
Sagemath in the Cloud and Sagemath 5.11
August 20, 2013
No Comments
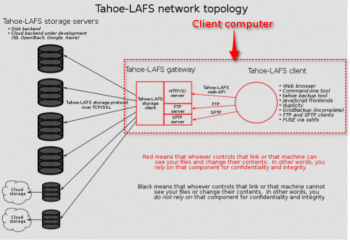
Tahoe Least-Authority File System for secure, distributed data storage
August 17, 2013
2 Comments

4 host-proof or PRISM-proof Cloud storage services
August 17, 2013
10 Comments
Elementary OS 0.2 “Luna” review
August 16, 2013
32 Comments

Ubuntu Edge sets crowdfund record, but could still fail
August 16, 2013
1 Comment

Google to Gmail users: Forget about privacy. It’s so dead!
August 14, 2013
9 Comments
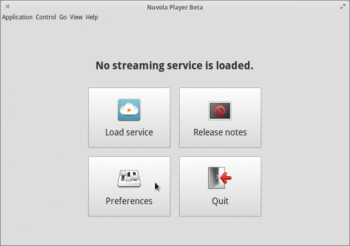
Nuvola Player: Enjoy all your Cloud music services from one interface
August 14, 2013
No Comments

Microsoft’s Surface RT is an “Unmitigated Disaster.” What’s wrong with that?
August 13, 2013
6 Comments

Developers: Give us sane and sensible default system and application settings
August 13, 2013
18 Comments

The Android-powered MeMO Pad™ HD 7 is just $149
August 12, 2013
No Comments

I quit using Linux because…
August 12, 2013
33 Comments
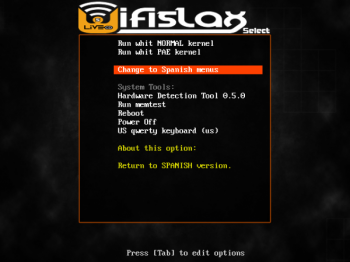
Wifislax 4.6 review
August 8, 2013
No Comments
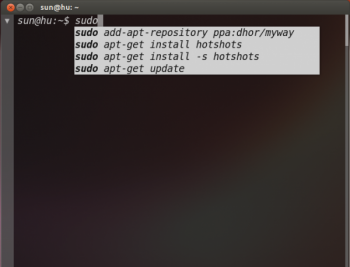
Final Term: A terminal emulator to rule them all
August 7, 2013
10 Comments
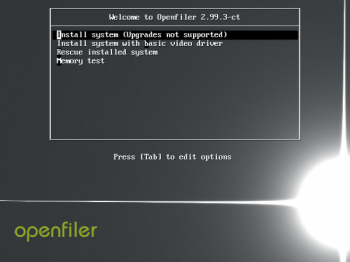
Openfiler is moving to CentOS
August 1, 2013
No Comments

Memo to HP: A backdoor is not a vulnerability
July 31, 2013
No Comments



















