PRISM and Boundless Informant. Don’t you just love names like that. They have a nice ring to them. But do not be fooled. Those are bad for your privacy and, with time, even worse for a true democracy.
But thank heavens for Free Software and those making them available. With much gratitude to them, here are two Free Software services that can help you deal with PRISM and Boundless Informant. Maybe not completely, but a little something is better than nothing.
1. Tor is a well-known anonymizing service. Many privacy-conscious people already use it. According to the official description:
Tor software’s job is to conceal your identity from your recipient, and to conceal your recipient and your content from observers on your end. By itself, Tor does not protect the actual communications content once it leaves the Tor network. This can make it useful against some forms of metadata analysis, but this also means Tor is best used in combination with other tools.
So while Tor by itself is not a complete solution to the problem that PRISM and Boundless Informant and other mass surveillance programs pose, it’s a very important piece to the solution. Other applications that can help make Tor a more complete solution are: Enigmail, TorBirdy, and HTTPS Everywhere. Read more about Tor and PRISM here.
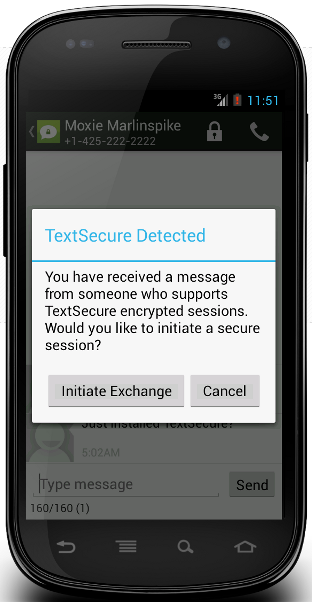
2. Open Whisper is a Free Software project that creates “tools for secure mobile communication and secure mobile storage.” So far, the project has published two Android applications – RedPhone and TextSecure. They are available for download for your Android devices from WhisperSystems.org.
RedPhone is said to provide “end-to-end encryption for your calls, securing your conversations so that nobody can listen in.”

TextSecure is a replacement for the default messaging applications and encrypts messages on the device, that is, locally, and over the air.




Quote “…Those are bad for your privacy and, with time, even worse for a true democracy.”
Democracy is just smoke and mirrors an illusion played out… you do not have it, you just think you do, very much like your freedom – UK, USA, Europe.
Love the Moxie reference 🙂
Sometimes, simply knowing the sender and the receiver, without knowing the contents is enough. It’s unclear, still, if Verizon turned over simply who called whom and when and for how long, basically what’s on everyone’s cell phone bill, or whether Verizon allowed the NSA to record vast quantities of content. Tor doesn’t help for hiding the fact that you sent through Tor, when an agency can track every packet in and out of a Tor server, even if they can’t see the contents. That may be enough to attract attention, and further snooping by the agency involved. For example, the NSA may simply turn over the fact that you used Tor to the DoJ who can charge you with something (see the book “Three Felonies a Day”) simply because you used Tor.
I’m still skeptical about Snowdown’s entire story. He’s obviously got part of it right, the part I already knew and had learned from publicly available sources. I am still not sure he is not exagerating that kernel of truth, and will be skeptical without separate, reliable information. And someone’s friend’s brother-in-law who knows someone who really knows, isn’t reliable. Nor are anonymous posters on the internet.
Snowden did not tell “entire story.” In fact, the guy has not even said a whole lot. He just turned over hard evidence to reliable journalists, who published part of it. And there’s still more to come. So there’s nothing about Snowden that I’m skeptical about.
Isn’t that very scary. Isn’t that part of what Snowden is trying to warn us about.
If using Tor can get you in trouble, what’s next? Https?
Part of the problem is that one of those “reliable journalists” isn’t.
Glenn Greenwald at the Guardian is a notorious jihad-appeaser who wouldn’t fail to excoriate Israel if they found the cure for cancer. (ignore the “religious” issues if you are capable of doing so, and just research how much POSITIVE computer tech advances come from Israel).
As much as I refuse to accept this administration spying on law-abiding American, it’s not hard to assume that part of Greenwald’s exposure is to help his jihadi friends who have been and should be the sole focus of Prism etc.
“Nor are anonymous posters on the internet”
PS – here’s the bottom line. This administration has taken tools designed to be used against American’s foreign and domestic enemies (muslims and marxists) and used them against ALL LAW_ABIDING Americans, concurrently with abusing the IRS to harass those domestic legitimate political groups and media that the Administration fears.
Thats virtually treason, and most certainly falls under high crimes and misdemeanors.
I take issue with 2 things you said.
“American’s foreign and domestic enemies (muslims and marxists)”
Some people (including some in the government) see these as enemies but they are not my enemies.
“This administration has taken tools designed to be used against American’s foreign and domestic enemies”
It’s not only this administration. This extensive spying has been taking place for at least 10 years. The Bush Administartion was also doing it. I am very disappointed in President Obama for continuing it.
“but they are not my enemies”
Then you are a muslim, a marxist, or a moron, because the first two are dedicated to controlling, converting or killing all those who do not follow their path. READ HISTORY.
“It’s not only this administration. This extensive spying has been taking place for at least 10 years. The Bush Administartion was also doing it.”
Yes but they started out doing to to track the muslims and their marxist allies.
” I am very disappointed in President Obama for continuing it.”
Boo-fricking hoo, so you’re another obamunist, no wonder you are ok with jihad and communism.
Is this clear enough for you? William Binney a former senior NSA crypto-mathematician for almost 40 years confirms what Snowdown said:
http://www.democracynow.org/blog/2013/6/10/inside_the_nsas_domestic_surveillance_apparatus_whistleblower_william_binney_speaks_out
It’s clear that the NSA is collecting and storing everyones text messaging such as email. And they are collecting the meta-data for everyones phone calls. Later they can use this data to build a case against anyone. They use computer algorithums to filter the data and find the so-called bad guys.
This kind of power is easily abused. If the government doesn’t like persons political beliefs they can use this system to build a case against them.
thank your for this article, and the one covering full disk encryption. important topics, nowadays. for everyone.
By the way – the name’s “Tor”, not “TOR”: https://www.torproject.org/docs/faq.html.en#WhyCalledTor
Thank you.