WebGoat is a deliberately insecure, Java web application designed for the sole purpose of teaching web application security lessons. The officially-stated aim is to enable developers to “test vulnerabilities commonly found in Java-based applications that use common and popular open source components”.
In other words, how to hack Java web applications. This tutorial shows how to install it on any recent version of Ubuntu, like Ubuntu 14.04, 15.04 and 15.10.
WebGoat is maintained by OWASP, the Open Web Application Security Project, and it features a series of lessons that teach different application security and penetration testing techniques.
Before you get started, you might want to first learn the basics of ethical hacking and online penetration testing by requesting a free video course of Online Penetration Testing and Ethical Hacking.
After you’ve completed that course, come back here and learn how to install WebGoat.
WebGoat is a Java application so you need to have a Java JRE installed. To install and verify that a Java JRE is installed on your edition of Ubuntu, launch a shell terminal and type the follow commands. The recommended JRE is 1.7, which is the current available version, so you’ll be covered by installing the default JRE package:
# Install the default Java JRE from the repository using the following command sudo apt-get install default-jre # Verify that Java is installed java -version # Expected output of above command is: java version "1.7.0_95" OpenJDK Runtime Environment (IcedTea 2.6.4) (7u95-2.6.4-0ubuntu0.15.10.1) OpenJDK 64-Bit Server VM (build 24.95-b01, mixed mode) #
Next, download the executable jar file by running the following command:
# Download the executable jar file to a suitable location, like your Downloads folder wget https://s3.amazonaws.com/webgoat-war/webgoat-container-7.0-SNAPSHOT-war-exec.jar #
After that, you can run it using the following command:
# Run the WebGoat jar file java -jar webgoat-container-7.0-SNAPSHOT-war-exec.jar #
Finally, access the web interface by navigating to http://localhost:8000/WebGoat. You should get a login screen just like the one shown in Figure 1, and you can log in as a guest or privileged user using the webgoat account.
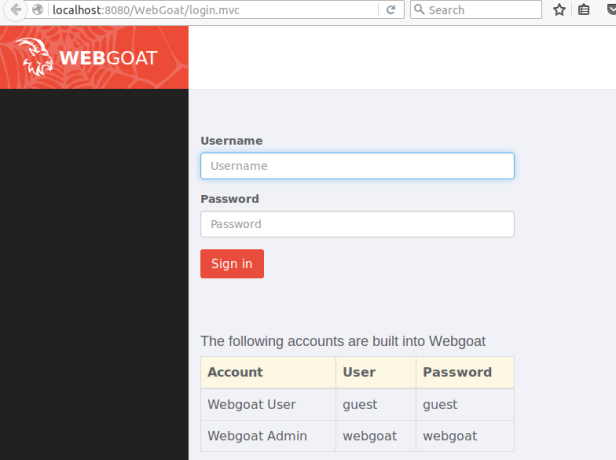
Figure 1: WebGoat’s login screen
Logging in gives you access to a bunch of lessons that allows you to practice pentesting on a live system that you have permission to mess with.
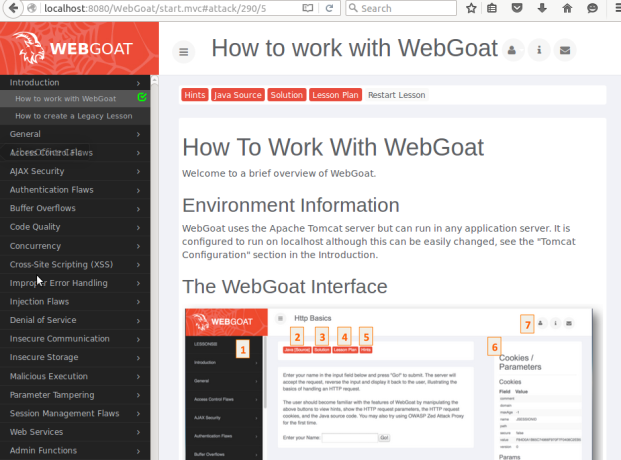
Figure 2: WebGoat’s interface showing the category of lessons
Here, for example, is the DOM Injection lesson. WebGoat is a cool tool, but don’t take what you learn by using it to hack systems that you don’t own. The point of it is to become familiar with ways that Black Hats can use to compromise your system. If you know the secrets of their craft, you’re in a better position to secure your systems. Happy pentesting! Learn more about WebGoat from the project’s home page.
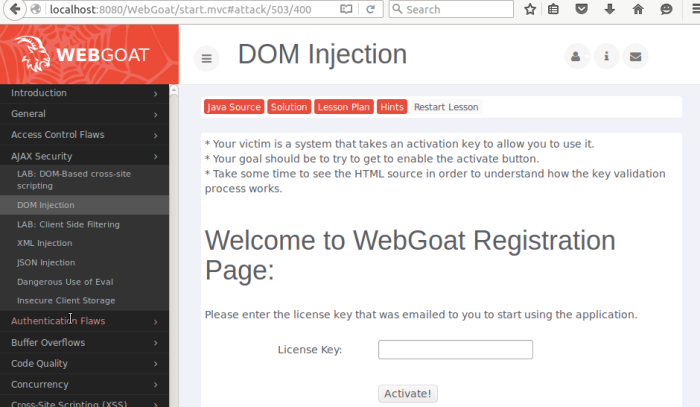
Figure 3: WebGoat’s interface showing the DOM injection lesson



Im getting a HTTP 500 status unable to compile class for Jsp when im running the jar file … i don’t know how this came up since ive followed all the steps exactly as said .
hi,
not http://localhost:8000/WebGoat ….
but http://localhost:8080/WebGoat