
Upgrade the kernel on Linux Mint 17.2
September 3, 2015
1 Comment

Configurable mintMenu stops working after upgrading to Linux Mint 17.2
September 3, 2015
No Comments

Kernel panic on Linux Mint 17.1
September 3, 2015
No Comments
KDE 5 Application Dashboard: A fullscreen app launcher that beats the competition
September 2, 2015
1 Comment

Installing NGINX and NGINX Plus With Ansible
August 19, 2015
1 Comment
Clustering a Node.js application with Mongo, Docker and Rancher
August 19, 2015
No Comments
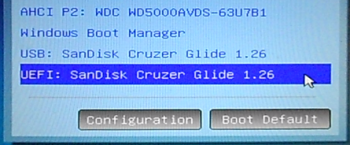
How to dual-boot Linux Mint 17.2, Windows 10, Windows 8.1 on a PC with UEFI firmware
August 18, 2015
68 Comments
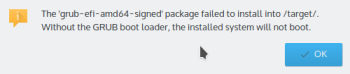
GRUB-Install errors while attempting to dual-boot Windows 10 and Linux distributions
August 12, 2015
6 Comments
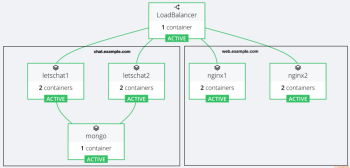
Virtual Host Routing for Docker using Rancher Load Balancer
July 31, 2015
No Comments
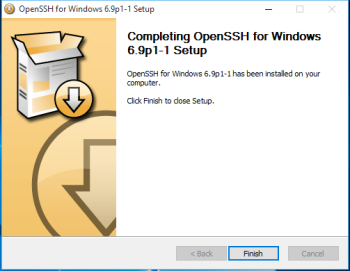
How to install OpenSSH on Windows 10
July 30, 2015
13 Comments
Upgrading Windows 8.1, Windows 7 to Windows 10
July 30, 2015
No Comments

How to implement Docker-as-a-Service
July 29, 2015
No Comments
Will an upgrade to Windows 10 on a dual-boot system mess GRUB up?
July 29, 2015
25 Comments

How to configure caching in Nginx
July 28, 2015
No Comments
Fedora 23 will feature a Cinnamon Spin
July 28, 2015
No Comments



















