Disk encryption is one of those physical security features that determine whether I install a Linux distribution on any computer I use for serious computing. Whether it’s a server, notebook, ultrabook or any other type of *book, if it’s not a crash-and-burn unit, the hard disk drive (HDD) has to be encrypted.
And no, it’s not because I have anything to hide, it’s just that personal data should be just that – personal, and private. If you are not authorized (by the owner) to see it, you don’t.
This becomes especially important in this age of warrantless orders, sational national security letters, and judicial overreach, where a bunch of trigger-happy guys from any government agency can show up at your place and cart everything and anything they can get their paws on.
Take the case of Kim Dotcom, who leaves lives in New Zealand. Back in January 2012, based on charges of copyright infringement related to the Megaupload file-sharing website, the New Zealand police raided his residence and bagged everything they could find. Cloned copies of his HDDs were sent to the FBI in the US of A.
Now, Kim Dotcom is not without blemishes in his character; the guy has a criminal history that dates back to his teenage years. But that’s not the point of discussion here. The gist of this article is what we can learn from the legal aspect of the case against him.
Since the raid of his residence and seizure of his assets, the raid has been deemed, by the courts, to be illegal and the warrant detailing what could be seized too broad. Virtually every single court case has come out in his favor.
In the latest decision, the judge overseeing the case ruled that all digital material taken from his residence that are not relevant to the case should be returned (to Kim). And that any copies of HDDs sent to the FBI be returned.
Too late!
Do you think the US government is going to comply with the decision of a New Zealand judge? Fat chance. Even if they did, don’t you think they’ve already made copies of the copies, and copies of the copies of the copies. And if those HDDs were not encrypted, what good will returning them at this point do.
Again, it’s too late. Lesson? Always encrypt your HDDs. It’s not about who is a good or bad guy, or who has something or nothing to hide. It’s about having the final say on who can have access to your personal data. In cases of this sort, it’s better to be in a position where the authorities are going to court to get you to give up your encryption passphrase(s).
Regarding full disk encryption in the graphical installation programs of Linux and BSD distributions, Anaconda, the Fedora systems installer, the Debian Installer, and PC-BSD‘s installer are the best. Note that the graphical installer of Sabayon is a fork of an older version of Anaconda, but it, too, has support for full disk encryption.

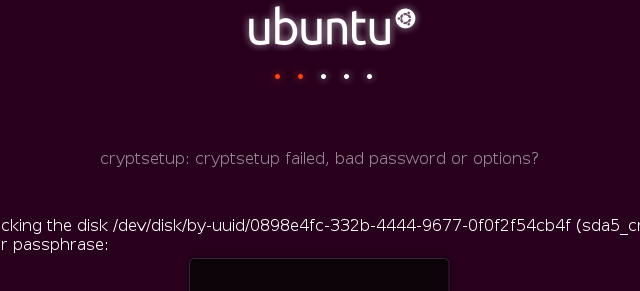


Full disk encryption protects you from the casual opportunistic criminal. It does not protect you from government agencies with budgets that stretch to landing attack helicopters to arrest a guy who “might” be guilty of copyright infringement.
I think we can all agree if a government agency can afford attack helicopters it can afford a few geeks with the tools to crack your passwords.
By all means use full disk encryption to protect against the physical theft of your computer. Don’t pretend it will protect you from the government.
If you live in the UK, you must now give up your passwords on demand. Refusing to do so is a refusal to cooperate with the police in a criminal investigation. Which can be considered a crime in it’s self.
If it were that easy for govt agencies to decrypt an encrypted HDD, they wouldn’t go to the trouble of making it a crime for refusing to disclose the encryption passphrase.
In every single case involving a computer with an encrypted HDD that’s been reported in the US of A, prosecutors have had to go to a judge to force the defendant to disclose the encryption passphrase.
“In every single case involving a computer with
an encrypted HDD that’s been reported in the
US of A, prosecutors have had to go to a judge
to force the defendant to disclose the encryption
passphrase.”
This has more to do with our procedural law here in the US than the other crux of your argument.
Here, government agents are required to get court approval before proceding, thus the establishment of the FISA courts for national security issues and which do NOT report their grants of approval.
In normal criminal cases, evidence obtained without warrant, or which is not otherwise generally and publically available, is not admissable into evidence in court. I assume this is true in most countries, and particularly true of any British commonwealth country.
Secondly, assuming cases of US government malfeasance, the NSA has a huge budget and even non-government players can now crack up to 90% + of 24 character passwords in a matter of hours and with affordable equipment. Imagine the NSA with a flea in its ear.
Still as you and others have said, it is important, for financial and professional safety, to encrypt your data… and make it as tight as you can.
I think that you think that you are too important.
Why would anyone _care_ about your disk’s contents?? What do you think they would expect to find on it?
– Secret letters of the Pope to pretty boys in Argentina?
– GW Bush’s plans on the attack on the WTC?
– Proof of Chinese cyber attacks on the Pentagon?
– Your latest research on transforming human poop to unleaded high-octane gasoline in room temperature?
– 4K porn?
Only three things are important on almost anybody’s disk: passwords, credit card numbers and PINs. Just encrypt these. Or use a specialized tool.
Full disk encryption? Completely, 100% unnecessary.
Why come here and betray your ignorance?
They might not care now, but what about when some future eco-fascist government suddenly decides that eating meat is a crime now (not an impossible scenario in some European countries…the eco-fascists are getting stronger…)
Then suddenly your recipe for grilled steak is an illegal document and you can go to jail for it!
Of course this sounds a bit silly now, but you must not think that everything will always stay the same.
Make it as hard as possible for anybody to get to your private documents. If the government (or anybody else) wants to see some of them, they can always ask nicely, and you can then show them what they want to see.
You shouldn’t make it too easy for them to just take everything they want without asking!
YES. Password for root is just fragile to physical attacks.
If you are living in Turkey, you should definitely encrypt everything. Read the court cases in Turkey like ergenekon, balyoz (sledge hammer). Police may accidently (!) embed evidence into your phone (Mehmet Ali Çelebi’s phone). Or there may be illegal documents in your computer you have never seen before and you can spend years in jail (odatv case).
And of course you should definitely keep a copy of your important documents in else where (Ahmet Şık’s book is destroyed by police without court order.)
I thought Turkey is a “poster-boy” for EU-like democracy and individual freedom. Or has Emir Erdogan got other ideas.
Agree completely! Well said.
paragraph 3: s/sational/national/
paragraph 4: s/leaves/lives/
Freely delete this post when original post is fixed.
Thank you.
Great article! I full agree. What the DOJ did to Kim Dotcom is crazy. Landing attack helicopters in his front lawn, lol?