If Verizon was your Internet Service Provider back in April 2011, you probably received an updated Terms of Service (TOS) spelling out several updates to their TOS. And if you are like most users, you likely did not read it or even if you did, you did not pay particular attention to the details.
Somebody brought it to my attention back then, but I was too busy to do anything with it, though one change did strike me as not kosher. Rather than bore you with what I think of ISPs or other companies that provide needed services, here is the part of Verizon’s updated TOS that should make you go, WTF!
The email itself was sent on the April 18 2011, but the updated TOS, as the email notes, was to go into effect on April 19. Which means that Verizon did not even give their subscribers enough time to read the email. That is usually the first sign that they wanted to pull a fast, which they did, and succeeded.
Ok, the email started like this:
Dear Valued Verizon Customer,
Good news! Below please find the description of changes to the Verizon Online Terms of Service (TOS) effective 4/19/11. In particular, Verizon will send emails regarding your account or TOS changes to your designated Primary Email Address on file. What this means to you is that these updates will now be emailed to the account you have marked as Primary on your My Verizon account profile. This will now make it much easier for you to keep up to date on important account-related updates using your Primary email address.We encourage you to log-in to the Account Profile section at myverizon.com and make sure that you have designated a Primary Email Address. When you do update your Primary Email Address you will receive a confirmation email from Verizon that your email address has been updated. Below you will find information regarding the additional changes to your TOS. We value you as a customer and look forward to continuing to serve you.
Sincerely,
Verizon
That is the nice part. Actually, the whole email was nicely worded, including the part of the TOS that is not so nice. Here is part of the updated TOS that merits special attention:
Effective April 19, 2011 – Important Information Regarding Changes to Your Verizon Online Terms Of Service
…As set forth in Section 3 of the Terms of
Service, your continued use of the Service after the effective date of these changes will constitute your agreement to the changes.
…3. Home Router Password Changes. Section 10.4 was updated to clarify that Verizon may in limited instances modify administrative passwords for home routers in order to safeguard Internet security and our network, the security and privacy of subscriber information, to comply with the law, and/or to provide, upgrade and maintain service. The administrative password for your home router is used to access the administrative controls for the router and to make changes to your router’s internal settings. We will use reasonable means to notify Subscribers whose home router administrative passwords are changed, which may include email notice to your Primary Email Address and/or an announcement on the My Verizon portal.
Note that the email was sent on April 18, with the new TOS set to go into effect a day after. So no time to read it, but you are told that just using the service after that date signals your consent to the updated TOS.
The most interesting part is the one about “Home Router Password Changes.” All routers that I have used usually come with a default username and password. If you have used one yourself, which I am sure you have, if you re reading this, the first thing you did after setting it up is change the default password to something more secure. I have always assumed that once that default password has been changed, that no person other than myself can change it.
Wrong assumption.
Verizon can change that password. In other to do that, they must have a master password, or as it is known in some circles, a backdoor. To Verizon, it is an administrative password. The only problem is their “administrative password” can unlock your administrative password.






They have an administrative port open on the router that you can not turn off that allows them in period. The only way to keep them from signing in to change the passwords which they have done to mine a couple of times it to backup the config which you can do. Set the unit back to factory defaults and login using the default user and password. Restore the config and reset the password. If you want to keep them out all together you have to put an inline firewall and block the port.I believe the port is 4567
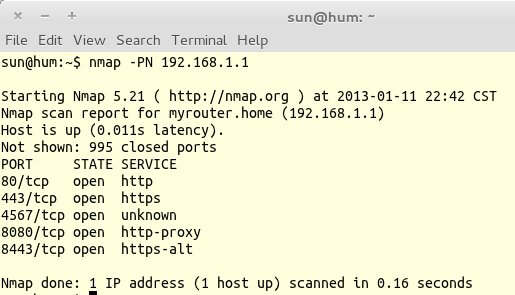
Thank you. So they do have a backdoor. An nmap scan of my router showed the following ports:
80/tcp open http
443/tcp open https
4567/tcp open unknown
8080/tcp open http-proxy
8443/tcp open https-alt
When I did that scan several months ago, I wasn’t sure what 4567 was for, but Wikipedia has it down as a Sinatra default server port.
Time to mess with my FIOS router.
For the longest period of time any form of wireless encryption above 128 bit WEP and MAC filtering were in the support scope of Verizon DSL support. WPA became a request only method about 2 years ago. It’s also within normal scope of support to set the password for the modem to “admin”.
Do you know for a fact that they have a higher priority password?
Because that, especially the “limited instances” part, reads to me like they were using a router that had its factory default password published, some installers weren’t changing it, and this gives them the necessary legal cover to go in and fix it, for those who have never messed with it themselves, thus leaving it at the default.
Of course that’s the favorable (to them) reading, and the terms now allow them to change it for other reasons too, but it does sound like they give you the new password when they change it, which at a minimum, does not necessarily imply they have a master password aka “back door”, to routers where the owner actually /has/ changed the password.
Given the general (IOW, IDR whether VZ has been named as a carrier with the problem or not) coverage of routers often installed without changing the password and with remote access on, thus allowing pretty much anyone on the net to go in and screw with it at their whim, retroactively going in to those where the default works and setting up a non-default password, then notifying the user about it, seems the best policy, but I can easily see the lawyers insisting on covering clause in the TOS.
Further, something like that would need to be carried out with a pretty short notification, because they’re essentially zero-daying themselves. Once the announcement is made, they very likely have literally hours before someone’s exploiting it. So if it were me and there wasn’t a minimum waiting period before the TOS could go into effect, I’d be sending out the notification emails @ 23:59 one day, and starting the password changes at 00:01 the next — two minutes later!
OTOH, if you have evidence of a tiered password system, with them having the master, that’s a different story indeed. But the TOS change alone “ain’t” it, nor is there any indication in your article that you have anything beyond that TOS change.
Verizon ain’t no friend of mine, but overplaying your hand as an opponent doesn’t help, either.
Does this apply just to Verizon-supplied routers, or to all routers?
If the former, it’s easy to avoid by using your own independently sourced router and setting it up with WPA2.
ISP-supplied routers always seem to be a bad financial deal, and the installers tend to set them up with weak, next-to-useless WEP security.