So for the past three months I’ve been using Tor Browser to surf the Web, not as a primary browser, but as a secondary browser. Firefox is my primary browser.
Together with using StartPage as my search engine, I feel much better about my privacy while surfing the Internet. Using Tor Browser leads to a tad slower browsing experience, but I knew that going in, so no complaints there.
So what did I learn from these past few months of using Tor Browser?
First: That some website’s will attempt to extract HTML5 canvas image data that can be used to uniquely identify my computer – even if they are disallowed from setting cookies. And it’s not just the “bad” sites. Reputable news organizations like The Guardian will attempt to.

Figure 1: Warning about site trying to extract html5 canvas image data.
Et tu, GitHub?

Figure 2: Warning about GitHub attempting to extract HTML5 canvas image data.
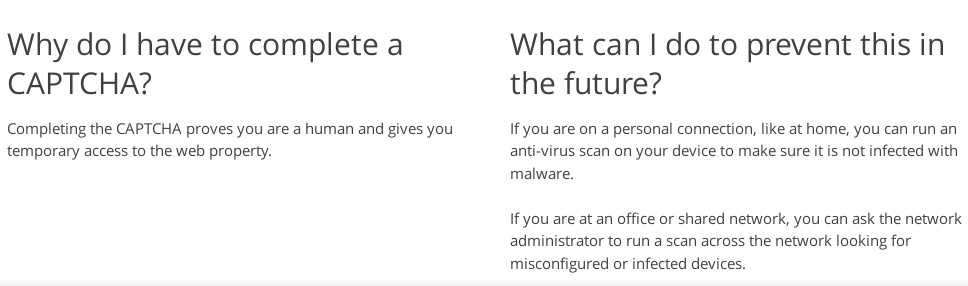
Second: Some websites can’t tell if I’m human or not, so they ask me to prove it by jumping though a reCAPTCHA loop. Am I legit?

Figure 3: Hacker News asking me to prove if I’m legit.
Some will go a step further and tell you what you can do to prevent being asked to jump through a reCAPTCHA barrier in the future.

Figure 4: What I can do to prevent getting a reCAPTCHA.
Note that Tor Browser is a patched version of Firefox, but these are things I’ve never encountered while using plain-vanilla Firefox or even Chromium. I wonder what other tricks these website’s try to pull when you’re not using Tor Browser. For more on HTML5 canvas image data and other features in Tor Browser, visit Fingerprinting defenses in the Tor Browser.





This homepage also attempt to extract HTML5 canvas image data.
I’m browsing right now with Tor, and I got that warning visiting this article.
Hey,
Interesting post. I am so lost, what is this Hola VPN and isn’t Google doing good by trying to block access by it?
Don’t forget WebRTC is leaking your IP.
Most web sites are just vacuum cleaners sucking up as much of your data as your software allows. If you run Ghostery you will be amazed at the number of trackers. What’s also interesting is if you block trackers and then go back to the web site at some later time, a new tracker sometimes shows up. Are they rotating them to try to bypass the blocking ? Probably.
I don’t care what the site is, they’re all about the data., the data, not the push but the pull.