![]() PC-BSD is a desktop-oriented, FreeBSD-based distribution with KDE as the default desktop environment. The version due to be released shortly is PC-BSD 8. Because it the only BSD-based desktop distribution that’s in a position to compete with the best Linux desktop distributions, I’ll be publishing a number of articles over the next few weeks to introduce those not yet familiar with it to some of its management tools. This post takes a look at the graphical firewall manager.
PC-BSD is a desktop-oriented, FreeBSD-based distribution with KDE as the default desktop environment. The version due to be released shortly is PC-BSD 8. Because it the only BSD-based desktop distribution that’s in a position to compete with the best Linux desktop distributions, I’ll be publishing a number of articles over the next few weeks to introduce those not yet familiar with it to some of its management tools. This post takes a look at the graphical firewall manager.
The firewall application on PC-BSD (8) is OpenBSD’s Packet Filter (PF). It is a very powerful firewall application with many advanced features and functionalities. At the command line, the rules are a lot easier to write and understand than Linux’s IPTables/Netfilter. Though simple and intuitive to use, the graphical firewall manager that will ship with PC-BSD 8 only gives you access to a very small subset of the many useful features and functionalities of PF.
Access to the graphical firewall manage is via the Network Connectivity section of System Settings. Double click on it to begin.
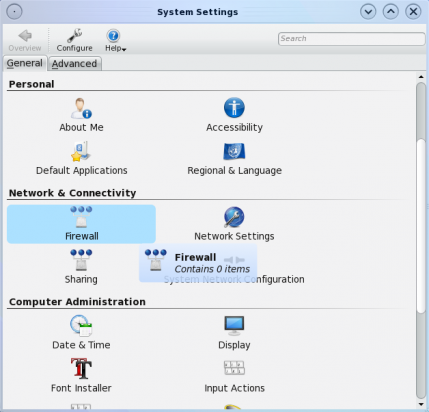
Access to the firewall manager is via the system settings window
Viewing and making changes to the firewall manager requires root access. Click on the “Run in Administrator Mode” button to bring up the password prompt. Type in root’s password at the prompt to be granted full access.
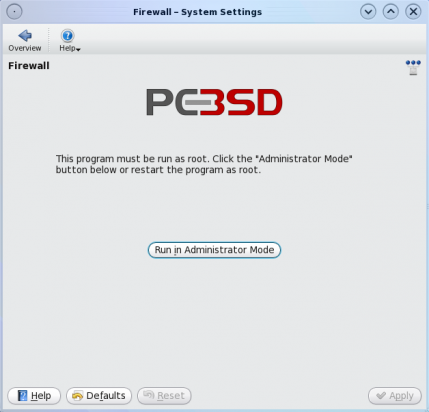
Managing the graphical firewall manager requires root privileges.
This is the default graphical firewall manager’s window. By default, the firewall is enabled and configured straight out of the box. Most users will not need to do anything to use a PC-BSD-powered computer securely and safely on the Internet. The default behavior is to “pass all” on all outgoing traffic and “deny all” on all incoming traffic except those under the “Exceptions” tab. Click on this tab to view the exceptions.
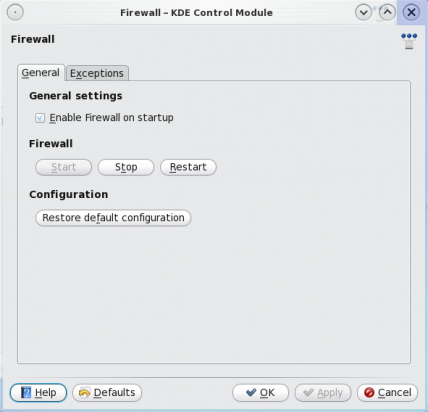
This is the main window of the graphical firewall manager. It is enabled straight out of the box.
The are the exceptions to the default incoming traffic rule. To view the detail of any rule, select it and click on the “Edit entry” button.
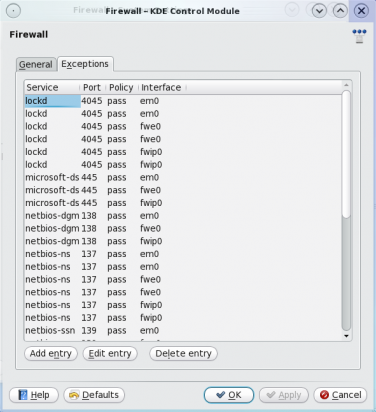
These are the firewall's default rules.
Details of the lockd rule. You’ll notice that the graphical firewall manager only allows you to set very basic rules for any service or protocol. You can see in this example that the rule allows access to lockd from any host or network. The same applies if you want to write an outgoing rule for a service. To see an example of this, click to add a new rule.
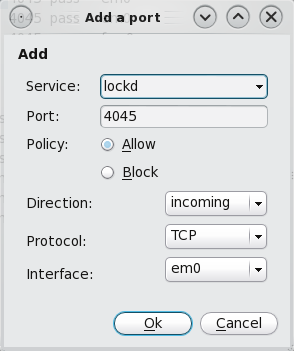
Individual rules may be edited.
Adding a new rule to the ruleset is as easy as choosing a service from the “Service” dropdown list. For this example, let’s use the “ssh” service to add an incoming rule. The default port will be automatically selected. If you are running SSH on a custom port, specify instead. The policy should be “Allow.” The rest are self-explanatory. As said earlier, the graphical firewall manager does not allow you to set more specific or granular rules. This SSH rule, for example, allows SSH connections from anywhere. To set a more specific rule, you may edit this entry in the /etc/pf.conf file or use the pfctl userland utility.
Even for a new user, the rules are pretty easy to understand. A more specific rule for this “ssh” rule could be written as: pass in on em0 inet proto tcp from 192.168.1.15 to 192.168.1.6 port ssh . See, the rules are pretty easy to write and understand, even for non-gurus. You may read more about PF at the Official PF documentation page.
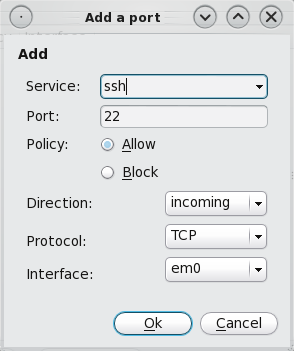
New rule may be added to the list. The list of pre-set protocols is very impressive.




about the comment you made about “the only BSD-based distribution that’s in a position to
compete with the best Linux desktop distributions” I would like for you to know that many people would strongly disagree with you, in fact most people think pc-bsd is the ‘ubuntu’ of the BSD’s. Which isn’t a bad thing but its just a starting off point in which just makes things easier but if you want to really use BSD and not just have it all nice and pre-loaded for you then you would use freebsd, just like you would use debian instead of ubuntu. like this http://xkcd.com/456/ pc-bsd has auto-config issues and you will never avoid those issues.
That statement was actually supposed to have read “the only BSD-based desktop distribution that’s in a position to …”
I don’t think you want to agree with people who that “think pc-bsd is the ‘ubuntu’ of the BSD’s.” The PC-BSD I’m. playing with right now is in many ways better than Ubuntu.