A recent article titled Emergency Self Destruction of LUKS in Kali revealed an ongoing attempt to add a “nuke” option to cryptsetup, the utulity used to manage disk encryption.
The idea is very simple. But before I get to the gist of the article, here’s how setting up full disk encryption protects your data from authorized unauthorized access. When a disk is encrypted, a passphrase is specified at setup time. That passphrase will have to be specified at boot time before the OS installed on the disk can boot (properly). If the correct passphrase is not specified, your data remains where it is – encrypted and secure, safe from unauthorized access.
It’s a physical security feature that works to your advantage until you forget or misplace the encryption passphrase. Unless you have a friend or relative at a secretive government agency, you might as well throw the HDD away. This feature ranks number 1 on the list of physical security features you can use to protect sensitive data.
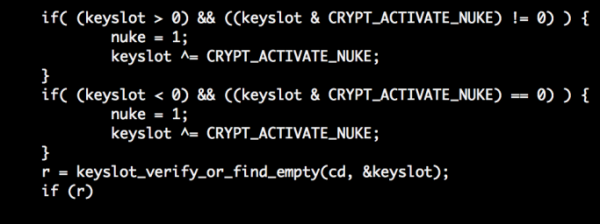
The “nuke” option that the developers of Kali Linux are cooking up is designed to let you specify a passphrase that will destroy saved keys thereby rendering data on the target disk inaccessible. As described in the original post (See Emergency Self Destruction of LUKS in Kali):
On any subsequent reboots, you will be asked for the LUKS decryption password each time as usual. If for whatever reason, you were to enter the nuke password, the saved keys would be purged rendering the data inaccessible.

But why would you want to nuke your encrypted hard disk and in the process lose your data – forever? The authors of the article and the patch did not speculate on the reason(s) one might want to “nuke” an encryption disk, but here’s one occasion where that nuke passphrase might come in handy: Say your computer is confiscated by law enforcement authorities and you refuse to hand over the encryption passphrase. You can maintain that stance until a judge says give in or go to jail. Since I’m sure you don’t like the idea of spending time in jail and you also want to keep your data from those guys, you could, if you have one configured, give them the nuke passphrase.
I think I like the “nuke” idea and would love to see the patch in the official cryptsetup utility. If you do, let the developers know by voting in a poll set up here.
UPDATE: Kali Linux 1.0.6 has just been released. And it comes with the “nuclear option” integrated in cryptsetup. See Kali Linux 1.0.6 released. Cryptsetup has “nuclear option” integrated.



after reading the kali linux documentation, this ‘nuke’ feature is badly implemented: https://www.kali.org/tutorials/nuke-kali-linux-luks/
“it is possible to backup your keyslots beforehand and restore them after the fact.”
“‘restore’ them to the machines once back in a safe location.”
‘nuking’ is useless if it just ‘nukes’ the password but leaves the data behind to be ‘restored’ ‘in a safe location’
If your disk is confiscated, it’s already to late –
digital forensic always work on copied data!
There’s only one use case:
If cops knocking on your door, nuke it …
“digital forensic always work on copied data!”
Even if the disk is encrypted??
>Even if the disk is encrypted??
Sure – raw disc image are made for several reason –
one is independent expert witness
Even if the disk is encrypted??
no. the best the bad guys could do is make an image of your encrypted disk. use strong aes-plain-xts with a 512 byte sha hash. if the bad guys could read your encrypted partitions, they wouldnt need the key.
i think a nuke option could be bad if done wrong. if it can be shown you deliberately nuked a disk, you could still face the consequences. the nuke option needs to quietly overwrite the disk with random data or gibberish which is impossible if the image is burnt onto a dvd. perhaps 2 keys is the best option. the second key further encrypts as the data is written. if you offer a key to the bad guys and it would unencrypt 1 level and still be random data. make it so both keys have to be used to get the real data. also make it indeterminate how many keys exist. frankly, advertising a nuke option is not very wise. every forum on the internet is archived and scanned. not much of a secret.
Using “authorized” instead of “unauthorized” is an obvious error, and thanks for pointing it out. It has been corrected.
Like @Frodo said, you don’t seem to know the difference between physical and network security.
If encryption is not a physical measure, what is it?
You obviously don’t know the difference between physical and network security.
This article is poorly written. It should read ‘unauthorized’ in “… full disk encryption protects your data from -> authorized <- access."
Secondly, encryption is not a 'physical' security measure, which implies it's not possible by laws of nature to access the data. This is simply incorrect. Any means of encoding information that requires a key or passphrase to decode the information is protected by statistical, thus mathematical, laws that have nothing to do with the physical world.
It is true that the information itself is converted into another format and is stored onto the drive in such a way. This does not mean that the security measure is a physical one, like an actual door lock, it rather means that it's extremely hard to interpret the data without the key.