If you have never heard of or used John the Ripper, then you most likely have not heard of or used Johnny either. So, what, or who, is Johnny? Well, Johnny is not a who, more like a what.
What Johnny is, is a graphical interface to John the Ripper, which is a very powerful and cross-platform password cracking tool that you probably have installed in your favorite Linux or BSD distribution, or other UNIX-like operating system. Johnny just takes what used to be a command line task and provides a user-friendly interface to it.
If you have some free time, it is a very good tool with which to crack passwords in a password file that you have legal access to, for example, the /etc/shadow file from your Linux installation.
Just like John the Ripper, there is nothing really fancy about Johnny. It just does its job very easily and very well, too. All it needs is a password file to crack. Here are a few screen shots of Johnny:
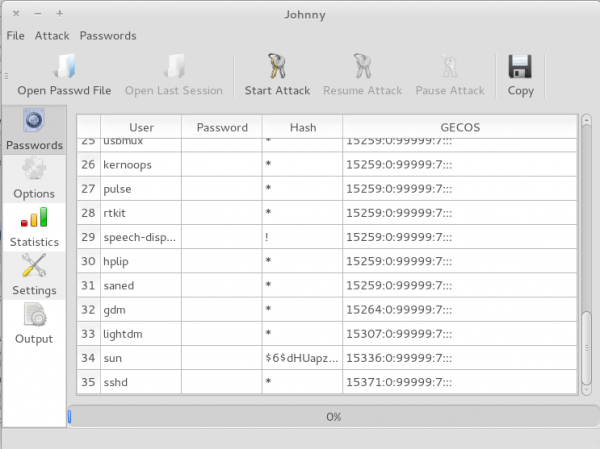
This screen shot shows with a password file ready to crack.

Just a few seconds later, Johnny is done, and password is cracked. The cracked password file is from a test installation of a Linux distribution.

Johnny’s settings.

If Johnny is not in the repository of your favorite distribution, binaries and source code are available from here.



why are the two first screenshots same?
Corrected. Can you tell the difference?
Yeah, nice game 🙂
now the password that cracked is shown: sun123
I pay attention to that ’cause I translate plenty of this website’s articles in my native language and I really like it.
thanks…