At a time when your ISP is tracking your online activities, sites you visit are doing the same (even the one you do not visit are able to track you), Google is not to be left out in the game, and the NSA is tracking everybody else, it’s easy to be depressed.
What exactly don’t these guys know about you? Or what can’t they know about you? For most people, the shocking answer, is not much. You see, privacy died about 10 years ago. There are things you can do to regain some semblance of privacy in your life, but with the wide variety of ways used to track you, only the most paranoid and tech-savvy has the skills to put up a good fight.
But while most of us can’t do very much, we can at least have fun tracking who’s tracking us, as we surf the Internet. If you use Firefox Web browser, an extension called Collusion can help you see which websites are tracking you. Install it like you would install any other Firefox add-on.
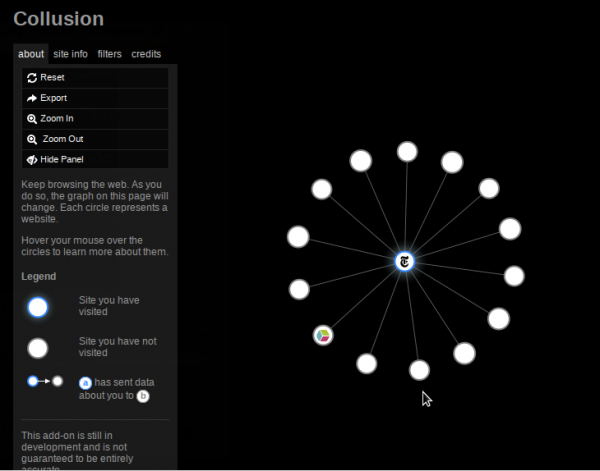
Once installed, you can access the graph by clicking on its icon in the bottom-right of the browser window, or from the menu – Tools -> Collusion Graph. This image shows all the websites that are able to track me when I visited the nytimes.com. That’s just one site I visited and 14 other sites can track me.

Some sites do not cause as many third party tracking as the nytimes.com. For example, visiting nsa.gov only added one more third-party to the mix. Duckduckgo.com, my preferred search engine, does not add any extra spy, other than its own cookie. I don’t even want to tell you what happened when I visited my own site. Ridiculous!

Just as I was about to press the publish button, I decided to see what happens if I disallow any type of cookies – first-party or third-party, from being set on my browser. There was no difference. I don’t know how they do it, but Collusion’s graph still read the same, as when cookies were allowed.





I did an extension search in Iceweasel, but couldn’t find it, so I downloaded the latest Firefox and it can’t find it either.
If it existed, I’d be quite interested to try it.
Just clicking on its link in the article takes you to the extensions page. And on a search of “collusion,” it was the first item returned.
Thanks for the prompt and helpful advice. I’ve found my problem. I originally read your article in Chromium, then loaded Firefox and looked for it in the Extensions. It failed to appear.
With your advice, I loaded your article directly in Firefox and clicked the link. As you said, it came up on the Add-ons page, but there’s a message that it isn’t available for version 17.0.7 – which is what I have.
I think I’ll just have to wait for a bit.
Lets not forget about Tor browser bundle. A bundled package of software that is free and uses the latest “do not track me” technology.
Everyone can check it out here.
https://www.torproject.org/projects/torbrowser.html.en
very cool.
I opened http://www.askjeeves.com and saw a bigger web that nytimes.com 😀
Instead of dis-allowing cookies, try using a privacy plugin like Ghostery. Before installing, Linux Today informed 14 sites. After installing ( and resetting Collusion report), it only informed 7 sites.
Good to see a visual that ghostery is doing what it is supposed to do.
Ghostery is bought and paid for by corporations that are looking for and watching web site traffic. Take a read of this.. http://venturebeat.com/2012/07/31/ghostery-a-web-tracking-blocker-that-actually-helps-the-ad-industry/
As always, do your own research but, I personally do not use ghostery any longer. I only use TOR now.
Try the RequestPolicy extension. IIRC, I actually found it recommended on an earlier discussion of collusion. Eventually, I ended up uninstalling collusion as there simply wasn’t much left for it to report — the only sites it listed were sites I already knew about as I had specifically allowed them in RequestPolicy.
Of course, that /does/ come with a non-trivial amount of hassle-cost, especially at first, until you’ve set normal permissions for all the sites you normally visit, and especially for images and scripts, because one thing you find out real fast with this extension is just how many sites link to off-site images as well as off-site scripts. But it does get better. After a couple days you’ll notice less hassle on the sites you visit nearly daily, and after a week or two, you’ll find most of the permissions you’re setting are now one-shot/temporary, as you don’t visit the site (or your favorites sites don’t link to a site) often enough to make it worth setting a permanent permission for.
The one thing I wish RequestPolicy had was something like Noscript’s untrusted sites list, to take them off of the list that appears all the time. Google-analytics, the big ad-networks and the social sites (twitter, facebook, reddit, stumbleupon, dig, del.icio.us, etc) all end up on noscript’s untrusted list, but request-policy doesn’t have such a list, so they continue to show up in candidate list and I have to continuously ignore them.
The other thing that would be nice would be no-script integration, such that allowing a site in no-script would auto-allow it in request-policy as well, instead of having to allow it twice, once in each, since allowing a script in no-script doesn’t help if request-policy is blocking the request for the script in the first place. (But allowing in request-policy wouldn’t allow in no-script, as someone could well want to unblock image serves, for instance, without allowing scripts from the same site to run.)
But there’s a bonus, too. With a nicely setup RequestPolicy, the need for an ad-blocker pretty much disappears, since very /very/ few sites serve their own ads, meaning the ad-sites all appear in RequestPolicy, and if you don’t allow the requests…
And without a half-dozen or more additional sites to load content from, web pages load much faster, too. =:^)
Duncan
The RequestPolicy info page, the recommendation is to use it and NoScript together, so the coders of RequestPolicy know the limitations of their extension.
I’ll install it and see how it goes.