The news making the rounds in the Linux security arena is the one about a bug discovered in Cryptsetup, the program used to set up disk encryption in Linux.
The bug, detailed here, was discovered by Hector Marco and Ismael Ripoll.
As described by the authors, the bug is basically the result of incorrect error handling after several failed attempts to decrypt a LUKS encrypted disk. And the failure could be triggered when a user inputs the wrong encryption passphrase, or repeatedly presses the ENTER key.
In their report, they noted that:
An attacker with access to the console of the computer and with the ability to reboot the computer can launch a shell (with root permissions) when he/she is prompted for the password to unlock the system partition. The shell is executed in the initrd environment. Obviously, the system partition is encrypted and it is not possible to decrypt it (AFAWK). But other partitions may be not encrypted, and so accessible. Just to mention some exploitation strategies:
…
Their report appears to be based on tests of Debian and Ubuntu systems. From my own experience, I can report that every major distribution seems to handle failed hard disk decryption a bit differently. To start with Ubuntu, the system will drop to an initramfs shell after 181 failed attempts (you can simulated it by pressing the ENTER key that many times). If you have such a system, give it a try. After 181 failed attempts, you’ll be presented with a shell like the one shown in Figure 1.
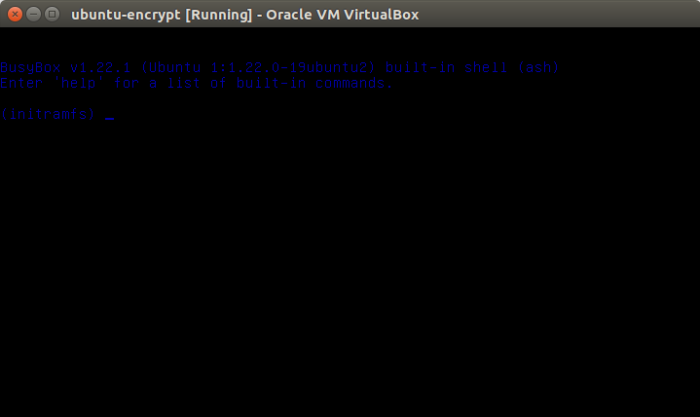
Figure 1: Result of failed attempt to decrypt Ubuntu 16.10 system partition
With Fedora 25 Rawhide, you have just three attempts before the system gives you a shell. And that has been the case with Fedora systems for as long as I can remember. Compare that to the 181 attempts on Ubuntu 16.10.
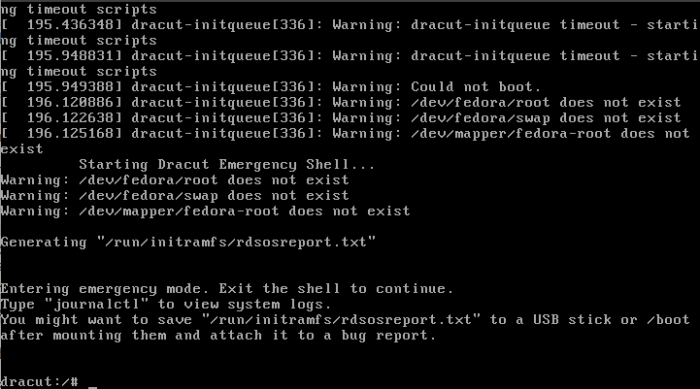
Figure 2: Result of failed attempt to decrypt Fedora 25 Rawhide system partition
Manjaro 16.10, which uses the Calamares installer, is even less forgiving. It gives you just one attempt before it drops you into a shell.
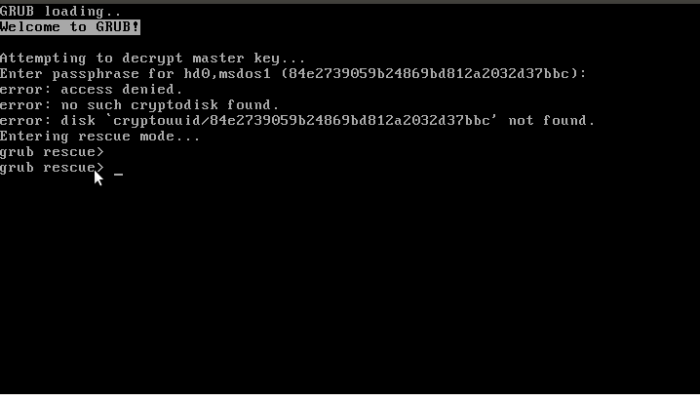
Figure 3: Result of failed attempt to decrypt Manjaro 16.10 system partition
In all three case, the encrypted system partition is still encrypted, so you data is still save. However, as detailed in the bug report, unencrypted partitions, like ones mounted at /boot and /boot/efi (on UEFI systems) might still be open for exploitation. But how far can an attacker go on such system, when the system partition is still encrypted? Not far, I hope.
A bug always has a solution, and in this case, the authors provided an easy-to-apply workaround. I’ve expanded on it a bit in the code block below. If after applying the workaround you discover that it does not work, welcome to the club. It didn’t work on all the encrypted systems I applied it on – Ubuntu 16.10, Manjaro 16.10, and Fedora Rawhide. By the way, all three distributions were running either Cryptsetup 1.7.2 or 1.7.3.
# # You might want to backup your /etc/grub/default file before executing this command sudo sed -i 's/GRUB_CMDLINE_LINUX_DEFAULT="/GRUB_CMDLINE_LINUX_DEFAULT="panic=5 /' /etc/default/grub # Follow that with this on Ubuntu and Manjaro on no-UEFI systems sudo grub-install /dev/sda # On UEFI systems on Ubuntu and Manjaro, the second command should be # Change /dev/sdaX to match your systems /boot/efi partition sudo grub-install /dev/sdaX # On Fedora Rawhide, the second command on no-UEFI systems should be sudo grub2-install /dev/sda # On Fedora Rawhide, the second command on UEFI systems should be # Change /dev/sdaX to match your systems /boot/efi partition sudo grub2-install /dev/sdaX #
If the workaround stopped your system from dropping into a shell on failed decryption attempts, which means it worked, post a comment. I’ve contact the authors with my findings, so I’ll update this article when I get some feedback from them. Perhaps there’s something I missed.






Hi,
I think i found a workaround on Fedora.
You can add the rd.shell=0 option to your Grub command line to disable the dracut shell.
– Edit the /etc/grub2.cfg file
– Add rd.shell=0 to the /vmlinuz… line
– Reboot and test it
That works for me.
SaiYan
Thanks, I’ll give it a shot later today.
But that file is not supposed to be edited, as it is auto-generated.