The bug that was discovered and patched in the Bash shell is still vulnerable to code injection attacks. And the latest is that the bug, now officially known as Shellshock, is being exploited by a computer worm. But nobody seems to know the extent to which the attacks have been successful.
The problem with Shellshock, is that many of the devices that could be vulnerable cannot be patched. Such devices include embedded devices that are powered by highly modified versions of Linux. Home Internet access routers and webcams are another group of devices that are susceptible to Shellshock, besides all the Internet-facing Cloud servers and personal computing systems that run a Linux distribution.
The latest statement from Red Hat, Inc., which was the first company to publish a patch, says that “the patches shipped for this issue are incomplete. An attacker can provide specially-crafted environment variables containing arbitrary commands that will be executed on vulnerable systems under certain conditions.” That’s the bad news. The good news: The bug in the patch “is a less severe issue and patches for it are being worked on.”
Reuters has reported that experts they spoke with are saying that “For an attack to be successful, a targeted system must be accessible via the Internet and also running a second vulnerable set of code besides Bash.” But nobody is saying what those “second vulnerable set of code” are.
A new test that anybody may conduct to determine whether their copy of Bash is vulnerable was posted on the Twitter account of Tavis Ormandy. Try the code: <strong>env X='() { (a)=>\' sh -c "echo date"; cat echo</strong>. Actually, that is not the only line of code that you can run to test whether your copy is Bash can be exploited. But that should be enough. If your copy of Bash is vulnerable, there should be a file named echo in the directory that you ran the code in. Delete it and wait for the next patch.


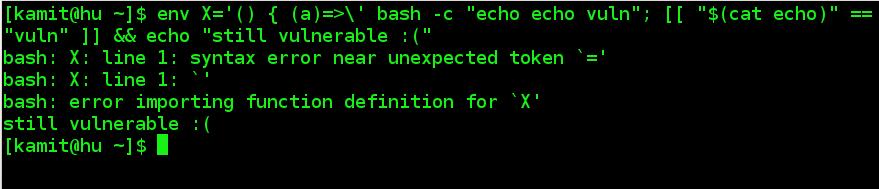






The latest patches that were released last night do fix this bug. Which is to say that my test system passes the checks that have been put out there once the updates are applied.
This article is very misleading about embedded devices. The vast majority of embedded devices don’t have bash installed and were never vulnerable to this exploit. Most embedded devices use a lightweight shell like ash.