Summary: Fedora 19 review presents a detailed review of the latest edition of Fedora, a Linux distribution sponsored by Red Hat, Inc. Out of the box, it ships with only Free Software applications.
Like previous releases before it, Fedora 19, code-named Schrodinger’s Cat, comes with many, many new features and feature enhancements, and, of course, its own share of bugs.
Installation images are available as Live CD/DVD ISO images. The main edition uses the GNOME 3 desktop environment, with an unmodified GNOME Shell. Installation images for other popular desktop environments are also available for download. These other flavors, known as Spins, run the KDE, LXDE, Xfce, and MATE Compiz desktops.
There are also specialty flavors designed for specific computing tasks (Design-suite, Electronic-Lab, Games, Jam-KDE – for the musician in you, Robotics, Security, and SoaS), and ready-to-run images for Cloud platforms. Installation images for ARM, PPC, and s390 architectures are also available.
This review is based on test installations of the main edition and the KDE Spin on real hardware and in a virtual environment powered by VirtualBox. I usually like to begin a review from the installer, but for Fedora 19, I’ll leave for somewhere towards the end. The following list shows the topics I’ll touch on in this review, starting with features common to the main edition and all the Spins.
Here are the list of features that interest me:
- Network upgrade of existing installations
- Automatic bug reporting tool
- Firewalld Rich Language
- SELinux
- 3D printing
- Anaconda
- GNOME 3 Edition
- KDE Spin
- Graphical Package Manager(s)
1. Network upgrade of existing installations: Before Fedora 18, upgrading an existing installation of Fedora was not very user-friendly. That changed with the introduction of an upgrade tool called FedUp (FEDora UPgrader). In this latest release, another upgrade script called fedora-upgrade was stable enough to be included. So the first thing I did when Schrodinger’s Cat was released, was attempt an upgrade of two existing installations of Fedora 18 using both tools. Aside from a minor problem with the default GRUB theme files, both scripts worked as advertised, though my preference would be to use FedUp, as it can be run unattended.
I documented my experience with both scripts at Upgrade Fedora 18 to 19 using fedora-upgrade or FedUp. In the future, I think most distributions not using a rolling-release development model will be using upgrade tools similar to FedUp or fedora-upgrade.
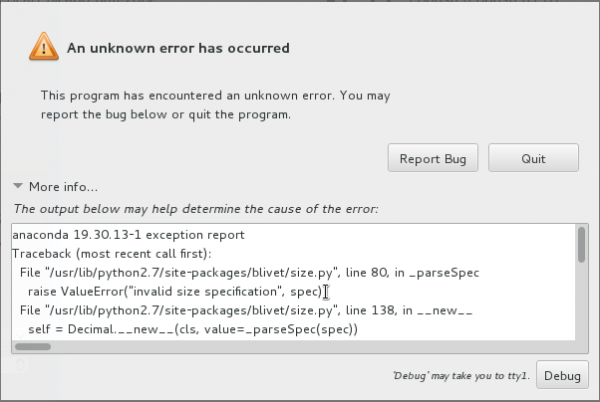
2. Automatic bug reporting tool: Bugs happen and applications will crash. The question is, does your favorite distribution make it easy to file a bug report? For Fedora (19), the answer to that question is a yes. While attempting several test installations, Anaconda, the Fedora system installer, managed to crash on three separate occasions. Even at that stage, an automatic bug reporting tool was launched. This image shows one of the generated bug reports.

Two options for reporting/saving the bug report were presented – one to the Red Hat Bugzilla website, the other to another local or remote server.

Since I did not have a Red Hat Bugzilla account, I chose to upload the report via scp (secure copy client of OpenSSH server) to another computer on my network, where it currently sits as a compressed tar file. The automatic bug reporting tool, abrt, works just as well on a running system. Ubuntu Desktop also has a bug reporting tool, though I don’t think it works during the installation process. Linux Mint, a popular distribution based on Ubuntu Desktop, does not even have a bug reporting application installed.

3. Firewalld Rich Language: Firewalld is the new (starting with Fedora 18) firewall application for Fedora. It is made up of a daemon that goes by the same name, a graphical interface called firewall-config, and an applet called firewall-applet. Before this latest release, it had the same shortcoming as the previous firewall application – creating granular or complex firewall rules was not for newbies. With the introduction of Firewalld Rich Language, that process is a little bit less intimidating. It is an attempt to make creating granular firewall rules as user-friendly as OpenBSD’s pf (Packet Filter), which is about the best there is.
So now you can write firewall rules of this sort: <strong>firewall-cmd --add-rich-rule='rule family="ipv4" source address="192.168.1.11" accept'</strong>. Before Firewalld Rich Language, rules like that could only be created using an IPTables syntax that could easily scare non-techies. By the time Fedora 20 is released, it should be possible to create such rules from a graphical interface, likely incorporated into firewall-config. This image shows the entries in the context menu of firewall-applet.

Firewalld and its graphical interface are installed by default in Fedora 19, but the applet is not. While I was able to install it (the applet) on test installations of both the main edition and the KDE Spin, it failed to launch on the main edition, from the menu or the command-line, without a feedback error message, and no clues in /var/log/messages or /var/log/firewalld. I had no problem starting it on the KDE Spin. I have to assume that the reason firewall-applet is not installed by default is because it has an unresolved bug.
Aside from being able to create rich-language or granular or complex rules from firewall-config, another feature I’ll love to see added to its main window is a statistics tab.

Firewalld introduced the concept of network zones, which define trust levels for network connections and interfaces. Several network zones are pre-configured out of the box. In the KDE Spin, you can change the firewall zone for an interface from the NetworkManager setting. That is not possible from the NetworkManager window of the GNOME Shell. In the Cinnamon Desktop Environment, it is also possible to assign a firewall zone to an interface from its network settings window. However, that is not possible when you install the Cinnamon desktop on an existing installation of Fedora 19 GNOME, because the network settings manager is the same as that of the GNOME Shell.

Firewalld has been ported to Ubuntu, though Ufw, the Uncomplicated FireWall, is still the default firewall application on that distribution. Like on the main edition of Fedora 19, I was able to install firewall-applet on Ubuntu 13.04, but it failed to start, though it worked just fine in Linux Mint 15 Cinnamon and Linux Deepin 12.12, two distributions based on Ubuntu. (See How to replace Ufw with Firewalld in Linux Mint 15 and How to customize Linux Deepin 12.12.)
Firewalld is the type of application that exposes and makes it easy to use the powerful features of Linux to all users. We need more applications like it.
4. SELinux: SELinux is one of three mandatory access control or application-level firewall tools available in Linux. The others are Tomoyo and AppArmor. On the desktop and even on server installations, SELinux used to be a royal pain, so much so that the most commonly recommended method of dealing with it, was disabling it. Starting from Fedora 18, it has become less of a headache to use. I’ve been using an installation of Fedora 18 KDE exclusively since it was released, and I’ve not had any problems with SELinux.
With the SELinux Policy Generation Tool, generating a policy for an application of user is a point and click affair, provided you understand the SELinux concept.

Like Firewalld, SELinux has a graphical management interface, so dropping to the command-line to use its dozen or more command-line clients should not be necessary. The main interface of the SELinux Administration tool is shown below. Even with a graphical management interface of this sort, you need to have a fundamental understanding of how SELinux works before you start messing with it. Visit the official SELinux project here for documentation and usage guides.

With its many modules, SELinux, even from the graphical interface, can be too much of a good thing for those new to Linux. But if you are willing to spend some time learning how it works, it can be an invaluable tool for boosting the overall security posture of your Fedora (19) installation.





Cinnamon… my problems with Gnome are now solved.
FedUp tool was introduced since Fedora 18 to upgrade your system, but it will work with Fedora 17. For fedora 16 and older verions, to upgrade fedora to newer verion, we used “Preupgrade”
Before you do anything, **backup** your important data first to external hard drive, usb disk or to any another machine.
# yum install fedup -y
# yum update
# reboot
After your system rebooted, run
# fedup-cli –reboot –network 19
source: http://namhuy.net/1358/upgrade-fedora-18-to-19.html
“2. Automatic bug reporting tool”
This isn’t new in F19, not remotely – we’ve had automated crash submission from the installer since, man, I think at least since F12 when I started on Fedora.
“In the KDE Spin, you can change the firewall zone for an interface from the NetworkManager setting. That is not possible from the NetworkManager window of the GNOME Shell.”
Yes, it is. Select the connection, hit the ‘properties’ button (that cog icon at bottom right), click Identity, there’s a ‘Firewall Zone’ drop-down right there.
“So given that the third attempt was successful, I can say with some degree of confidence that Anaconda has a nasty but at the step of the installation process shown in the image below.”
That’s odd: I haven’t seen a single crash there and I’ve run thousands of F19 installs. But then, I don’t use the resize function much (personally I’d rather resize a partition prior to an installation attempt; partition resizing is just a finicky thing to deal with). Perhaps it can crash if you happen to try and set the root password while the resize operation is in place? I’m not sure why that would happen, but it’s all I can think of. It would certainly help if you’d file bug reports for the crashes: we have no chance of fixing them without reports (containing all that data the bug reporting tool provided).
“Though Anaconda has most or all advanced features in place, a few basic ones, like being able to specify a bootloader password and install the bootloader to a location other than the Master Boot Record (MBR), is not in place.”
The second is an intentional choice, not a ‘missing feature’: https://bugzilla.redhat.com/show_bug.cgi?id=872826 . The first is possible via kickstart, I don’t know if it’s intentional or an oversight that it is not available through the GUI.
“One thing I fail to understand about the GNOME Shell, is why the Suspend option is not in the User Menu or why it’s not listed in the shutdown options window. Instead, the developers decided that the place location for it is on the login screen. So if you are logged into the system and wish to put the computer in Suspend mode, you have to first logout of the system. Bad implementation!”
Hold down alt, and Power Off turns into Suspend. If you recall, back around 3.0 – 3.4, there was no Power Off option, only Suspend, and people bitched so much about that it was changed: you could hold down alt to turn Suspend into Power Off. I think in 3.6 it was flipped so it’s Power Off by default and you hold alt to turn it into Suspend.
“I’m not a big user of keyboard shortcuts, which means that to get to the Frequent-ly used application picker view of the GNOME Shell requires two mouse clicks.”
I really, _really_ don’t get why people don’t just use the ‘press start key, type name of thing you want to launch’ method. It is the way the Shell’s designed to work and by far the easiest way to launch anything.
“Fedora 19 GNOME 3 ships with a welcome application or desktop greeter that I think is an attempt to implement a Kaptan-like application for Fedora. Kaptan is a desktop greeter for Pardus, a Turkish Linux distribution. It runs on first boot (or first login) and can be run at any other time.”
I’d never heard of ‘Kaptan’ and I don’t think the GNOME devs had either. gnome-initial-setup is rather a part of the ‘GNOME OS’ effort – https://wiki.gnome.org/GnomeOS/ . GNOME project has this grand vision for a complete vertical stack from the installer to the desktop, of which g-i-s is a part. Note that the ‘ideal’ installer for GNOME OS would be something substantially simpler than anaconda – the GNOME devs would take the account creation bits out of anaconda entirely if given the choice, for instance.
“Compared to Kaptan and Kapudan, Fedora’s desktop greeter is very basic. All it allows you to do is change input sources and configure online accounts.”
It actually lets you set your language as well, and configure a wireless network if that’s necessary. And set some date/time options.
“The Fedora team might want to consider borrowing some features from Kaptan and Kapudan.”
g-i-s is a GNOME component, not a Fedora component.
““Almost all,” because the startup or auto-start module is missing. I found that in order to configure a program to start automatically at login, I had to drop to the command-line and type gnome-session-properties, then configure the target application from its interface.”
This is intentional (on GNOME’s part): they consider session management deprecated and would rather you just suspend/resume the system instead. They intentionally hid g-s-p from the menus.
“A question I always ask myself whenever I install a Fedora KDE edition is this: Why is Konqueror the default Web browser? I’ve written about this before and it bears repeating here. Konqueror is a powerful application, supporting more protocols than any other (Web browser). but as a dedicated Web browser, it’s terrible.”
The Fedora KDE devs subscribe to the ‘KDE is a complete environment’ philosophy. This kind of choice is entirely up to the team maintaining a given desktop, and that’s what the Fedora KDE devs decided.
“For power-users, holding down the Alt and F2 brings up a very useful utility of the KDE desktop. From this small app that pops up, you can search for local content, online content by specifying “gg” (that’s short for Google), though the Youtube and Wikipedia plugins don’t seem to work, because I could not get results by typing in a search term I now can only be returned from the Internet.”
That’s exactly the intended main interaction method of GNOME’s Overview search which you seem so unwilling to use!
“So like the Linux Mint developers, it seems that whoever is responsible for rolling the main edition of Fedora 19 has a grudge against games”
The teams for each spin choose the package loadout, not any ‘central authority’. The lack of games on the GNOME spin is for a simple and boring reason: lack of space. Check the GNOME spin image size, it’s about 2MB under 1GB, which is its size target. We had to hack a lot of stuff out to keep it under 1GB for F19. Definitely no room for games. I don’t know why the KDE spin doesn’t include more, but honestly, it’s kind of a futile pursuit: it tends to be the case that each person has just one or two little time-waster games they like to play but everyone’s is different, so we can’t ever include all the ones to make everyone happy. Probably just easier you install the one(s) you want yourself.
“Regarding consistency in management applications, especially with respects to the graphical package manager, I think the time is ripe for the Fedora team to give users the same experience across the different Spins and the main edition.”
I think the KDE spin actually included gnome-packagekit for a while but found that it didn’t always work right in the KDE env and brought in a bunch of deps, hence the desire to use Apper once it was mature enough.
“And it might just be better to port an existing one than to code one from scratch. None of the ones I have in mind are perfect, but the best candidate is Linux Deepin’s DSC.”
Unlikely unless it’s a PK front end. There are a couple of plans for writing an ‘app store’ type interface for Fedora, though.
“Yes, it is. Select the connection, hit the ‘properties’ button (that cog icon at bottom right), click Identity, there’s a ‘Firewall Zone’ drop-down right there.”
There is no Firewall drop-down here in my Fedora 19 installation. (network-manager-applet-0.9.8.2-1.fc19)
There’s no firewall zone dropdown menu in the GNOME 3 network settings.
“In this latest release, another upgrade script called fedora-upgrade was stable enough to be included.”
fedora-upgrade is included because someone submitted it as a package, that’s all. It is not an officially recommended upgrade method, and personally, I’m not a fan of it: if you want to upgrade via yum it’s probably better just to run each step manually so you know what the hell’s going on, and if you want a ‘supported’ upgrade method, use fedup. But that’s just my personal opinion.
To be clear, fedora-upgrade is essentially simply a script which ‘automates’ the steps for a yum upgrade recommended at https://fedoraproject.org/wiki/Upgrading_Fedora_using_yum .
I said as much at Upgrade Fedora 18 to 19 using fedora-upgrade or FedUp.
Ah, cool – I didn’t read that article yet, just wanted to clarify it here too since you mentioned it, for the benefit of other readers.
I feel sorry for the fedora devs, they do a step forward and two backwards. What a lame installer, really. If you want to kill the proyect there are many less painful ways.
“7. GNOME 3 Edition: […]One thing I fail to understand about the GNOME Shell, is why the Suspend option is not in the User Menu or why it’s not listed in the shutdown options window.”
Suspend option is in User Menu by holding the Alt key which will replace “Power off”
“I’m not a big user of keyboard shortcuts, which means that to get to the Frequent-ly used application picker view of the GNOME Shell requires two mouse clicks.”
That is where the dock on the left side comes in handy by adding your favourite applications and removing the least used one.
“Compared to Kaptan and Kapudan, Fedora’s desktop greeter is very basic. All it allows you to do is change input sources and configure online accounts. ”
Reading your “Every distribution should have its own Kapudan” article, one of commentators raise good points like: need to create folders (why doing it when a preset is already made), secure system (unneeded since Fedora enabled security tools by default), services (handled by systemd) to name a few. Detection of components like Bluetooth or printers should be automatically handled with minimum interaction possible. Note those post installation setting are mainly specific to desktop environments.
A desktop greeter does not have to duplicate what’s on Kapudan. I’m sure there are any number of user-configurable options in, say, the GNOME 3 edition that could be part of a desktop greeter. GNOME Tweak Tool itself could be fashioned into a desktop greeter.
So, what again is the benefit of hiding the Suspend option behind a keyboard shortcut? What should take 2 mouse-clicks to get to, now takes the same number of clicks plus a key press.
Tweak tools is considered as advanced options users wish to modify. Most ordinary users wanted to get a go and configure their desktops later.
“So, what again is the benefit of hiding the Suspend option behind a keyboard shortcut? What should take 2 mouse-clicks to get to, now takes the same number of clicks plus a key press.”
Only two mouse-click? What about double-click? This is very much a nitpick. Reason is ergonomic. You have both hands so why only use one? You can set both suspend and poweroff with the help of dconf-editor.
“You have both hands so why only use one?”
Because the other hand could be doing something else.
True. The cat could be nearby, or the dog needs petting, or something just needs to be scratched or squeezed. You never know.
“So, what again is the benefit of hiding the Suspend option behind a keyboard shortcut?”
I don’t really know, but for some reason the GNOME devs are hell-bent on there only being one such option on the User menu. There’s an extension which puts them both there all the time, though.