Kali Linux is the latest incarnation of BackTrack Linux, an Ubuntu-based distribution for penetration testing. It is developed and maintained by Offensive Security, an outfit that provides security training and certification courses for IT professionals.
It has been described by its developers as the “the most advanced and versatile penetration testing distribution ever created.” Whether you agree with that statement or not, this article gives you an idea of what type of applications and features are available on this first edition of Kali Linux.
Where BackTrack was based on Ubuntu and used a GNOME 2 desktop environment, Kali Linux 1.0 is based on Debian and uses a customized GNOME Shell. The customized GNOME Shell comes with a menu called kali-menu that is fashioned to look like a GNOME 2-type menu. Fans of desktop environments other than GNOME 3 should take comfort in the fact that Kali’s build system makes it relatively easy to rolling their own using KDE, LXDE, Xfce, E17 or MATE.
A reader made a comment here about not being able to boot Kali from a thumb drive on an OEM machine with UEFI firmware pre-installed with Windows 8. While I can’t comment specifically on OEM machines pre-installed with Windows 8 (because I don’t have one), I can say that I was able to boot Kali on a non-OEM machine with UEFI firmware.
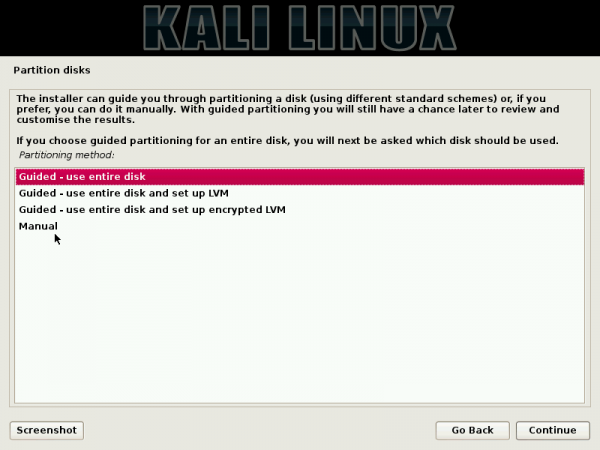
Being based on Debian (Debian Wheezy), Kali also uses its parent distribution’s installation program, the first Debian-based distribution I have reviewed in a while that uses the Debian Installer (DI). What that means is that Kali gives you more features (during installation) than BackTrack, Ubuntu or any other distribution derived from Ubuntu. This screen shot shows the installer’s disk partitioning options.

Unlike BackTrack, where you had to start the graphical desktop manually – even after installation, Kali boots into a graphical desktop environment automatically. The installer allows you to specify the root account’s password during installation, but not a standard user account. When using the Live desktop, the password for the root account is toor, the same as the root account on BackTrack.
As a niche distribution, the most important features offered by Kali are the applications that make it what it is. And since it will be impossible to demo how to use even a small percentage of what it ships with, or list every single one, the best that can do here is offer a screen shot of the menu’s application categories. Note that the developers maintain a repository that syncs with Debian testing repository four times daily, so you get bleeding-edge versions of applications and kernel that Debian has to offer. Kali’s kernel is not a plain-vanilla kernel, but a Debian kernel patched for wireless injection.

About those applications, there’s virtually no open source or Free Software security or hacking tool you might need that’s not pre-installed on Kali Linux 1.0. Most of the applications available on the last edition of BackTrack 5, except those with duplicated features, are on Kali. Whether it’s for hardware hacking, sniffing and hacking wireless networks, hacking Android devices, forensic investigation, and Web applications exploitation, you’ll likely find it installed in Kali Linux. Note: Just be sure that you do not use them in a manner and in an environment that will get you in trouble.
Note also that Kali comes with a graphical application manager (gpk-application) that makes it easy to install any application from the repository, so you can install productivity tools like LibreOffice 3.5 and OpenOffice 3.4, both of which are in the repository.
Because it uses the GNOME 3 desktop environment, it also comes with all the graphical management tools that ships with any distribution that uses GNOME 3.

So, here are the screen shots that give you a peek into the types of applications you can find. For starters, this screen shot shows the top 10 hacking applications on Kali Linux.

Information Gathering > OS Fingerprinting applications.

Vulnerability Analysis > Database Assessment applications.

Web Applications > Web Vulnerability scanners

Password Attacks > Online attack applications.

Wireless reconnaissance and attack applications.

Exploitation Tools > Social Engineering applications.

Sniffing/Spoofing > Voice surveillance tools.

Reverse Engineering applications.

Android hardware hacking applications.

Reporting and evidence management applications.

You may read more on what Kali Linux brings to the table here and download ISO or VMWare images from here. Aside from Intel-compatible systems, Kali is available for the following ARM devices: rk3306 mk/ss808, Raspberry Pi, ODROID U2/X2, and Samsung Chromebooks.





I’m glad to see something new from the backtrack geniuses. I’m actually downloading kali right now. I hope its less buggy out of the box as bt5 was,is. I never did get metasploit to work correctly in bt5-bt5r3. Crossing my fingers, nice review, first look for me, thanks.
If your looking for a comparison to bt5, kali is a great performance improvement. I only use a few tools like Armitage, aircrack, ettercap, easy-creds etc.but I’m impressed not only with the lack of problems, but the speed of the os. Everything I do is faster using the same computer. Reaver for example does consistent 2 second pin attempts. If your on the fence go for it. If you use easy-creds you’ll have to add it, but no biggie. The problems I had with every version of bt5 with metasploit problems updating are gone, right out of the box. Aircrack keys per second up about 8% with dictionary crack, on same hardware, of course your mileage will vary, Good bye bt5r3 DVD, putting you to rest.
For me, it’s not that I mind a feature review, per se. It’s just that I came from from DistroWatch expecting a normal review. Maybe even a comparison to BackTrack.
It’s tough to give a “normal” review of this type of distribution, since it is all about apps that are not for very specific tasks. I think it’s a waste talking about desktop computing stuff since potential users don’t and won’t care about that. Maybe next time, I’ll make an effort in that direction.
Kali is just an old edition of BackTrack. The major difference, which I think I mentioned in the article, is that Kali is based on Debian (and uses the Debian Installer), while BackTrack was based on Ubuntu Desktop (and uses the Ubiquity installer). See BackTrack 5 or Kali Linux 1.0.
Could you suggest me where can i find tutorial (books, websites, etc) of all of the kali-linux tools? already familiar with major tools like nmap, airomon-ng, but i am curious to know them all. thanks b4..
I agree with Krevin Linguini, this is simply a feature review.
But that was made known in the second paragraph by “…this article gives you an idea of what type of applications and features are available on this first edition of Kali Linux.” Where you expecting to learn how to use all 300 hacking and penetration testing applications?
Were you looking for an article on how to (mis)use tools like Nmap, Kismet, etc ;)?
Thanks for this review. I think it’d be improved though if you added some thoughts. Currently the article is more just of a feature summary than a review. Even another paragraph at the end would help. Thanks