When Sperical Cow hits the digital shelves sometime in late October or early November, users will have to get used to a new firewall management application. Sperical Spherical Cow is, of course the code-name for Fedora 18, the next stable release of Fedora.
On current versions of Fedora, the firewall management application is system-config-firewall, a static firewall application that requires a refresh of the firewall with any rule change. The new application will provide a dynamic system that will not require a refresh or reload of the firewall, even after a rule change.
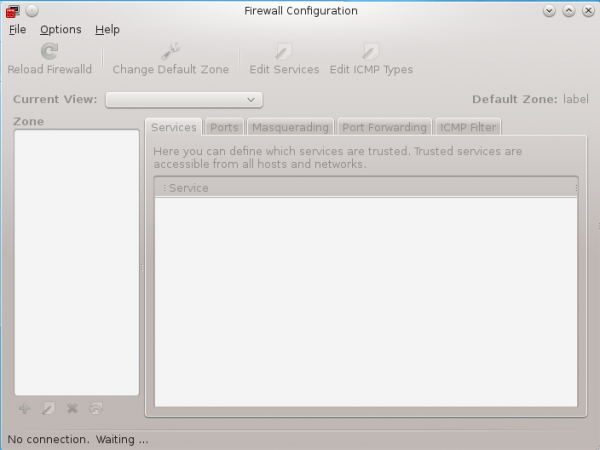
The new kid on the block is called Firewalld, and it is made up of a daemon with a D-BUS interface – firewalld; a command line interface – firewall-cmd; a graphical management interface – firewall-config; and a desktop applet – firewall-applet. Most of the work has been done, but not all the parts are working, at least in the just released Fedora 18 Alpha that I tested.
In this alpha release, Firewalld is installed and running, but firewall-applet is not installed. This, for example, is the interface for firewall-config. It does not work, so I could not mess with it. But you can tell that the final product will be easy to manage.

With Firewalld and coupled with NetworkManager, you will be able to utilize network zones on your system. The Shields Up/Down interface, which you start from the firewall applet, makes it easy to manage configured zones.

This is a screen shot of the firewall-applet. The options are self-explanatory.

What the applet looks like when network traffic is blocked.

Here is an excerpt from the Fedora wiki what Firewalld really brings to the table:
The dynamic firewall mode with firewalld will make it possible to change firewall settings without the need to restart the firewall and will make persistent connections possible.
This is for example very useful for services, that need to add additional firewall rules. libvirtd is one of them and also openvpn in the future. With the static firewall model these rules are lost if the firewall gets modified or restarted. The firewall daemon holds the current configuration internally and is able to modify the firewall without the need to recreate the complete firewall configuration; it is also able to restore the configuration in a service restart and reload case.
Another use case for the dynamic firewall mode is printer discovery. For this the discovery program will be started locally that sends out a broadcast message. It will most likely get an answer from an unknown address (the new printer). This answer will be filtered by the firewall, because the answer is not related to the broadcast and the port of the program that was sending out the message is dynamic and therefore a fixed rule can not be created for this. With the dynamic firewall mode a time limited rule could be requested by the discovery program to allow the receipt of the answer.



How to disable firewalld?
Uninstall it.
This article should help.
sp: spherical cow