


nginScript: A JavaScript tool for configuring NGINX
September 24, 2015
No Comments

Flatcar: A tool for creating Docker-ready Rails projects
September 24, 2015
No Comments

Clustering Atomic Hosts with Kubernetes, Ansible, and Vagrant
September 24, 2015
No Comments

Using Flannel as a soft-defined networking solution for rkt containers
September 24, 2015
No Comments

Docker 1.8 and the New Daemon Command
September 13, 2015
No Comments

Chronicles of SELinux: Dealing with web content in unusual directories
September 13, 2015
No Comments
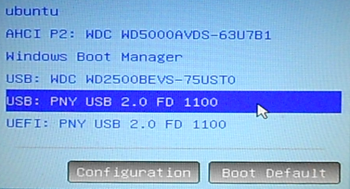
How to install Ubuntu 15.04, Linux Mint 17.2 on an external hard drive
September 13, 2015
4 Comments

Tips for installing a Linux distribution on an external hard drive
September 12, 2015
No Comments

Use Convoy to Backup, Recover a WordPress MySQL database with Docker
September 9, 2015
No Comments

Weave introduces ‘Gossip’ DNS service discovery for containers
September 8, 2015
No Comments

How to use fedora-tools image for Fedora Atomic Host
September 8, 2015
No Comments
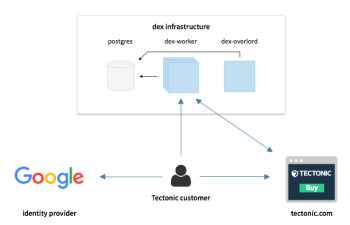
dex: A OpenID Connect Identity Provider from CoreOS
September 8, 2015
No Comments
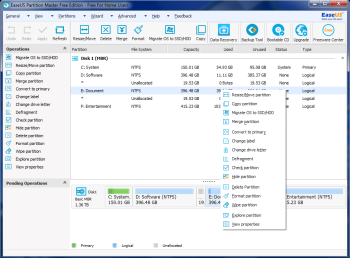
EaseUS Partition Master Free: A full-featured disk manager for Windows
September 7, 2015
1 Comment
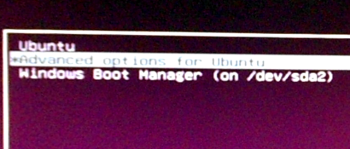
How to dual-boot Ubuntu 15.04 with Windows 10 on a single hard drive
September 7, 2015
5 Comments
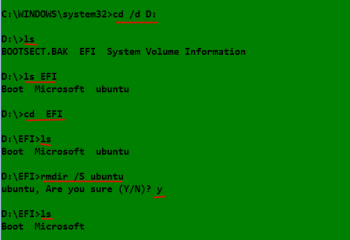
How to delete GRUB files from a Boot EFI partition in Windows 10
September 5, 2015
199 Comments



















