Building and deploying secure web applications is a full stack effort. This guide focuses on the server side end of things for a web application in your scripting language of choice. Typically this involves: reducing attack surfaces, keeping everything up to date, and sticking to the principle of least privilege.
This isn’t surprising or new – and in fact operating systems have security oriented capabilities and tools baked in – but the introduction of containers makes it possible to benefit from these tools in a mostly automated zero-configuration way. A tool that is too hard to configure or is too inaccessible ends up not getting used at all. The ability to automate the tedious or error prone tasks results in an application that is more secure.
This guide will be using a sample node.js application and a real vulnerability in one of its dependencies to make everything a bit more concrete.
Leveraging OS built-in security features
Linux has all of the building blocks necessary to lock down applications: file permissions, SELinux / AppArmor / seccomp. Docker even provides default profiles for AppArmor and seccomp. This should help us with the principle of least privilege but unfortunately those tools aren’t pleasant to work with.
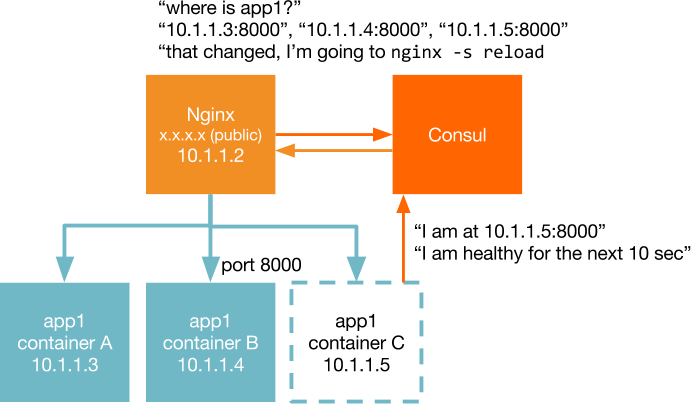
Fortunately we can find out a lot about our application when it is properly containerized. Continue reading…