For professional security researchers, participating in bug bounty programs is one means of earning money on the side. It is also the easiest means of building up street-cred. And many companies take advantage of their skills, recognizing that its either they find and fix bugs in their products first or the bad guys do and exploit them. For Black Hats, the underground market for exploit code is a very lucrative one.
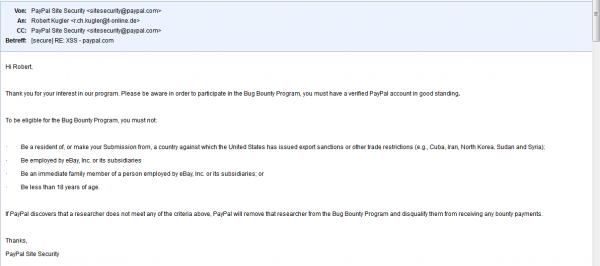
So, many companies run these bug bounty programs to encourage White-Hat security professionals to show off their skills and make some money, while doing so. Robert Kugler is one such security professional who took part in Paypal’s bug bounty program. He found a Cross-Site Scripting (XSS) bug on Paypal.com and reported it, hoping to collect whatever reward was due.
But Paypal refused to pay. Why? At 17 years of age, Robert Kugler, according to Paypal, does not meet the age-related eligibility requirement for participating in the program. Curiously, that specific requirement is not stated in the publicly available description of the program, which is available here.
Not happy with Paypal for refusing to pay, Robert posted his finding (and the exploit code) at Packet Storm.
The email exchange between him and Paypal is shown in the three images.
I think if this age-related requirement had been made very clear in the programs description, Paypal would have a good case for refusing to pay the bounty to Robert. So obviously, Robert is not a very happy kid. Paypal recognizes that and is trying to patch things up.
But Paypal’s way of compensating Robert for his efforts is a “Letter of Appreciation,” which you may read here (PDF file).
In that letter, Paypal promised to send him “some more tangible signs of our appreciation of your efforts.” Let’s wait and see what Paypal’s “more tangible signs of our appreciation” translates into.









Hope PayPal likes having zero-days posted to the FD list with no advance warning.