With recent revelations about browser fingerprinting, the race is on to find ways and means that will help reduce your browser’s fingerprint, and with it, make it difficult for it (and you) to be tracked.
After trying Panopticlick yesterday, a tool released by the Electronic Frontier Foundation to help users determine if their browser is safe against tracking and fingerprinting, I set out to find out how to make my browsers less unique to trackers.
For the very paranoid, the results are not good.
Under default settings, a browser like Mozilla Firefox and Iceweasel emit very unique fingerprints, as shown in the result of a Panopticlick test in Figure 1. “Default settings” implies that DNT (Do Not Track) is disabled, and cookies are accepted. Pay special attention to how many other browsers have the same fingerprint as the target browser.
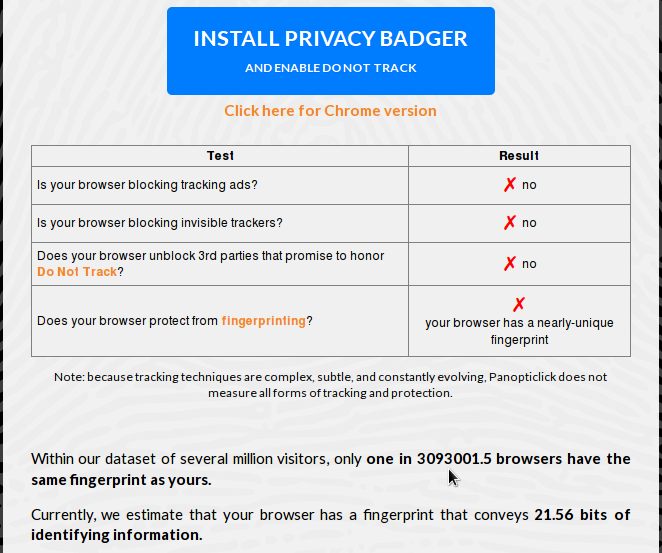
Figure 1: Browser fingerprinting under browser default settings
Enabling DNT makes no difference to the result of the test.
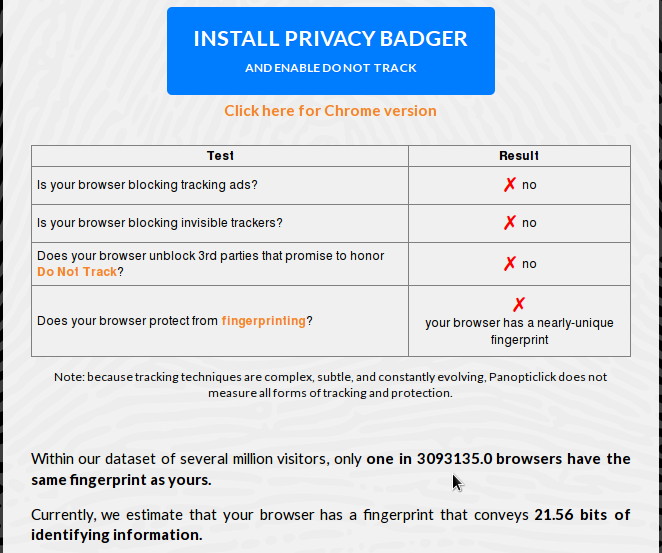
Figure 2: Browser fingerprinting with DNT (Do Not Track) enabled
Even with DNT and cookies rejected globally, the browser still has a unique fingerprint which was even worse than when cookies were accept.
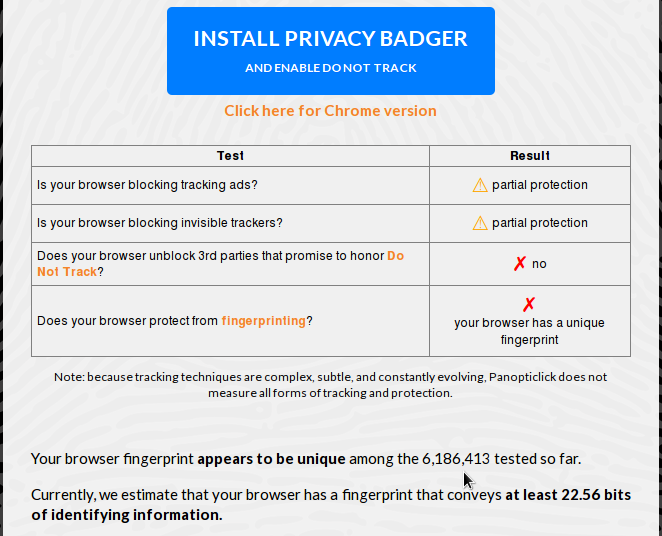
Figure 3: Browser fingerprinting with DNT (Do Not Track) enabled and cookies disabled
With Privacy Badger installed, still keeping DNT enabled and cookies rejected, the result is only as good as when DNT was enabled, which means not very good.
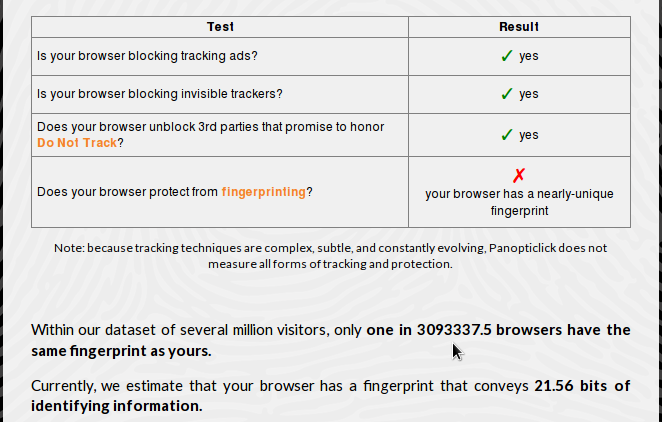
Figure 4: Browser fingerprinting with Privacy Badger installed
Throw NoScript in the mix, and your browser stands out like a sour thumb, which is counter to the expected result.
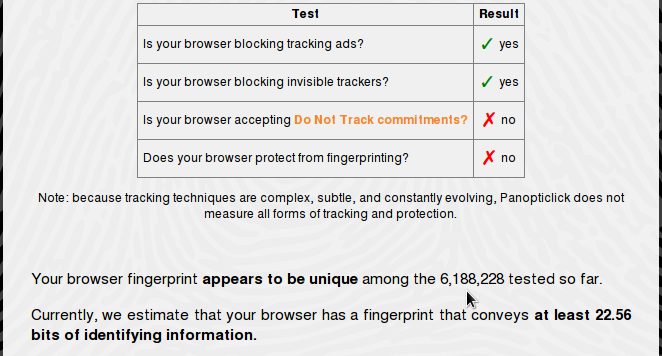
Figure 5: Browser fingerprinting with Privacy Badger and NoScript plugins installed
On a KDE desktop, there’s an option in the System Settings that can be used to disable browser identification in Konqueror, the native KDE browser and file manager. It can also be used to give a fake identification to the browser.
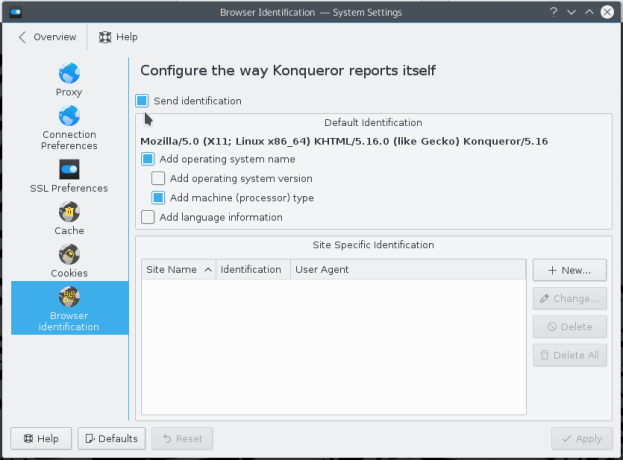
Figure 6: KDE Konqueror browser identification
However, disabling sending browser identification is useless, as it still leaves your browser with a unique fingerprint.
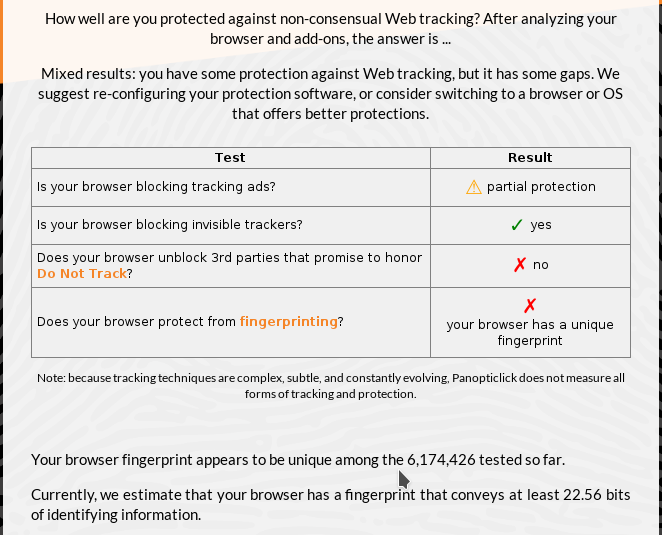
Figure 7: Browser fingerprinting test on Konqueror
So despite all the browser tools and options that can be deployed and tweaked to give a browser a less unique fingerprint, nothing seems to make any real difference. And from what I’ve seen so far, the more plugins installed and the more options enabled/disabled, the more unique your browser becomes. It’s like getting your phone number on a “Do Not Call” list. To learn a bit more about this topic, the EFF has some suggestions here.




If you are using the Firefox extension Random Agent Spoofer, your browser finger print will look highly distinctive. However, since the user agent will change to some other value every few minutes, the ability to track you through finger printing is greatly impaired.
Extremely interesting article. Coincidentally, I took the Panopticlick test today with pretty much the same results that you outlined in your article. If only I could turn my system into a virtual Fort Knox! Seems like trackers are persistently against web surfers getting any kind of privacy! The internet means business…
I run stock Debian Jessie but with a back-ported Iceweasel (currently version 43.0.2). My panopticlick number is 1 in 8600, so i think I’m as close to the norm as possible.
I was getting numbers similar to those you outline in the article until I installed the following add-on’s:
– Total Spoof
– Privacy Badger
– NoScript (using the default settings)
I’m not sure if these also affect the numbers, but I’ve also installed these ad blockers:
– uBlock Origin
– Disconnect
Here’s the Panopticlick output:
Test Result
Is your browser blocking tracking ads? ✓ yes
Is your browser blocking invisible trackers? ✓ yes
Is your browser accepting Do Not Track commitments? ✗ no
Does your browser protect from fingerprinting? ✓ yes
Note: because tracking techniques are complex, subtle, and constantly evolving, Panopticlick does not measure all forms of tracking and protection.
Within our dataset of several million visitors, only one in 8632.85185185 browsers have the same fingerprint as yours.
Currently, we estimate that your browser has a fingerprint that conveys 13.08 bits of identifying information.
Hope this helps.
Eddie