

Use HTC Scribble app to create photo blogs, diaries and greeting cards
November 23, 2013
No Comments

The problem with using CAcert’s digital certificates
November 22, 2013
1 Comment

Safeplug offers plug-and-play anonymous Web browsing using Tor
November 22, 2013
3 Comments
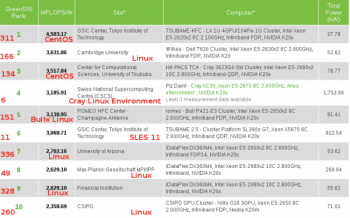
Green500 List top 10 are all powered by NVIDIA Tesla GPUs and Linux
November 21, 2013
No Comments
Mainframe2, NVIDIA GRID and the future of streamed apps. Don’t leave Linux out
November 21, 2013
1 Comment
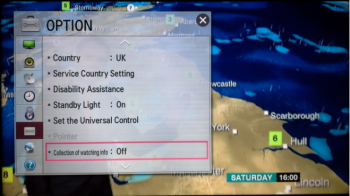
Smart TV, Spy TV. Is that LG Smart TV spying on you?
November 20, 2013
No Comments
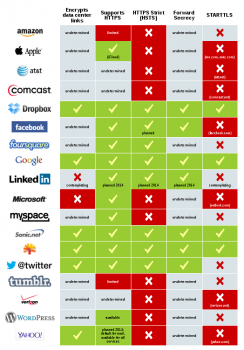
Are Web service providers encrypting their data?
November 20, 2013
No Comments
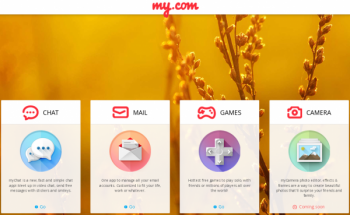
Mail.ru launches My.com, offering mail, chat, games and image editor
November 20, 2013
No Comments
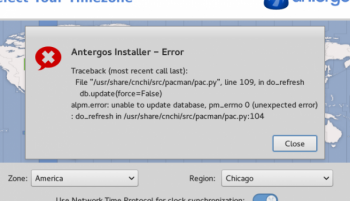
Antergos 2013.11.17 review
November 19, 2013
4 Comments
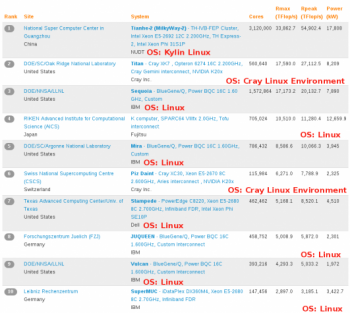
482 of the Top500 supercomputers run Linux, and China’s Tianhe-2 is the fastest
November 18, 2013
No Comments

Linux Mint 16 Petra Cinnamon Desktop screenshot preview
November 16, 2013
No Comments

GNUnet submits draft for p2p-related TLDs to the IETF
November 16, 2013
No Comments

SecureDrop, SafeSource and Strongbox: Different names, same app
November 15, 2013
No Comments

How Exynos 5 Octa HMP efficiently allocates workload to big.LITTLE CPU cores
November 15, 2013
No Comments

ZShaolin Android terminal updated
November 15, 2013
No Comments



















