Calamares is the graphical installation program that you’ll most likely use to install many popular and not-so-popular Linux distributions. That’s because its development is not tied to a specific distribution and adoption by desktop distributions has been encouraging.
In this article, you’ll learn how to use its disk encryption feature to enhance the physical security posture of a supported Linux distribution. And we’ll look at how to use that feature when a Linux distribution is being installed in standalone mode and also when it’s being installed alongside Windows 10 in dual-boot setup.
The images used in this article were taken from test installations of Manjaro 16.10 in standalone mode in a virtual environment, and from a dual-boot setup between Manjaro 16.10 KDE and Windows 10 on a Lenovo G50 laptop.
Figure 1 shows the disk partitioning options available on the latest edition of Calamares. The program has no default method.
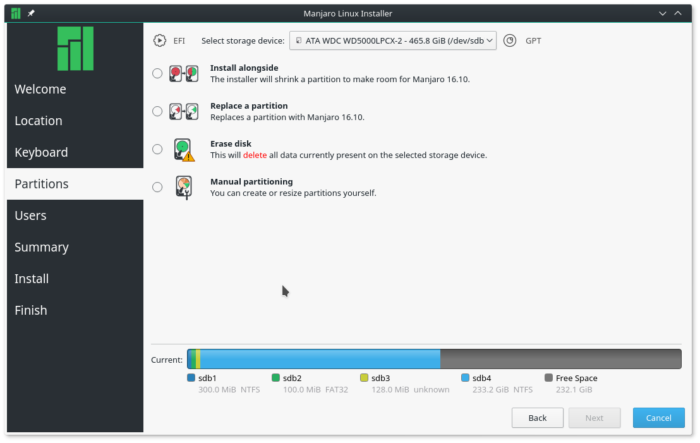
Figure 1: Disk partitioning options of Calamares
Disk Encryption in Calamares in Standalone Mode
With the Replace a partition option, you can select a free portion of the disk that you wish to install the Linux distribution on, or an occupied partition that you wish to erase. The installer will auto-partition it for you. It will also encrypt it if you select the Encrypt system option.
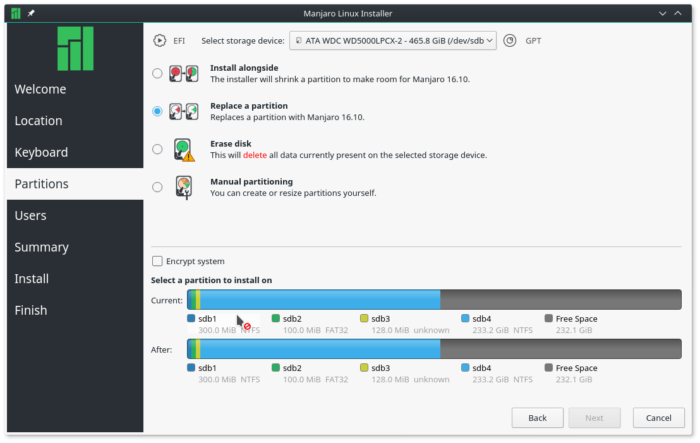
Figure 2: Replace disk partitioning option of Calamares
If your choice is the Erase disk option, then selected Encrypt system, the installer will erase and encrypt the whole disk.
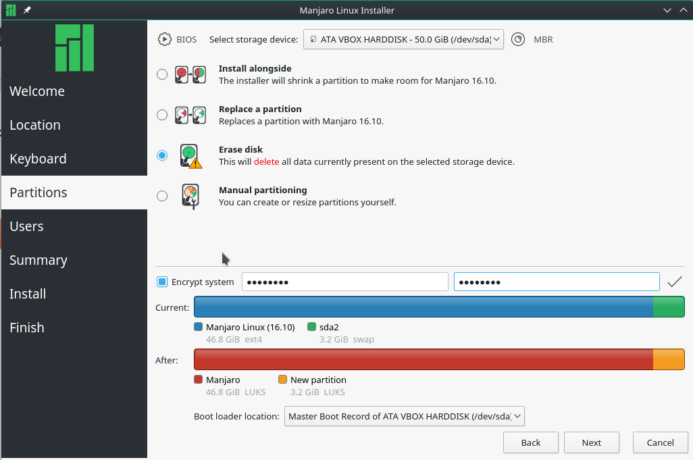
Figure 3: Calamares erase disk partition option
At the next screen, after selecting one of the previous options, the installer will display the partitions that will be encrypted. All partitions, including the swap partition, are encrypted.
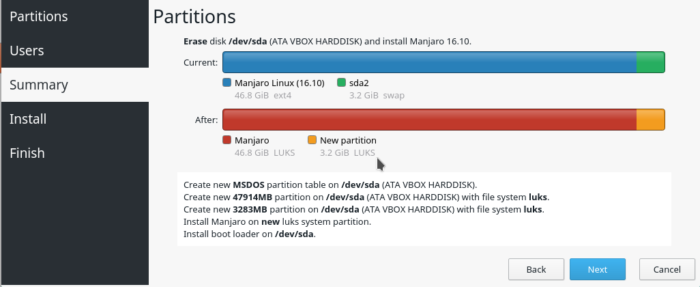
Figure 4: Calamares disk partition confirmation
After installation and reboot, you’ll be prompted for the encryption passphrase before the GRUB boot menu is displayed. As shown in Figure 5, the system is asking for a passphrase to decrypt hd0,msdos1. That’s the first partition of an MBR-partitioned disk. And this is when you get to experience the benefit of disk encryption. The system will not boot if the correct encryption passphrase is not specified. So if another party gains unauthorized, physical access to the computer while it’s not turned on, you can be rest assured that the system will not boot. The other side of that, is if you forget the encryption passphrase, same deal happens to you. You won’t be able to brute-force your way in.
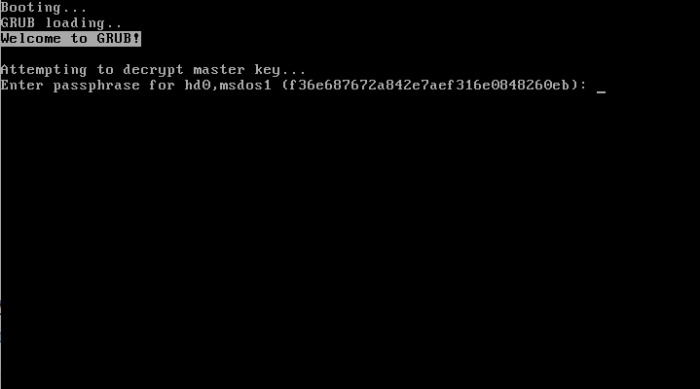
Figure 5: Calamares decrypting an encrypted disk
This is what happens when the correct disk encryption passphrase is specified – you’re presented with the GRUB boot menu. Now you may boot into your favorite Linux distribution.
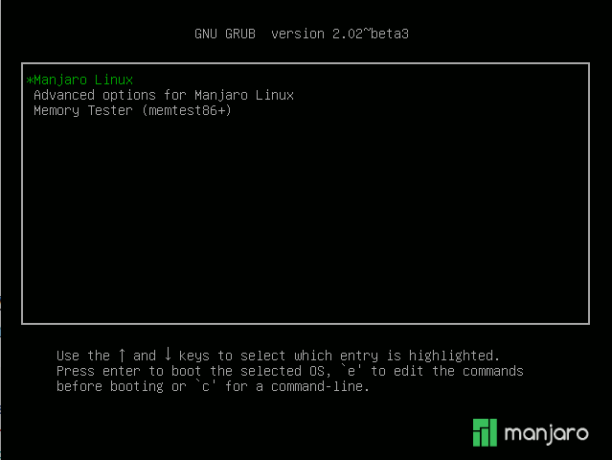
Figure 6: GRUB boot menu after disk has been decrypted
Disk Encryption in Calamares When Dual-booting with Windows 10
Setting up a dual-boot system using a Linux distribution that uses Calamares and Windows 10 with the Linux side encrypted is just as easy in standalone mode. The recommended approach to that is to select the Manual partitioning option.
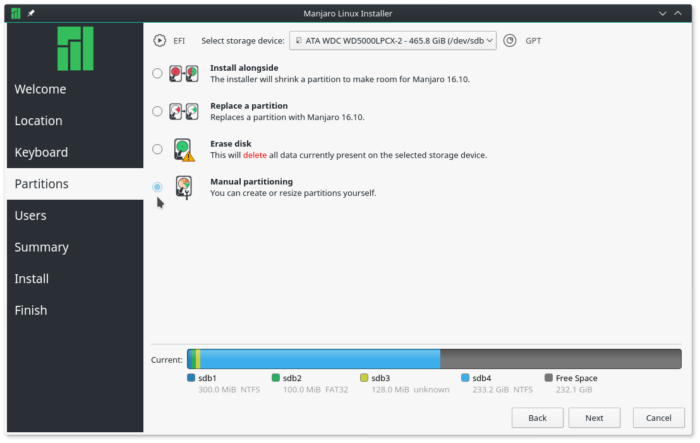
Figure 7: Manual disk partitioning option of Calamares
This and the next two images show how to create an encrypted custom set of partitions using the installer’s partition editor. In Figure 8, the root partition is encrypted. To encrypt any partition, simply select the Encrypt option, then specify and confirm the encryption passphrase.
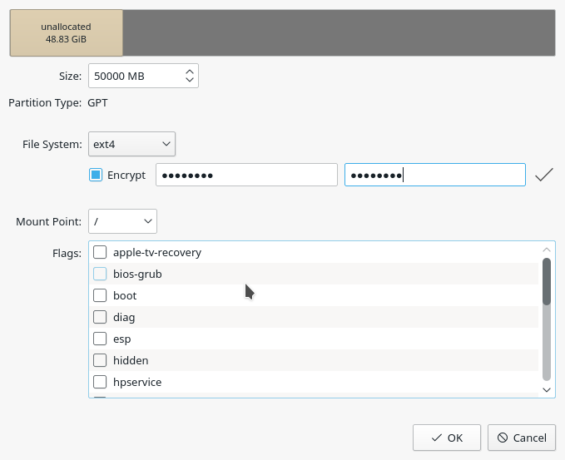
Figure 8: Creating an encrypted root partition in Calamares
Same was done when creating the partition mounted at /home.
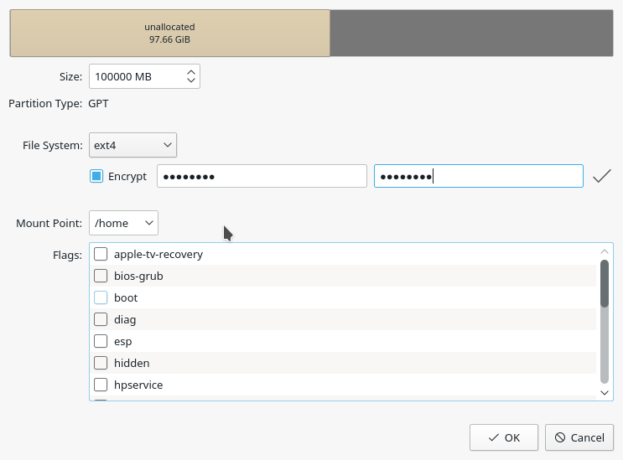
Figure 9: Creating an encrypted home partition in Calamares
And for the swap partition too. It is very important that you encrypt all partitions, except for a partition mounted at /boot or /boot/efi. Also use the same encryption passphrase for each.
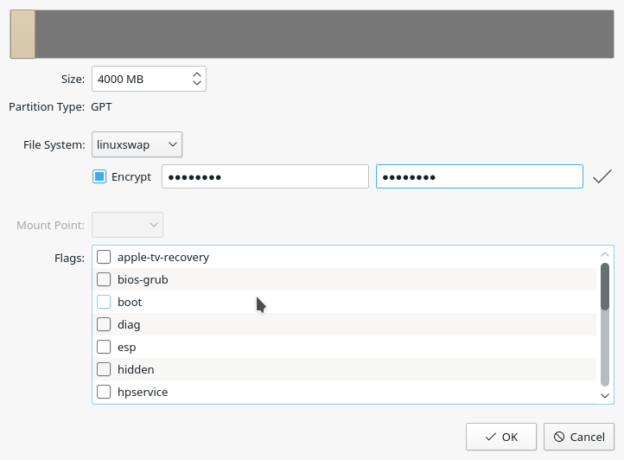
Figure 10: Creating an encrypted swap partition in Calamares
At the installer’s manual disk partitioning window, the partitions marked for encryption will have LUKS in the File System column.
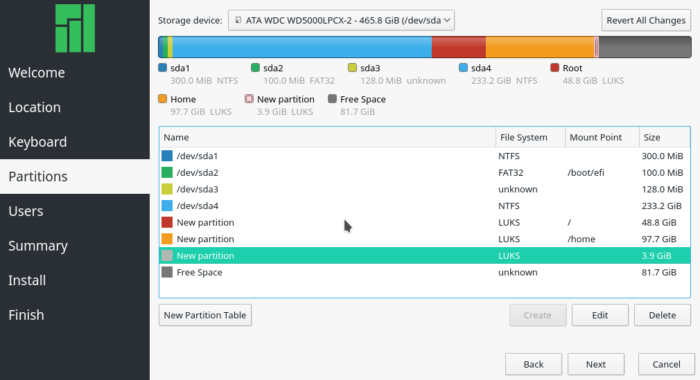
Figure 11: LUKS-encrypted partitions created with Calamares in a dual-boot setup with Windows 10
After a successful installation and reboot, you’ll be prompted for the encryption passphrase before the GRUB boot menu is displayed. In this image, notice that the system is asking for a passphrase to decrypt hd0 gpt5. That corresponds to the root partition of the Linux side of the business. Contrast that with the situation in Figure 5, during a standalone mode setup.
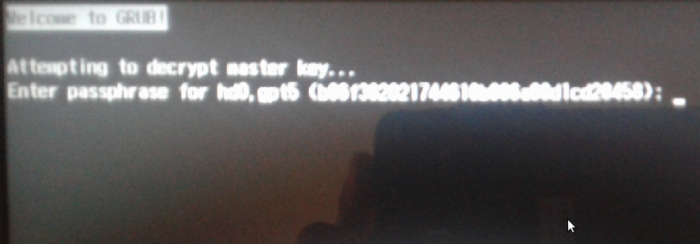
Figure 12: Decrypting a disk encrypted with Calamares in a dual-boot setup with Windows 10
Note that on the test system I used for this article, if the GRUB Boot Manager is the default boot manager, I had no problem booting into either operating system. However, when I set the default boot manager to Windows (10) Boot Manager, the system will not boot. What I got instead, is shown in Figure 13. Not sure why, but that’s how it worked on mine. If your experience is different, post a comment.
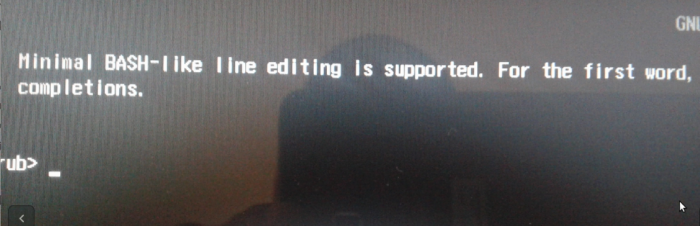
Figure 13: GRUB error when Windows Bot Manager is the default in a Calamares disk encrypted, dual-boot setup with Windows 10
And that’s how you can encrypt your Linux installation if the distribution uses the Calamares graphical installer – in standalone and dual-boot mode.




grub encryption input language is most of the time english. but the world is more than that.
if you configure a complex passphrase or using a token you might get into troubles.
the calamaras installer does not recognize the current input language and will not setup grub to use the same input as at install time.
I hope someday open source will accept the world and not some exotic singularity.
I’m sure you meant disk encryption, not “grub encryption”.
Regarding the problem you’ve encountered preventing you to boot Windows 10 through the Windows Boot Manager on a FDE [Full Disk Encryption] Linux installation you can try the following (credits to Linux22, https://community.linuxmint.com/tutorial/view/2191):
“If you want to resolve this last error you must break a taboo …
You must edit the ‘grub.cfg’ file in your directory ‘/boot/grub’, search for the menuentry ‘Windows Boot Manager’ and comment out the line ‘cryptomount -u’ with a # …
Remember that you need root privileges for editing these files.”