ROSA Desktop Fresh R4 is the latest edition of the bleeding-edge edition of ROSA Desktop, a Linux desktop distribution from ROSA Laboratory, a Linux software solutions provider based in Moscow, Russia.
For new users, it is one of the better designed KDE desktop distributions, with a few features you won’t find on mainstream KDE desktops. However, my experience with this latest release has put a damper on that “better designed” label.
ROSA Desktop Fresh R4 is a major release and comes with the following new features, some of which are experimental and not recommended for those who don’t like bleeding-edge stuff. If, however, you don’t find getting digital grease on your hands, you will find at least one of those experimental features a fun toy to play with, like:
- ROSA Freeze, which makes it possible to rollback your system to a working state after performing tasks with a potential to break your system
- Pipelight, an experimental version of the Fresh Player Plugin
On the more stable end of things, ROSA Desktop Fresh R4 comes with:
- KDE 4.13.3
- kernel 3.14.15 with support for BFQ I/O scheduler v7r5
- Phonon 4.8
- Nvidia proprietary modules: 340.x, 304.x, 173.x
- Improved support for hybrid Nvidia and Intel graphics
- The usual cast of updated end-user applications, including Firefox 32, LibreOffice 4.3.1, and XBMC 13.2
- Support for installation on computers with UEFI firmware
- And support for encrypting the root partition
It’s that last item – encrypting the root partition – that got my attention, because that’s a feature that’s been missing in the installer of all Mandriva-based distributions that use the old Mandrake/Mandriva installer. Not knowing whether it will work as advertised or not, I decided to test it out. That’s what a review is for, right?
On test installations in a virtual environment, it does not work. Not that anybody will want to encrypt the root partition (or any partition) of a guest OS, but a feature like that should work in any environment. Disk encryption on other distributions that support it works in any environment, virtual or real.
By “it does not work,” that just means that the decryption of an encrypted root partition fails on reboot. This screenshot shows the boot screen with the encryption passphrase specified.

After that, the screen just hangs at that step. But that’s in a virtual environment provided by VirtualBox.

On real hardware things got better, but not in all situations. For example, on a computer with UEFI firware and with UEFI partitions, that is, with a /boot/efi partition, the installer failed to install GRUB, the boot loader. This screenshot shows the GRUB installation step.

The error screen.

And the reason that GRUB installation failed. So it appears that disk encryption does not work if a /boot/efi partition is configured.

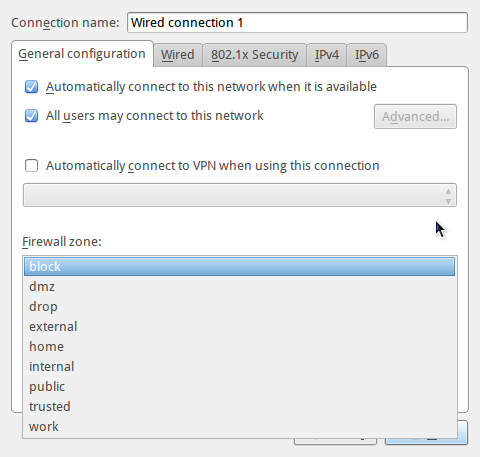
Without a /boot/efi partition, that is, either with plain MBR or GPT partitions, encryption of a root partition works as advertised. I should note that the failed attempts were with partitions that were created manually. That, by the way, is the only means of configuring disk encryption, because the installer does not have a facility to enable encryption when any of the automated disk partitioning option is selected, as shown in this screenshot.

Other than the issue with encryption of the root partition, I had no other problem using the installer. The installer does require plenty of RAM (2 GB recommended) to run smoothly. On a test installation with about 1.2 GB of RAM, the process was so slow that I had to abort it and restart it with more RAM allocated. At about 1.7 GB of RAM, the installer ran normally.

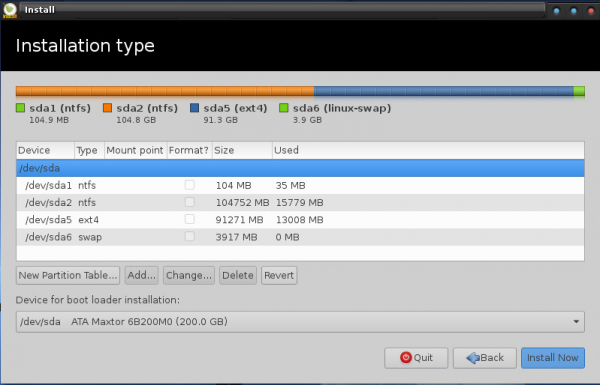
This screenshot shows the default partitions created on a system with UEFI firmware.

And this shows the popular file systems supported by the installer.

Past the installer, almost everything worked as expected. “Almost,” because there’s a major problem with the firewall application (more on that further down). This screenshot shows the login screen. It’s football season, right?




Is that distro stable enough to stay at daily using?
Yes. The latest version is ROsA R6.
Rosa Fresh R4 announced itself more than 2 years ago, so that’s not the version number you’re looking for (and then, the free version would not actually boot for some arch., and that the version was ‘Fresh!’ ran.) Now per http://wiki.rosalab.ru/en/index.php/ROSA_Desktop_Fresh_R4_Release_Notes it’s based on rosa2014.1 and will be maintained 2 years (and comes in i586 and x86_64) and has notes for old machine suitability. I rather imagine a Russian runthrough would make better reviews? Also, encrypted boot would necessarily be UEFI or at least TCP, typically done in those contexts, otherwise there’s no BIOS key mechanism…something not much made out in the review.
That wiki’s handily in English now though, so friendlier than it was. How’d it perform otherwise? Patches patching? Sources sourcing? Your OpenCL stuff ran like a colt?
How did “Rosa Fresh R4” announce “itself more than 2 years ago” when the Official release annuncement is dated “08 октября 2014”?