So Lenovo has been reeling from the self-inflicted wound called Superfish, VisualDiscovery or WindowShopper.
No sympathies from me, buster. What else have you done in the past that nobody found out?
If you have no idea what Superfish is, here’s a very brief summary.
Superfish is an adware installed on some Lenove consumer computers. The actual name is WindowShopper or Visual Discovery. Superfish is the name of the company that makes the software. A good description of what it does is provided by the US Computer Emergency Readiness Team (US CERT):
Starting in September 2014, Lenovo pre-installed Superfish VisualDiscovery spyware on some of their PCs. However, Superfish was reportedly bundled with other applications as early as 2010. This software intercepts users’ web traffic to provide targeted advertisements. In order to intercept encrypted connections (those using HTTPS), the software installs a trusted root CA certificate for Superfish.
All browser-based encrypted traffic to the Internet is intercepted, decrypted, and re-encrypted to the user’s browser by the application – a classic man-in-the-middle attack. Because the certificates used by Superfish are signed by the CA installed by the software, the browser will not display any warnings that the traffic is being tampered with. Since the private key can easily be recovered from the Superfish software, an attacker can generate a certificate for any website that will be trusted by a system with the Superfish software installed. This means websites, such as banking and email, can be spoofed without a warning from the browser.
That’s just a very wicked software to have running on your computer. Lenovo has made public comments about the issue and Microsoft has released something that can fix it. Even Facebook has a team of researchers dedicated to the matter.
But those are not enough. You see, Superfish (the company) is an outfit that needs to make money, and VisualDiscovery is their main product. So the company is not going away any time soon. Just last year the company was voted 4th (out of 5000) on the list of fastest-growing private companies in America. Fastest-growing translates into “our product is red hot”, as in, very, very popular.
So no, Superfish, WindowShopper or Visual Discovery is not going away just because of one bad public relations story. Knowing how these things play out, Superfish will only get worse (or better, depending on where you stand on the issue).
A blog post from security researchers at Facebook paints a very grim picture for users of the operating system and browsers impacted by Superfish (Windows folks the finger is pointing in your direction). See Windows SSL Interception Gone Wild.

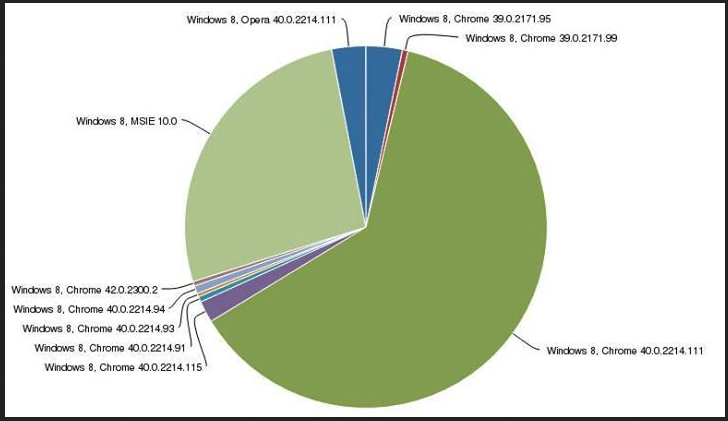
Figure 1: Percentage of browsers on Windows 8 affected by Superfish. (source: Facebook Security Research)
Owners of Lenovo computers are, therefore, not the only folks at risk of man-in-the-middle (MitM) attacks. So exchanging your Lenovo computer for another Windows brand won’t do you much good.
A real solution, a final solution, is one that does not involve the parties that caused the problem in the first place. And that solution is this: Find a good Linux distribution and install it over Windows. End of story. No more adware or other factory-delivered malicious software.
I know this solution is not for every Windows user, so evaluate your situation carefully before you attempt to replace Windows with a Linux distribution. The Linux distributions that I highly recommend for new users because they’re most likely to just work, are Linux Mint, Ubuntu Desktop, ROSA Desktop, Deepin, Mageia and Manjaro. If you don’t mind getting some digital grease on your fingers, try Debian and Fedora. There are many more Linux distributions out there, but if you’re new to Linux, the recommended distributions are good starting points.
So go ahead, take one of those Linux distributions out for a test drive and let’s clean up this mess called Superfish.






Steps-
Open the Windows Start menu or Start screen and search for certmgr.msc.
Click Trusted Root Certification Authorities and open Certificates.
Scroll down or use find to get to the Superfish, Inc. certificate.
Right-click it and select Delete.
Open the Windows Start menu or Start screen and search for certmgr.msc. …Click Trusted Root Certification Authorities and open Certificates.Scroll down or use find to get to the Superfish, Inc. certificate.
Right-click it and select Delete.
I have a Lenova laptop. I bought it specifically to install Linux. I totally wiped Windoes when I got it and installed Ubuntu. That was several years ago so I don’t think I had that software on my computer but I don’t have to worry about it now.
Companies need to be held financially accountable for the havoc they create.
Sue Superfish into oblivion.
It’s time we users demand the right to buy bare bones hardware and use it as we like! Enough with all this vPro Secure Boot Computrace nonsense! And now this! We should demand unlocked platforms and no more backdoors!
Yep said very true