‘Tis the season for upgrading.
This hour, the target is OSSEC. Next will be a Cloud server running Ubuntu 12.04 LTS, which will be upgraded to Ubuntu 14.04 LTS
OSSEC is a cross-platform and Free Software “host-based Intrusion Detection System that performs log analysis, file integrity checking, policy monitoring, rootkit detection, real-time alerting and active response.”
It is one of the best of its kind, and one piece of software you want on your server as soon as it’s online. Most tutorials you read advocate Fail2ban, but OSSEC brings a lot more to the table than Fail2ban. Don’t get me wrong, Fail2ban is nice to have on your server, but OSSEC is nicer.
Before the upgrade, the target server was running OSSEC 2.7.1. It was then upgraded to OSSEC 2.8, which was released on June 4 (2014). Upgrading OSSEC is a very simple operation, but I ran into a problem at the end. More on that later. For now, here’s how the upgrade was done.
Downloaded OSSEC 2.8 from here. Verified its checksums and moved the compressed tarball to the server. Unpacked it (tar zxf ossec-hids-2.8.tar.gz), changed to the OSSEC directory (cd ossec-hids-2.8), and started the installation by typing ./install.sh.
Your language is likely supported by the installation script.

It wil detect that there’s an existing OSSEC installation and ask for an upgrade.

From this screenshot, you can tell that something did not go as intended: OSSEC analysisd. Testing rules failed. Configuration error. Exiting.

Querying the status of OSSEC showed that it is not running. What can the log file tell me?

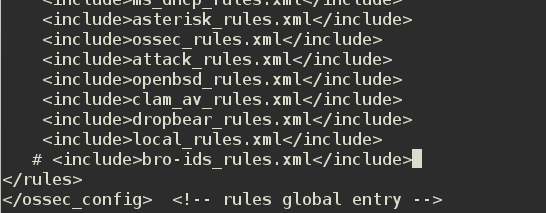
Entries in the log file revealed the cause of the problem: The program failed to load the bro-ids rule: Invalid decoder name: ‘bro-ids’. Error loading the rules: ‘bro-ids_rules.xml’.

I found out that the issue with bro-ids rules is a longstanding one and that the recommended fix, if you can call it that, is to uncomment the

Now, OSSEC is up and running, monitoring the system and sending email alerts when it detects bad traffic.