A security research outfit has released a report which revealed that more than 300,000 routers in homes and small businesses have been hacked.
Team Cymru, the US-based security outfit which published the report, said that the network of hacked routers is one of the biggest of its kind that has been discovered, with most of the hacked routers in Columbia, India, Italy, Thailand, and Vietnam.
Most of the hacked routers have the following common features: Owners who didn’t know how to configure their routers, insecure default settings (factory-default passwords was not an issue), backdoors in firmware, firmware version vulnerable to a known Cross-Site Request Forgery CSRF) technique, and graphical user interfaces accessible from the Internet.
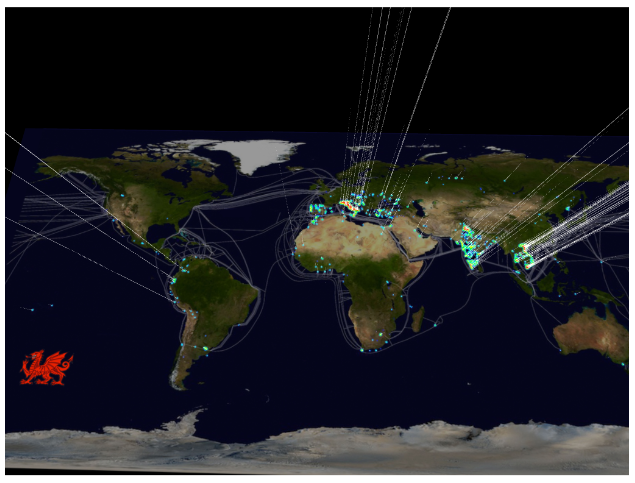
The hacked router had their DNS settings modified, which is just as bad (maybe worse) than having the end-point computers themselves hacked. This image shows a heatmap distribution of the 300, 000 hacked routers.

In this particular network of hacked routers, I don’t think it would have made any difference if the computers behind those routers have host-based security tools installed. But it certainly wouldn’t hurt to have the best security tools that you can get installed on your computer(s). The problem with Internet routers is that, for most users, they are an install-it-and-forget-it-device. I think asking users to reset their Internet routers often might not be such a bad idea.
Details about the 300,000 hacked routers are available in this PDF file.