Disk encryption is one of several security features built into the Linux kernel that you may use to enhance the physical security rating and posture of a Linux installation. Disk encryption used to be widely recommended for notebook computers, and the reason is such mobile computers are more likely to be stolen than a desktop or server in a home or business. But that has changed. The general recommendation is this: Encrypt every disk. Whether it is in your notebook, desktop, or server. To paraphrase the late Johnny Cochran, If you have a disk, you must encrypt.
The primary purpose of disk encryption is to deny unauthorized (physical) access to your data. And the most effective method of enforcing that is to deny unauthorized persons from being able to boot your computer completely. In essence, deny such persons access to your login screen. When your computer boots, you want the person sitting in front of the keyboard to see something similar to this:
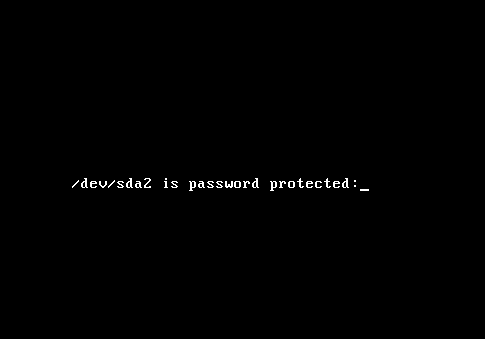
No passphrase, no access. Keep in mind that the most effective encryption scheme entails encrypting everything but the boot partition. Which means that Swap must also be encrypted. If Swap is not encrypted, sensitive data written out to disk can be recovered by anybody with access to the disk. Such data might even be the encryption key or passphrase.
The problem on the Linux front is few distributions support disk encryption during installation. If you use Ubuntu, you are in luck because it supports it. You must know, however, that the Live CD version and the Alternate Installation version support different types of encryption. The former supports encryption of the home directory. As shown in the image below, you can enable encryption of your home directory during the user account setup step. That, however, does not very little to boost the physical security posture of the computer. And the reason is simple: Once you log in, your home directory is decrypted.
And that is the main reason why automatic login (“Log in automatically”) should not be enabled. It is a very convenient feature, but it comes with a hefty price tag. The gist here is if you want full disk encryption, do not install Ubuntu from a Live CD ISO image.

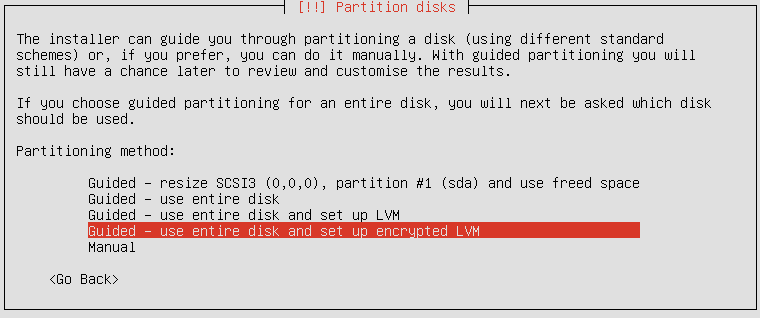
You should instead use an Alternate Installer ISO image. Aside from full disk encryption, it also supports LVM, the Linux Logical Volume Manager, and if you chose the option shown in the image below, the installer will set up two partitions. The first partition, used for /boot, will not be encrypted. The system needs an unencrypted boot partition to complete some preliminary boot steps. The second partition, which will be initialized for use by LVM, will be encrypted, and under it, the system sets up two logical volumes – one for the root directory, and the other for Swap. That is how full disk encryption should be configured. That, by the way, is how it is configured on Debian, Fedora, and Sabayon.

If you do not want to use LVM, you can set up a non-LVM disk partitioning scheme and enable encryption for the partitions manually. However, because of the benefits of LVM, it is highly recommended that you use it. There is no downside. Or none that you will notice. An article, to be published by end of day tomorrow, will provide a step-by-step guide on how to install Ubuntu 11.04 on an encrypted LVM partitioning scheme. To have it delivered automatically to your Feed Reader or Inbox, subscribe via RSS or email.





Ubuntu now has the option to encrypt the whole disk or the home folder from the installation process on the live CD as of 12.10. If you have already setup and want some tools to encrypt partitions or other folders you can do so from gnome-disk-utility which is a handy GUI frontend for formatting disks, this allows you to encrypt partitions in ext4 during format. If you prefer folders then install encfs and cryptkeeper, or gnome-encfs-manager, which will allow you to encrypt hidden folders and mount them when decrypted. Encfs and cryptkeeper work very well with dropbox and Ubuntu one.
I have installed 12.04 on my laptop and marked the option to encrypt my home folder. After reading you post, the immediate question in my mind is: when I’m logged in using my computer, if somebody gains access to it via network and decide to download my files, are they going to be encrypted or decrypted?
Logging in decrypts your home folder, otherwise, you’d be required to authenticate before opening your files. So, yes, if you using the system, anybody with network access can read and write to the machine. For example, anyone with legal or illegal permission can ssh to your computer, while you are logged in, and do anything they want. Encryption does not stop that type of activity.
Encryption prevents unauthorized access before the system boots. On a multi-user PC, encrypting your home folder prevents other users from accessing it while they are using the machine from their own account.
I have already setup my laptop with ubuntu 11.10.
Can I now encrypt the whole hard disk , so the next time I reboot , it should ask me for a password ,akin to the screen shot you have above. ?
Afaik, you can’t You may, however, be able to encrypt new volumes or directories using encfs or other applications.
This article is extremely inaccurate and misinformed.
Ok, what parts of it are “extremely inaccurate and misinformed”?
Hi, if i already have a windows partition on my hard drive.
How should i set up ubuntu on another partition with encryption so i can dualboot.
Try the following link:
http://www.linuxbsdos.com/2011/05/22/how-to-dual-boot-windows-7-and-ubuntu-11-04/
Or look thru Ubuntu’s category for other articles on dual-booting it and Windows:
http://www.linuxbsdos.com/category/ubuntu
10000000 de gracias por los artículos sobre ubuntu =)