Editor: Interesting article if you’re into cryptocurrency trading.
Our Cyber Safety Solutions team identified a malicious Chrome extension we named FacexWorm, which uses a miscellany of techniques to target cryptocurrency trading platforms accessed on an affected browser and propagates via Facebook Messenger. A very small percentage of users were affected by these malicious extensions, and Chrome had already removed many of these extensions prior to being alerted by Trend Micro.
FacexWorm isn’t new. It was uncovered in August 2017, though its whys and hows were still unclear at the time. Last April 8, however, we noticed a spike in its activities that coincided with external reports of FacexWorm surfacing in Germany, Tunisia, Japan, Taiwan, South Korea, and Spain.
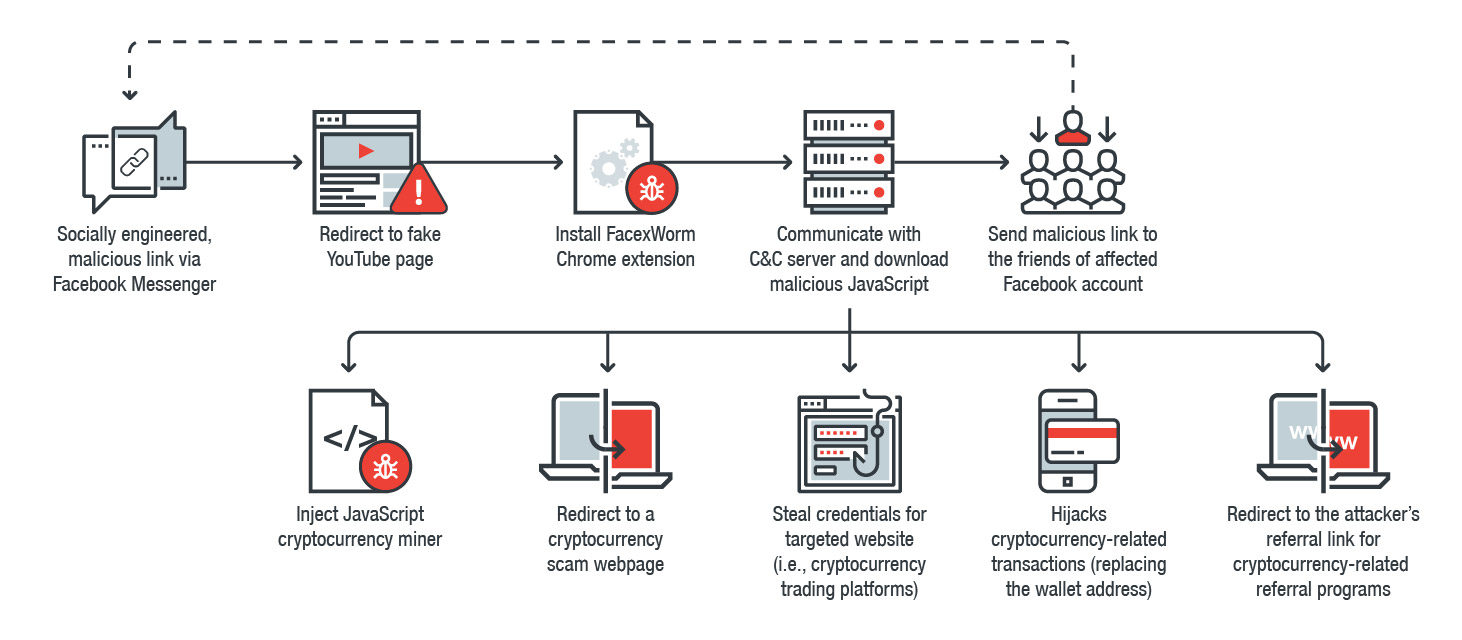
Our analysis reveals FacexWorm’s capabilities were made over. It retains the routine of listing and sending socially engineered links to the friends of an affected Facebook account, just like Digmine. But now it can also steal accounts and credentials of FacexWorm’s websites of interest. It also redirects would-be victims to cryptocurrency scams, injects malicious mining codes on the webpage, redirects to the attacker’s referral link for cryptocurrency-related referral programs, and hijacks transactions in trading platforms and web wallets by replacing the recipient address with the attacker’s.
While we’ve so far only found one Bitcoin transaction compromised by FacexWorm when we checked the attacker’s address/wallet, we don’t know how much has been earned from the malicious web mining.
Read the complete article here.
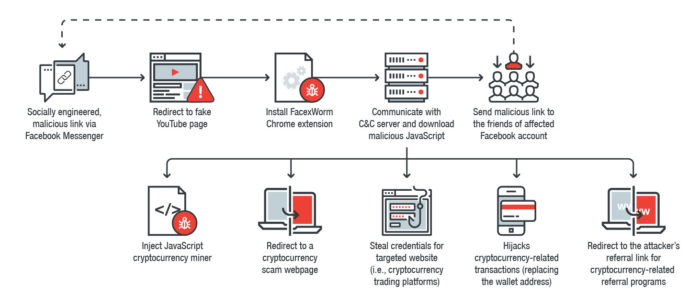
How FacexWorm propagates