![]() Disk encryption in one of the most overlooked and underused security tools in computing. When most people think about securing a computer or the operating system that powers it, a firewall, anti-virus, and other anti-malware software comes to mind. Those are all good and necessary tools, but they are only concerned with network security. What about physical security? What happens if someone gains unauthorized, physical access to your computer? Even with all the fancy firewall and other network security tools running, If the disk is not encrypted, check mate! Your data is now shared.
Disk encryption in one of the most overlooked and underused security tools in computing. When most people think about securing a computer or the operating system that powers it, a firewall, anti-virus, and other anti-malware software comes to mind. Those are all good and necessary tools, but they are only concerned with network security. What about physical security? What happens if someone gains unauthorized, physical access to your computer? Even with all the fancy firewall and other network security tools running, If the disk is not encrypted, check mate! Your data is now shared.
In Linux, there are kernelspace and userland applications for encrypting partitions and directories. You could opt to configure disk encryption on a running system, but I very much prefer to do that during installation. When encrypting a disk, it is better to encrypt the whole disk rather than just the home directory or the swap space. Very few Linux distributions provide a facility to configure full disk encryption during installation. Fedora is one of those few, and no distro that I’ve used or reviewed makes it as easy and as simple as Fedora’s implementation.
If you are using Fedora, and opt to encrypt the disk, which is highly recommended, you will essentially be setting up encrypted LVM. This is because Fedora uses LVM as the default disk partitioning scheme. This rest of this short tutorial shows you how Fedora implements disk encryption and how that protects your computer if it ever falls into the wrong hands.
When installing Fedora, this is one of the screens you will have to deal with. By default, disk encryption is not enabled. To instruct the installer to encrypt the disk, click on the check box next to “Encrypt system.” Verify the other options and click “Next.”

This is the next screen the installer presents. All it’s asking for here is the passphrase that will be used to encrypt and decrypt the disk. Pick a strong one and one that you will always remember. “Ok.” And that’s how Fedora encrypts your disk. Reboot when the installation is completed.
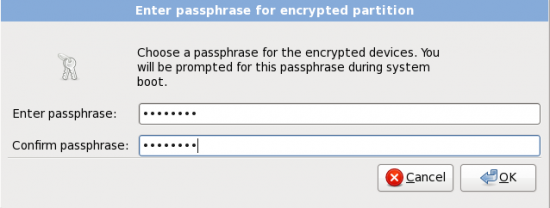
Here the installer requires you to type in the passphrase that will be used to encrypt and decrypt the disk
When you reboot the computer, and before the system partition is read, the system will request for the passphrase. Remember that this passphrase is not the same and should not be the same as the user account you created during installation. It should also not be the same as the root password. The system will continue with the boot process only after the correct passphrase is given.
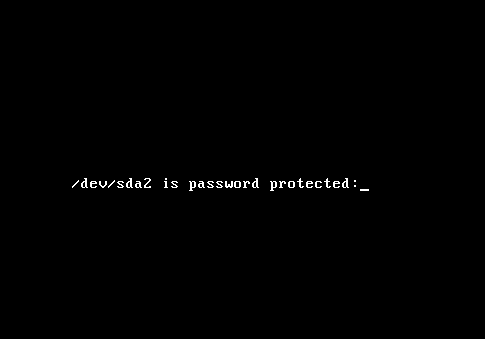
Now the system requests the passphrase before it reads the system partition.
It should be now fairly obvious how this protects your data if your computer is ever lost or stolen. When it comes to disk encryption, think ‘encrypt every computer.’ That is, do not just encrypt your notebook, netbook or other mobile computer that you own. Encrypt even the desktop. While it is not likely that you will forget your desktop at the airport or the local bookstore of coffee store, someone could easily break into your house or apartment and vanish with your desktop computer.
That someone could be a guy or guys from the local police station, the local FBI office or their equivalents in your country. Don’t make it easy for them to access your data. Always encrypt your computer’s disk(s). There’s no downside to it. Use a distro with support for full disk encryption. Fedora is just one. Debian and Mandriva also. To paraphrase the late Johnnie Cochran, If you install, you must encrypt.





When usually people or companies speak of encrypting their hardrive, they are speaking of protecting their data (Company’s secret or very important files with vital information on a person). Occassionly, there are those who wants to encrypt their hardrive for ‘other’ reasons, which could get them in trouble with the government. But for normal use, I don’t see why anyone would encrypt a server which is supposed to be ‘Public’ by default.
Wow. So many assumptions. I don’t even know where to start. What are you on about with regard to governments? Why do common-folk have knee-jerk reactions regarding encryption and that anyone using it must be doing naughty things?
And “public”? Who’s talking about public data here? “Server” does not automatically equal public. There are tons of severs sitting inside corporate, or even private home networks hosting non-public data.
Do you really want some criminal who breaks into your house and steals your computer to have that data?
There is a downside and that’s operator-less rebooting of machines. Think of the server that’s in the basement of your house. While you are away on vacation, the power goes out and stays out for a few hours (Do you have a generator that comes on automatically when the power goes out? I sure don’t). Finally the UPS runs out and the computer is shut down. A while later the power comes back on but the computer gets stuck booting waiting for an operator to enter a passphrase. And it continues to wait, days, until you come home.
Good point, but it’s all about balancing risk and reward.
That said, there is a software that allows remote booting of such a system. I should take a look at it and do a writeup one of these days.
Hello.
This is really great tool.
I have one questions,
If my pc or notebook is encrypted and use other OS to format my pc.
Encrypted is still protected my pc or notebook being format?
Because these days every main board has reset button on it. Even set it with best password, one button bye bye passwords.
Therefore Encrypted is still protect pc device even with format HDD…
Is there any other software can protect pc from even format it?
Please give me advice.
Thank you
Do u know debian base distro (not pure Debian) with disk encryption option during install ?
The only one I know is Ubuntu/Kubuntu Desktop Alternate Installer. See this link for a tutorial based on the Ubuntu edition:
just thought that i would mention if you are paranoid about the fbi or government taking your data, you should wear a tinfoil hat every time you enter you passphrase
I’m using FC14 and passed this option up on install. Now I am installed, is there a way to encrypt my install?
If you are thinking about encrypting a disk after installation, I do not think it can be done – easily. Full disk encryption of the disk you are installing into is something that must done during installation, not after.
If some one has a method of doing it after installation, I’d like to know about it.
If you customized the default LVM configuration as detailed at http://www.linuxbsdos.com/2010/11/03/fedora-14-installation-guide/, you can protect your home folder if you create a new logical volume, copy over contents of your current home folder to the new logical volume, delete the old one, and you have an encrypted logical volume.
It does not offer the same benefits as full disk encryption, but it is better than nothing. The best and easiest solution is to reinstall and do it the right way.
I do not use LVM partitioning scheme, and I encrypt all the partitions with the exception of the /boot partition. Is this habit dangerous?
I don’t see any problem with your set up. The key thing is to encrypt, and not whether you use LVM or the traditional disk partitioning scheme. LVM just makes it easier to manage your drive(s).
It’s also important to note, that on current computers, there is no recognizable performance hit when using disk encryption, for 128 bit AES anyway. Been using it a couple of years now.
And I’m still wondering why the other major distros make it such a hassle to set it up really. So I’ll definitely check out Fedora for my next reinstall. (Hope it also supports btrfs/compressed disks, for netbook performance.)
No major distro supports btrfs as at the last release cycle. I think by the next release cycle, you’ll start seeing btrfs support in a few of them. I hope you are aware that btrfs is not fully production ready.
“there is no recognizable performance hit when using disk encryption, for 128 bit AES anyway.”
That has always been my worry…slow performance. But if things have improved, I’ll definitely give it a whirl. I’d probably use a 256 bit AES key instead of 128.