This example shows how to specify a port range in your rules. Using the ports from the last two examples before this one, we specify a port range in the form: port1:port2. One advantage of using a port range is that it reduces the number of rules that you create.

Specifying port ranges in a rule
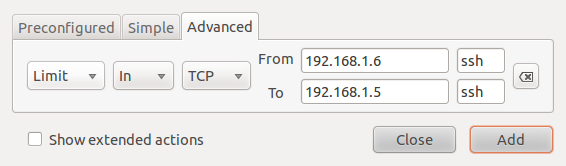
There are four policies that can be defined in a rule: Allow, Deny, Reject and Limit. The effect of an Allow rule is self-explanatory. If a packet matches a Deny rule, the packet will be dropped silently. The source host is not notified. Reject will trigger an ICMP destination unreachable message back to the source host. Limit rules are used to place a cap on the number of unsuccessful attempts from a host. They protect against brute-force attacks. In ufw, the number of unsuccessful attempts that will trigger a rate-limiting rule is 6 (or more) within the last 30 seconds. When a rate-limiting rule is triggered, subsequent packets from the offending host are denied (DROPped). Rate limiting rules may be defined from all three tabs, not just from the Advanced tab.

Actions
The following example shows a rate-limiting rule for incoming ssh traffic from a specific source to a specific destination.

Anti brute-force attack rule