Dual-booting between a GNU/Linux distribution and Windows on a computer with one or more hard disks is a common practice for those who use both operating systems. It is a somewhat hassle-free approach to keeping a foot in both OS worlds. If you are new to Linux Mint and want to attempt dual-booting between Linux Mint 11 (see Linux Mint 11 review), the latest release of Linux Mint, and Windows 7 on a computer with one hard disk, this tutorial offers detailed instructions on how to accomplish the relatively simple task.
If your computer has more than one hard disk, the steps involved are virtually identical, and this guide can be of great help for setting up dual-booting on a computer with, say, two hard disks.
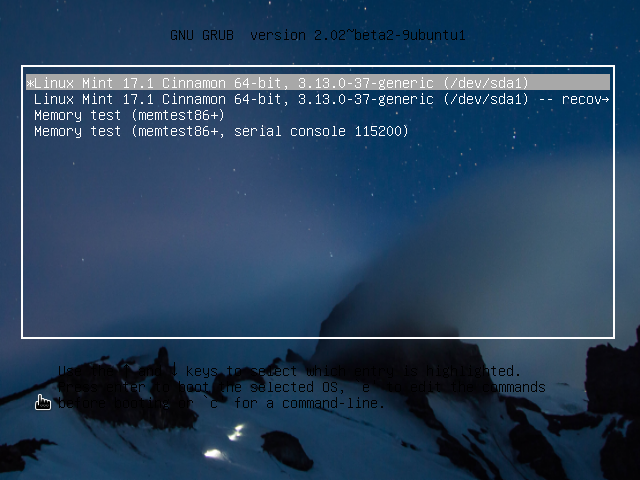
When configuring dual-booting on a single hard disk, the most important decision you will have to make is whether you want to install GRUB 2, the Linux Mint 11 boot loader, in the Master Boot Record (MBR) of the disk, so that when the computer boots, you will see this …

Or this, if you install Windows 7’s boot loader in the MBR.

Regardless of the option you choose, the result is not irreversible. For example, if you install Windows 7’s bootloader in the MBR and you change your mind, you can very easily overwrite it with GRUB. The reverse is also true. As a bonus, the simple steps involved in changing the boot loader installed in the MBR is made available at the end of this article.
The system used for this tutorial has an existing installation of Windows 7. If your computer has an existing installation of Windows 7 too, your first task is to free up enough space from Windows7. That space will then be used for installing Linux Mint 11. It is just as easy to free up space during the installation of Linux Mint, but this is my preferred method. If the computer you want to use has an existing installation of Windows, but you want to reinstall it, you can save yourself some time by leaving some unpartitioned space on the hard disk.
Okay, enough preliminary stuff. Ready to start? Me too. One more thing. If you have not done so already, download an installation image of Linux Mint 11 from here, burn it to a CD or DVD and keep it around.
To begin, boot into Windows 7, type partitions in the menu’s search filed. That will start the disk management application shown here. You can see that there are two partitions – the System Reserved, and the C drive. The first task is to create space for Linux Mint 11 by shrinking the C drive.

To do that, right-click anywhere on the drive and select “Shrink Volume…”

The disk management tool will always shrink the disk by half unless there is data in more than half of the disk. Unless you know what you are doing, click Shrink.

The surgical operation is complete. The Unallocated space is where Linux Mint 11 will be installed. Exit the disk management application, insert Linux Mint 11 installation CD or DVD and reboot the computer.

As it boots up you will see the boot menu. Linux Mint 11 is a Live CD/DVD, and you can only start installation from the Live environment. So, press Enter on the keyboard.

Once in the Live environment, click the Install Linux Mint icon on the desktop, then click Forward twice to get to the step shown here. The automated partitioner of the installer does not detect the free space, so the only way to partition and install Linux Mint 11 on it is to use the installer’s Advanced partitioning tool. To get to the Advanced partitioning tool’s window, select “Something Else,” then click Forward.





I shrunk the C partition to have some free space. Getting into Mint [15] where there is no ‘alongside’ option, I say that my free space read as ‘unusable.’
I did some research and found that with all HP computers, there are already 4 primary partitions. All are important, so I don’t want to delete them. And 4 is the maximum number of partitions per hard drive.
I have already installed Ubuntu alongside Windows 7 from before. The ‘alongside’ option was available.
I could just use Wubi’s ‘inside Windows’ option, but that would require me to uninstall Ubuntu, which I do not want.
I am not sure what to do.
Thanks!
What are the names of the partitions that came with PC. Please post them here.
Does it make a difference if you create the partitions in a different order, such as, boot, root, swap
instead of boot,swap,root ??
I ask because i read another tutorial some tyime ago that did it in that order
I’ve seen Swap as the first partition, followed by root. so the order does not seem to matter. However, when dual-booting, the location of the boot partitin relative to the first sector of the hard drive matters, as the system will fail to boot if the boot partition is located way out.
Hi, Im trying to find instruction like this the other way around install mint first then windows 7, I found your tutorial guide -> http://www.linuxbsdos.com/2012/01/14/manual-disk-partitioning-guide-for-linux-mint-12-kde/ but I cannot find the continuetion of this. please help thanks
Installing Windows after Linux on the same disk is not recommended. It’s the easiest way to make life difficult for yourself. When attempting to dual-boot, always install Windows first, followed by the Linux distribution.
For Mint, try this article. Other article for Mint are at http://linuxbsdos.com/category/mint.
thanks, I will trying that right now. thanks
thanks for such a great and easy way to make the things clear. actually I installed Linux mint 14 along with windows xp(already installed and working).but easybcd is showing the same error for me as what is given a few comments below by TRZALICA.i found on net that it doesn’t work for systems having only windows xp(and not windows vista/7 alongside)
I also couldn’t find any alternate software for easybcd. I tried to manually edit boot.ini file in xp and made an entry for mint by writing ‘ c:\grldr=”Linux mint 14(cinnamon)” ‘ at the end. now on startup, window shows a choice to select between two os but soon I pick “Linux mint 14(cinnamon)”,it gives the following error :
windows could not start because the following file is missing or corrupt:
\system32\hal.dll
please re-install a copy of the above file.
and then when i click enter,it boots to windows xp. i think it could not locate GRUB and the correction i made in boot.ini file is to check for GRUB at some other location. please give your valuable response about how to make a correct entry for GRUB during windows xp startup. thanks in advance
sorry I wrote the error message incorrectly. the following is correct message that I am getting :
windows could not start because the following file is missing or corrupt:
\system32\hal.dll
please re-install a copy of the above file.
there is written just before \system32\hal.dll. I don’t know even after entering why it didn’t come in above two comments.
omg again!!!!
why that keyword is not coming in any comment????it is:
angle bracket start windows root angle bracket end
then \system32\hal.dll
not this time please…
I don’t get it. I followed every step to the letter and tried this with LM14, picked the LM option in the MBR and all I seen was the word grub>… Anything?
If you tell us a few details about your hardware, we could help you out. The size of your partitions, including the Windows partitions. UEFI or non-UEFI motherboard.
It was installed via a live USB. I’m not too sure about the board, it’s an M2N-SLI board. I made a 50 GB partition for it and I used all the same sizes you did above, except for the /home partition. I just left it to use the rest of the hard drive partiton.
It worked fine with Grub and would dualboot, but I wanted to use the 7MBR. Windows 7 partition was 400 gb or so, it still had the recovery partition that 7 uses for restores.
This happened to me. Did you try to install it through the windows installer? It’s going to say that the Kernel must be installed.
Burn the image on a cd and install it using that.
It was installed via a live USB. I’m not too sure about the board, it’s an M2N-SLI board. I made a 50 GB partition for it and I used all the same sizes you did above, except for the /home partition. I just left it to use the rest of the hard drive partiton.
It worked fine with Grub and would dualboot, but I wanted to use the 7MBR. Windows 7 partition was 400 gb or so, it still had the recovery partition that 7 uses for restores.
Hey, I followed through your tutorial and I got stuck in a GRUB4DOS and it’s saying that the Kernel has to be installed. I did not install Linux from a disk but from a Windows Installer that was run on a Virtual Disk Mount.
I understand that the Kernel is in the Virtual Disk Files but is there any help you can provide me in accessing that or at least is there an easy way to solve this without having to reinstall Linux?
Thanks!
I don’t even recommend installing from a Windows installer. Grab an ISO image and install.
Hey thanks for responding. I’m now trying to do it through a disk but every time I create an account during the install, it gives me a username error and it then freezes.
I have one question. I set my partitions like this: /boot, /root, swap, /home and I installed GRUB into /boot partition (don’t want that Windows mess up with GRUB). I want to install LMDE next to Windows XP and I want to know how to do that because there is no solution in style of EasyBCD for Windows XP?? Everything is installed but I can’t see Linux in NTLRD boot menu…
Please help!!
Thanks in advance!
XP is supported in EasyBCD. It is the 2nd option in the “Type” dropdown.
No, it isn’t supported because when i try to open it in WinXP it said: Error opening BCD registry and than bla-bla and then Please note that EasyBCD requires the Windows Vista/7 bootloader, and will NOT work in XP-only environments.
I need a solution!
TY for this tutorial, really nicely put together.
Congratulations. This is the best web site i have seen. Very useful. I’ve done the steps and installed successfully the Mint with Win 7 working as dual boot. I just have a doubt: is EasyBCD no free anymore?
It is free for private use. That means you can download and use it for your own personal use. For business or commercial use, there is a fee. The current link is http://neosmart.net/EasyBCD