This tutorial presents a step-by-step guide on how to configure full disk encryption manually on Ubuntu 13.10 and Linux Mint 16. It will also work for any other Ubuntu-based distribution, like Linux Deepin.
The point of setting up encrypted partitions manually is so that you can create more than the two default partitions (root and swap) created by Ubiquity, Ubuntu’s graphical installation program, when the automated disk partitioning mode is used and the LVM and disk encryption options are selected. And also to be able to do that when attempting to set up a dual-boot system between, say, Ubuntu or Linux Mint and Windows 7 or Windows 8. The automated partitioning mode does allow using LVM and disk encryption when setting up a dual-boot system.
The problem is that even the manual step doesn’t work as well as it is supposed to, as you’ll see later in this tutorial.
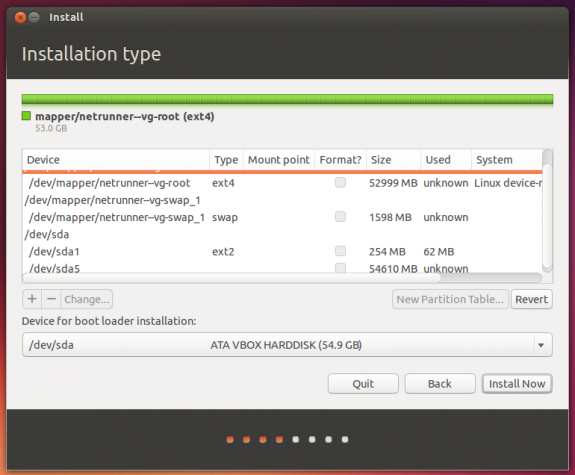
Before we start, let’s take a look at the default partitions and logical volumes that the installer creates when LVM and disk encryption are selected. This screen shot, which was taken from a test installation of Netrunner, shows those partitions and logical volumes. You can see that the first partition – /dev/sda1, mounted at /boot, is a standard partition. The second partition – /dev/sda5, is a logical partition. It is that logical partition that the installer uses to create the LVM Physical Volume. Under that Physical Volume, the installer then created the encrypted Logical Volumes for LVM. You can see the Logical Volumes listed at the top section of the image.

For this tutorial, we are going to create a separate encrypted partition for /home. It is not absolutely necessary, but it’s always nice to have /home in a separate partition. This screen shot just shows the installation requirements for Ubuntu 13.10. You can see that the recommended disk space (for Ubuntu 13.10) is 5.9 GB. The actual disk space used by a fresh installation of this edition of Ubuntu is 3.2 GB. That should give you an idea of how much disk space to allocate to the root partition.

That ends the introduction. Let’s get to the real thing. The test system used for this was a guest OS in a virtual environment, and 100 GB of disk space was allocated to it. The goal is to create manual partitions, with a standard partition mounted at /boot and three encrypted partitions, one each for root, home and Swap. Note that because of the manner the graphical installer works, LVM cannot be configured manually. So this tutorial has nothing to do with LVM, just full disk encryption. It creates a minor inconvenience that we’ll see later in this tutorial.
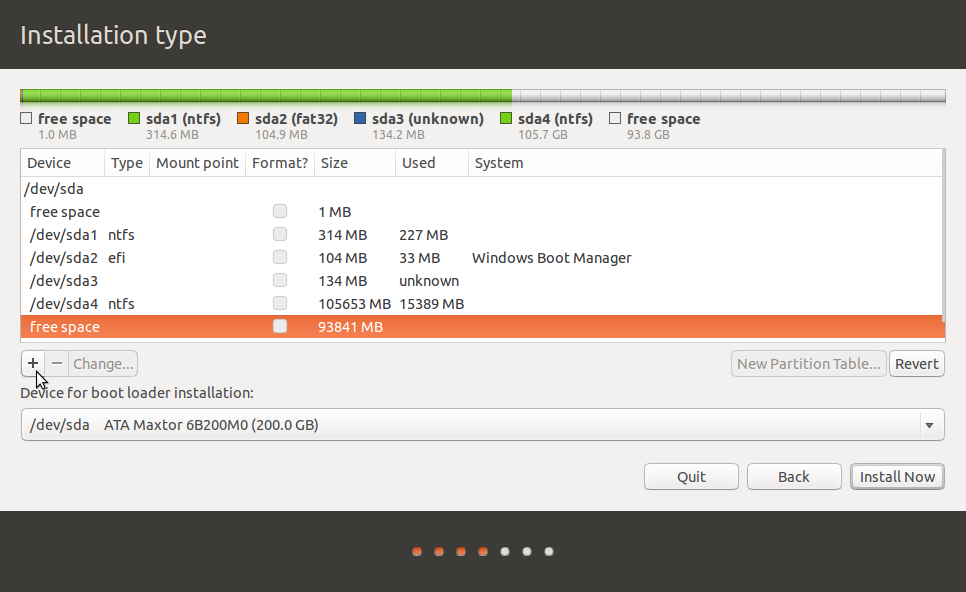
Ok, boot the computer from the installation media that I’m sure you have created by now and start the installer. Click until you get to the “Installation type” step. Since we want to create our partitions manually, the option to select is Something else.

Selecting Something else and clicking Continue should take you to the installer’s Advanced Partitioning Tool’s window.

This is the Advanced Partitioning Tool’s window. On a system with existing partitions, there should a listing of those partitions here. If that’s the case with your system, delete them. If you have another OS that you wish to dual-boot with Ubuntu or Linux Mint, then make sure that you have free space sufficient for installing either distribution. Since the system I used has a brand new disk, it is first necessary to create a partition table before partitions can be created from it. To do that, select the disk as shown and click on the New Partition Table button.

Now that a partition table has been created, select the free space and click on the + button. That should open the partition creation window.

And this is what that window looks like. For a standalone installation, the most important options to change here, are Size, Use as, and Mount point.

For the first partition, which will be for the boot partition, I chose to use the same value for Size and “Use as” that is assigned to it by the automated installer. And the “Mount point” is, of course, /boot. OK.

Back to the main window, select the free space, then click on the + button to create the next partition.




Also ran into the broken support for crypted disks when trying to install Gnome Ubuntu 14.04 next to Windows. Having to type my high entropy disk crypto passwords multiple times is not an acceptable option to me.
So I used the steps below to get all my partitions into a single crypto container.
—-
Follow guide upto the point where you created 1 encrypted volume.
Then push the back button to leave the partitioning tool.
Goto the shell ([ctrl]+[alt]+F1) and execute the following commands
Create LVM volume groups:
# sudo -s
# vgcreate gnome /dev/disk/by-id/dm-name-sda5_crypt
# lvcreate -L 2G -n swap gnome
# lvcreate -L 20G -n root gnome
(next command assigns remaining space to home partition)
# lvcreate -l 100%FREE -n home gnome
# lvs
Switch back to the installer([ctrl]+[alt]+F7)
select “something else” again and “continue”.
Once the tool is done rescanning you should now see the new devices(if not go back and forth again).
Reconfigure the /boot partition as done earlier.
Continue with the guide/installation, upto the point it asks for a reboot.
DON’t reboot yet.
Switch back to the console.
Create crypttab:
# blkid /dev/sda5
# echo ‘sda5_crypt UUID=(uuid from prev cmd without quotes) none luks’ > /target/etc/crypttab
Regenerate initramfs and grub config
# mount -t proc proc /target/proc/
# mount –rbind /sys sys/
# mount –rbind /dev /target/dev/
# chroot /target
# update-initramfs -u
# update-grub2
# exit
Now reboot, and you should be able to boot into you’re newly installed Ubuntu.
(note: if booting hangs with a black screen, press [esc])
Hey
when i type: vgcreate gnome /dev/disk/by-id/dm-name-sda5_crypt i get an error.
The error is: please enter a physical volume path.
I need to encrypt my whole computer (dualboot win+ubuntu) and dont want to type in my encryption password for ubuntu 2 or 3 times…
I use ubuntu mate 14.10
I hope its possible with ubuntu mate.
I cant find an article about it.
Thanks!
Have you verified that sda5_crypt is the device name of your unlocked crypto container?
# dmsetup table
sda5_crypt: 0 512989948 crypt aes-xts-plain64 00000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 0 8:5 4096
The steps above are written for my setup. Other setups(eg. Distro/Distro version/partition setup) might use other names and numbers. I’m sure that with the man pages and some googleing you will figure out how to get this working for your setup.
Thanks!
Now its working. But now i have another problem…
The command: mount –rbind /sys sys/ gets an error.
The error is: mount: mount point sys/ does not exist.
I hope you can help me with this problem too.
Sorry for the questions. 🙂
Oops, forgot something there. Should be:
# mount –rbind /sys /target/sys/
Sorry but still: mount point does not exist…
The solution might be something as simple as creating the directory yourself. If /target exists, try creating /sys under it with:
mkdir /target/sys
Then retry the original mount command. Just a guess, but nothing breaks if it doesn’t work.
Hey,
after a new try everything works just fine.
Thanks for the post and your help.
Cool.
Thank you David – your instruction helped me to properly encrypt my disk with three partitions! Linux Lite 3.4.
David, you are a life saver! Tried this procedure with Mint 20.1 and, a few ajustments (device names, etc.), it worked like a charm.
Thanks a lot.
Regards,
Luis
thank you for this post!
just to make the boot faster, is there a way to type the encryption password just once? (even for the prize of having the same password for all separate partitions)
thanks!
support for good LVM and disk encryption setup in the current installer is not that good, so, no, that’s not possible at this time.
Note that in this situation, having the same password for all partitions is ok.
These steps no longer work under 14.04. I’ll list some details below. Can you provide any guidance on how to do a similar setup with 14.04?
Details:
I’ve been building similar test systems under 13.10 for months now, and they have all booted sucessfully. However, with 14.04 I’ve found that none of the systems will boot. I’ve built the systems the exact way I have before (identical to these instructions). When booting, I never get as far as being prompted for a pass-phrase. I get the initramfs prompt after the boot sequence times out. One thing I’ve noticed, is that dm_crypt is missing under the module list that I pull from initramfs.
That’s strange. Didn’t know something changed in the installer. Will revisit this asap.
I just installed 2 systems using the same instructions, minus the /home partition. Both booted successfully. One is in a virtual environment (250 GB storage) and the other is on real hardware (320 HDD). Will publish a tutorial using screenshots from one of them in a few hours.
Thanks for this – surely someone cleverer than I could describe how to use initramfs (or similar) so that the passphrase only has to be entered once?
You may need to turn off swap before beginning.
https://bugs.launchpad.net/ubuntu/+source/ubiquity/+bug/1205397
But Swap also has to be encrypted. Otherwise you are not really getting full disk encryption.
I don’t even consider that a bug. That’s the installer just telling you to encrypt the Swap partition.