Ubuntu Business Desktop Remix is an edition of Ubuntu Desktop tweaked for use by institutional or business users. It was announced by Mark Shuttleworth, the founder of Ubuntu, in this blog post. The first release is based on Ubuntu 11.10 Desktop Live CD. So what is the difference between it and the end-user desktop Live CD edition?
According to Mark, the business edition “takes the most common changes we’ve observed among institutional users and bundles them into one CD which can be installed directly or used as a basis for further customization.” Those changes include removing “features like music players or games” and adding “components that are a standard part of their business workflow.”
That brings up this question: What is the penetration or adoption rate of Ubuntu Desktop in the business sector? I do not have the numbers, and Canonical has not released any, as far as I know, but given that Mark and Co. have had a rough going trying to persuade PC vendors to pre-load Ubuntu Desktop on personal computers sold to the public, I doubt that the adoption rate is significant. If true (I could be wrong, though), I do not thing that a separate desktop edition for business users will make any difference.
Here are reasons I think so, why Ubuntu Business Desktop Remix will be a tough sell to serious businesses, that is, those serious about protecting their assets and maximizing employee productivity?
Before we get to the reasons, here is the boot menu.

Now, to the reasons:
- Businesses now routinely stipulate that mobile computers (notebooks, ultrabooks, netbooks, etc) issued to employees be secured with full disk encryption. The reason is simple: Full disk encryption protects the data stored on a computer form those not authorized to view or modify it, as happens when the computer is lost or stolen. For example, back in 2009, Intel began deploying full disk encryption on all laptops issued to employees, and within 12 months, 75% of those computers were protected with full disk encryption. I do not have the latest figures, but I am almost certain that it should be 100% today. Besides businesses, full disk encryption has been required on all laptops owned by the Federal government, the US government that is, since 2006 (pdf).
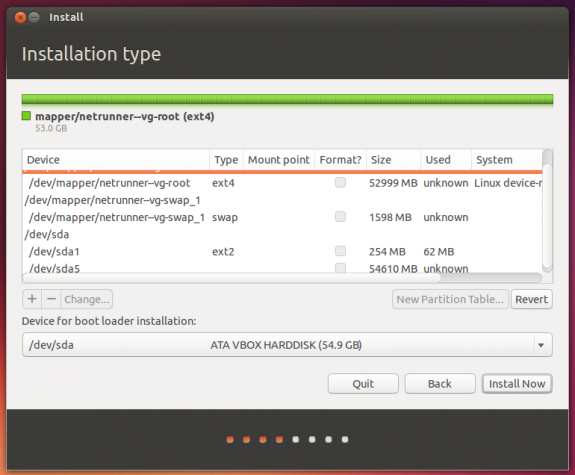
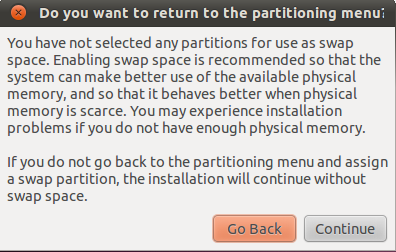
But the problem with Ubiquity, the installation program of Ubuntu Desktop Live CD, which is the same one on Ubuntu Business Desktop Remix, is that it lacks support for full disk encryption. That is despite popular demand and a campaign by the Electronic Frontier Foundation to bring full disk encryption to Ubuntu Live CD. The only physical security feature supported by Ubiquity, is encryption of the user’s home directory, which in the context of this discussion, is useless. So, until full disk encryption is implemented in Ubiquity, I do not think that major business entities will even consider Ubuntu Desktop or Ubuntu Desktop Business Remix. This screen shot was taken while attempting to install Ubuntu Desktop Business Remix. If you have installed Ubuntu Desktop, it should be familiar to you.

Note: In most states in the USA, the law requires that the authorities be notified when a business computer containing personal identification data (social security number, driver’s license number, debit or credit card number, etc) is lost or stolen.
- Ok, the second reason might not be a show-stopper, but how many businesses do you think will issue a laptop to employees when the login screen has a guest session enabled? I do not know the answer, but I do know that is one “feature” that many end users want to disable after installing Ubuntu Desktop.

- The final reason is the user interface, the desktop itself. I do not use Ubuntu, but since Unity became the graphical interface on Ubuntu Desktop, there has been an almost endless cry for Canonical to “stop this madness.” But like the developers of GNOME 3, Mark Shuttleworth and Co. have forged ahead, trying to redefine the Linux desktop backwards. Unlike the default GNOME 3 interface, which looks and feels bad no mater how many times you look at it or use it, Unity looks good at a first glance, until you start using it to do serious computing. Then you find out how badly it sucks. That is my experience. Maybe, businesses have had a different take. May be CEO’s have been urging their IT staff to deploy Ubuntu Desktop all over the place. Most of Europe could also be experiencing a heat wave right now. The screen shot below was taken from a new installation of Ubuntu Business Desktop Remix.

If you are interested in taking Ubuntu Business Desktop Remix out for a test drive, download an installation ISO image from here. Note: Registration is required, and only a 32-bit edition has been released.



FTW if you buy a laptop full disk encryption is in the TCI bits of the BIOS (now UHCI since yes, 2006.) Had businesses planned to give people ca. 2005 laptops, that this escaped your notice?
So, how can you not see tasks running concurrently if you mouse to Gnome3’s top-left overview trigger? It’s not like Fedora or EagleMode, then?
You did not say or cite how Gnome3 (r2) was dislikable, or detail the failures once ‘serious computing’ had been achieved (not a common use case I think; aim for a MS, get a 11th grader) with WebGL or whatever, but I’d consider this a review if you did.
Of course one also expects instaboot movie-player options, but those are -also- UHCI features drawn from a patent portfolio (still, I think) orthogonal to Microsoft’s.
Contrawise, you could shorten the review to ‘no iTunes/iPad executable VM, thus no adoption, QED.’ At least point at the dog of the Way Forward; otherwise, it is much like whinging that hybrid LED/HID bathroom lighting takes too long to pay for itself and you already know where things are.
“Unity looks good at a first glance, until you start using it to do serious computing. Then you find out how badly it sucks.”
When I worked at the phone company, the first half hour of my day was spent logging into the various computer systems I needed to access to do my work. These systems had to run concurrently.
This is supposedly a business desktop, and what do we see? No ability to see what programs are running concurrently! Doesn’t anyone at Canonical actually want to run programs concurrently? How would you expect a person to work across several computer systems?
That is why people use a windows environment: so they can run programs concurrently! “Oh, you can Alt-Tab”. I got RSI from doing Alt-Tab! That is an extremely bad habit, and should never be encouraged! Do you want to cripple your employees?
You can’t even see when one of the programs you have concurrently running has an alert. Right now I have 3 programs running, and I can see them along the bottom edge of my screen, and one of them is the superior Pidgin Instant Messenger, and the writing is in Bold font, so it is telling me I have some new emails. Can Unity do that?
What is so difficult to understand about “the customer is always right”!!!
I save all my sensitive data in /etc, I don’t know about you
1. I think the regulations state that full-disk encryption is sufficient, but not necessary. They explicitly say that non-sensitive data does not need encrypting, and it would be hard to argue that the OS itself is sensitive data. On Windows XP systems, user data can be found in many places across the filesystem, so FDE might be the only way to guarantee protection. A properly managed Linux system should keep it all in the home directory, so there is not a strict need to encrypt /usr, /etc, etc. [Yes, I’m aware that /tmp and swap ought to be protected too/]
2. I could give a good argument for keeping a guest user on a business laptop – then there is absolutely no reason for sharing the main user account for non-business purposes, children’s games, etc. Think of all the stories of viruses introduced by the family.
3. I suspect businesses that don’t like Unity will positively hate Windows 8 tiles! But as has been noted, there is still a choice of interfaces available.ding
4. Regarding root access – it’s easy to disable root/sudo access and manage centrally, if that’s what you want. Or to use the first account as a local admin if you prefer that way of working.
Oh come on. “Unlike the default GNOME 3 interface, which looks and feels bad no mater how many times you look at it or use it”
Its not for everyone, and obviously wouldn’t be ideal for businesses, but I really like gnome-shell. I use it on my home laptops and its great. Smooth and polished, and features like the instant messaging integration are really well done.
You can always use a dock if you don’t like having to use the overlay.
But that’s why I wrote “Unlike the default GNOME 3 interface…”
Another reason (not mentioned) is that the first user created can gain root privileges using their own password.
Spot on, esp about the lack of full disk encryption.
“Most of Europe could also be experiencing a heat wave right now.”
🙂
Personal opinion: At present, KDE is the only desktop environment that I feel fits business needs.
“Ubuntu Desktop, there has been an almost endless cry for Canonical to “stop this madness.”
This is there biggest problem, following the farce of the KDE “upgrade” the Linux desktop upgrade options are a joke.
We use Linux on the Desktop and I have a boss friendly to it but I can’t recommend we stick with it at the moment.