home, which means you won’t be able to recover yoour computer.
So that’s something to consider when evaluating Prey. What’s more important? Being able to recover your computer, which might not happen, even with Prey installed, or making sure that nobody but you can access your data, which is the peace of mind you get from encrypting the hard disk.
Tough decision!
Here’s what I’ll do – forgo Prey, encrypt the disk and have a backup system in place. There are other physical security measures you can take to frustrate whoever gains unauthorized, physical access to your computer besides encrypting the disk, but that’s usually enough.
The other option is to install Prey and still encrypt the disk, so that in the unlikely event the disk is decrypted without the configured passphrase, Prey will be able to call home and hopefully, help you recover the unit. If you go this route, remember to also have a backup system in place. You can’t lose your data by backing it up.
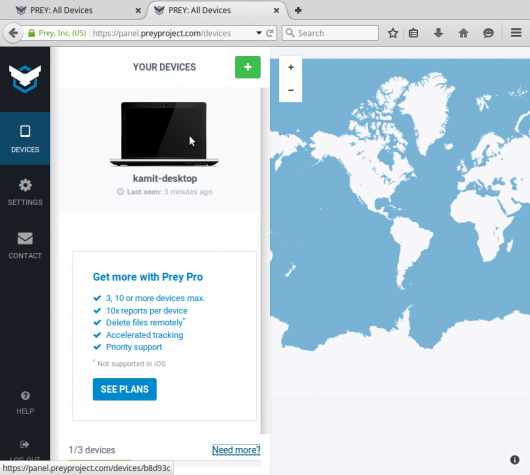
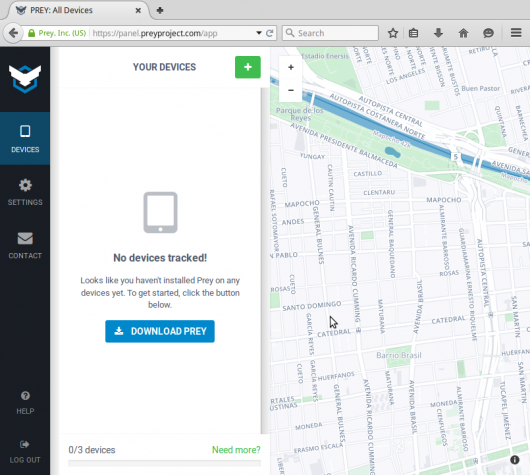
This screenshot shows the Prey Web UI before any device is registered.
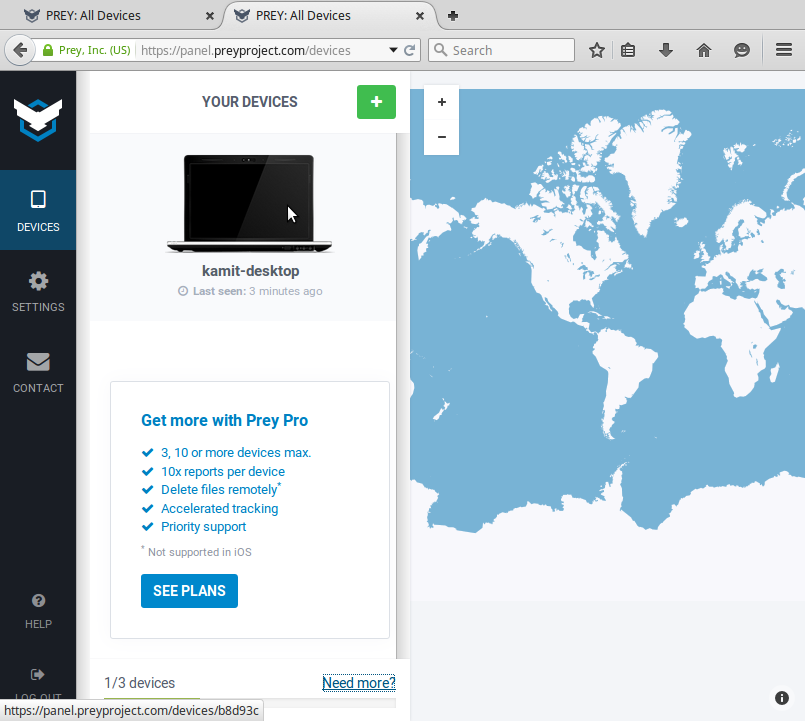
And this one shows the same interface after a device has been registered and is being tracked.