Using a VPN (virtual private network) will, to a large extent, protect your data and privacy on the Internet – but not if it suffers a VPN leak. What’s a VPN leak, you say, and what causes it? I’ll answer those questions in this post and also tell you how to check if your VPN is leaking, and how to protect yourself.
What Are VPN Leaks?
It’s when your IP address or traffic leak out of the encrypted VPN tunnel. It doesn’t take a rocket scientist to realize why that is a problem. Not only will your ISP see what you do online, but advertisers and websites will be able to track your digital footprints with your real IP address. Also, you won’t be able to bypass geo-restrictions anymore, because if a website knows your real IP address, they’ll know what country you are from.
So What Exactly Makes Your VPN Leak?
It’s not just one leak. There are actually quite a lot of VPN leaks that can ruin your fun. Here’s a quick but in-depth overview of all of them:
1. IP Leaks
IP leaks occur when your IP leaks out of the VPN tunnel. They come in two types:
-
IPv4 leaks – This happens if there are miscommunication errors between your device and the VPN server, the VPN server is poorly configured, or your ISP or operating system have trouble communicating with the VPN server.
-
IPv6 leaks – This kind of leak happens if the VPN doesn’t support IPv6 traffic. Not a lot of VPN providers do, and your IPv6 address will leak outside the VPN tunnel because of that.
2. DNS Leaks
These leaks happen when your VPN doesn’t route your DNS queries (website connection requests) through their own DNS server. Instead, they go through your ISP’s DNS server, meaning they can see what websites you browse. Here’s why DNS leaks usually occur:
-
Your network has configuration issues (basically, it uses the wrong DNS addresses).
-
Your VPN doesn’t have a DNS server (huge red flag).
-
Someone hacked into your router.
-
Your ISP uses a transparent DNS proxy.
-
The VPN suffers an IPv6 leak (which, in turn, causes a DNS leak).
-
Operating system features get in the way on Windows (specifically Teredo and smart multi-homed name resolution).
3. WebRTC Leaks
WebRTC is an open-source project that allows web browsers to support video calling, voice calling, and P2P sharing features. WebRTC is also a huge issue for VPNs since it can cause IP leaks. Why? Because WebRTC functionality can actually bypass the VPN tunnel. Since most web browsers enable WebRTC by default, this VPN leak happens a lot.
4. Traffic Leaks
This is when your entire Internet traffic leaks out the VPN tunnel. A traffic leak takes place when your VPN connection goes down – even if it’s only for a few seconds. That can happen if you use a resource-intensive protocol, if the VPN server is very far from you, or if the VPN client crashes. While the connection is down, your traffic is no longer encrypted. And anyone can spy on it.
How Do You Know If Your VPN Is Leaking?
It’s not exactly possible to tell when you’re dealing with a VPN leak. There are no signs or alerts that notify you about it. How to check if your VPN is leaking then? Simple – just follow that link. It’ll take you to ProPrivacy’s VPN leak test tool. It’s very easy to use, takes a few seconds or minutes at most to check your connection, and will let you know if your VPN has any:
-
IPv4 leaks;
-
IPv6 leaks;
-
DNS leaks;
-
WebRTC leaks.
It can’t check for traffic leaks, yes, but it doesn’t need to. If your VPN doesn’t have a Kill Switch, you will experience a traffic leak when your connection goes down.
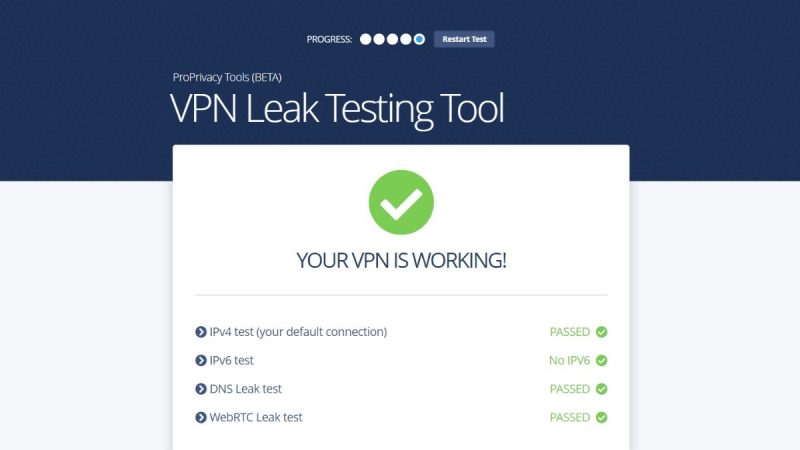
VPN leak test tool
How to Fix VPN Leaks
Here are some quick tips that should help you prevent any kind of VPN leak:
IPv6 Leak Fixes
If your VPN doesn’t support or block IPv6 traffic, and you have an IPv6 address, you’ll need to disable it. Doing that is pretty simple, though. Use this guide to learn how to do it in Ubuntu.
DNS Leak Fixes
-
Disable IPv6 like we mentioned above.
-
If you’re a Windows user, you’ll need to disable the problematic features. Here’s how to get rid of Teredo, and here’s how to disable smart multi-homed name resolution. Also, consider using this patch for OpenVPN too.
-
Try changing your DNS settings to either Google Public DNS (8.8.8.8 and 8.8.4.4) or OpenDNS (208.67.222.222 and 208.67.220.220). Alternatively, see if your VPN provider can offer you the address of their DNS server.
-
Change your router’s default login credentials to make it harder for hackers to break into it.
-
If the VPN can’t bypass your ISP’s transparent proxy, use OpenVPN, find and edit the server’s .ovpn or .conf file with a text editor and add this line: block-outside-dns.
WebRTC Leak Fixes
-
Disable WebRTC on your browser. Here’s a helpful guide.
-
Use your VPN provider’s extension if it blocks WebRTC, or use WebRTC Leak Prevent on Opera and Chrome.
-
Use uBlock Origin – an open-source script blocker that prevents WebRTC leaks.
Traffic Leak Fixes
The only way you can prevent a traffic leak is if you use a VPN that has a Kill Switch. That’s a feature that will shut off your web access if the VPN connection goes down. It will only turn it back on when the VPN tunnel is up and running.
The Bottom Line
VPN leaks can make using a VPN completely pointless since your data and IP address are no longer hidden on the web. That’s why you should use a VPN leak test tool regularly to make sure there are no problems. Also, it’s a good idea to use a secure VPN that offers WebRTC, DNS, and IP leak protection, and which also has a Kill Switch. NordVPN and ExpressVPN are excellent options.





Not sure if there are a lot of VPNs that have a kill switch, but mine does as well (I’m a Surfshark user btw). I always have it on since I torrent a lot, and just in case my VPN connection drops, there wouldn’t be any leaks. Every time I check the IP leak for this VPN, there aren’t any, so I guess it’s a good indicator, but it’s always better to be cautious.
An article on Surfshark will be posted within the next few days. What has been your experience with it like?