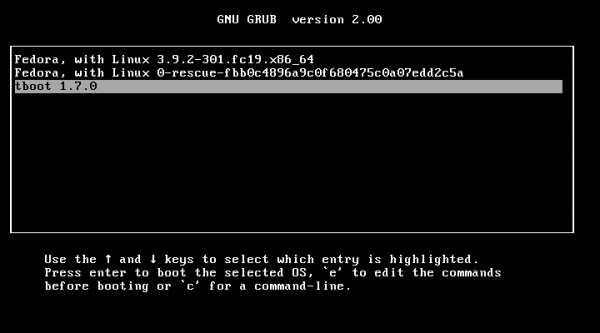
After installing Fedora 19 beta and rebooting my test computer, I noticed that one of the options available in GRUB’s menu is tboot 1.7.0. Not sure what it’s for, I selected it and hit the Enter key.

On the next GRUB screen, is the option to boot into Fedora GNU/Linux, with tboot 1.7.0. But what does tboot do? Well, one way to find out is to boot into the system and see what dmesg can tell me. Nothing.

Fedora’s official page on tboot has very little useful information, but a search of Apper, the graphical package manager, returns an entry for a tboot package. The description for tboot goes like this:
Trusted Boot (tboot) is an open source, pre-kernel/VMM module that uses Intel Trusted Execution Technology (Intel TXT) to perform a measured and verified launch of an OS kernel/VMM.
Ok, so tboot is the open source package for taking advantage of Intel Trusted Execution Technology (Intel TXT). Intel TXT requires a software and hardware component to work. Here, the software component is obviously tboot. The hardware component is a chip on the motherboard called the Trusted Platform Module (TPM). So if our computer does not have a TPM chip, tboot is of no use to you.
TPM chips are embedded in the hardware of Intel processors. But most of those are server processors, such as the Intel Xeon E3 v3, Intel Xeon E5 and Intel Xeon E7, and the latest Intel Core vPro processors.
Still not sure what to make of tboot in Fedora 19 beta, I sent an email to Adam Williamson, a Red Hat dude and publisher of happyassassin.net. His reply copied another Red Hat dude who said that tboot appearing by default in GRUB’s menu is a bug, and gave the following reasons why it should not be in the default installation.
1. We don’t really have the infrastructure for doing useful things with it, so it’s really mostly just something an interested party could do development on.
2. Sinit (the method for entering TXT mode) runs a pile of closed source code provided by the firmware on the host CPU effectively as the kernel, and a lot of people aren’t too keen on that. This is especially true since the code is doing things like turning on special processor modes and doing cryptographic verification, which is exactly the sort of thing open review of code often finds tons of bugs in…
3. There are some cases right now where it doesn’t really work right (for instance, UEFI). Obviously these are just bugs, so this is the least important of this list.
So, if you have installed Fedora 19 beta and were/are wondering what the heck that tboot entry in the boot menu is for, don’t worry about it. It’s just a bug. It will not show up in Fedora 19 final.
Here’s an introductory video about Intel Trusted Execution Technology.




Hi,
I managed to remove tboot menu from grub2 by,
su
yum -y remove tboot
grub2-mkconfig -o /boot/grub2/grub.cfg
I was told that tboot will not be in the final, but that obviously is not the case. On a test installation, I reinstalled GRUB and tboot showed up in the boot menu.
The TPM is a processor and vault on a chip. In other words, a smart card chip. I can provide truly random numbers from its generator, it can do encryption, it can store, lockbox style, passwords etc. and it is hardware.
The TPM can work with the bios to prevent a bios load and it can be used in wonderful ways to augment security. Hardware based security is it. By the way, you cannot slice the chip to discover its innards or memory. It is built to be distructable. My mother board has a slot to where I can plug one in.
This feature appeared in fedora 18 as a regular update also.
I think it actually goes back to Fedora 16, but this is the first time it’s showing up by default in GRUB’s menu.
> Not sure what it’s for, I selected it and hit the Enter key.
«Enter» too dangerous. For such cases most suitable «e» key.
I did that too, but it didn’t tell me anything.