This short tutorial shows how I configured Nginx to protect against hotlinking of images used in my articles. Protecting against image hotlinking in Nginx is pretty simple, if you know what to do, or know how to google.
So if you don’t like my approach, go ahead and google “image hotlink protection in nginx” or something close to that.
In simple terms, hotlinking is stealing. That’s what it is. And the perpetrator is a thief. In slightly more technical terms, hotlinking is directly linking to images (usually) that reside on a website’s server, on your own. The recommended practice is to copy an image you are interested in and save it on your own server, then use it in your articles. I do it all the time, but some website owners are too lazy to bother.
Hotlinking is also know as inline linking, piggy-backing and leeching. I prefer that last one, because it conjures up the image of a parasite, which is what an hotlinker is. A lazy website owner is stealing bandwidth from another webmaster.
That was the problem I’ve been having with a publisher who has been reproducing my articles verbatim, hotlinking images in the process. The rest of this article shows how I configured Nginx to protect against the hotlinking.
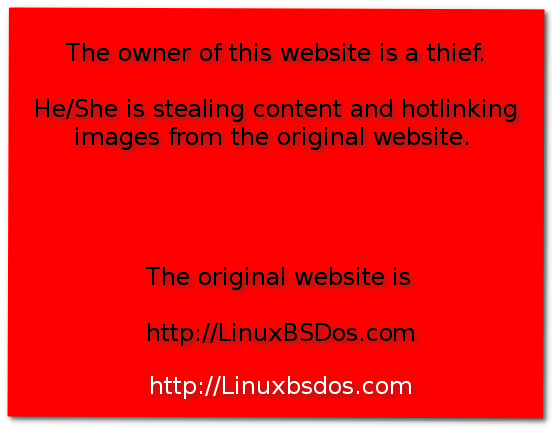
I had two options: 1. Configure Nginx to refuse to serve images to the thief; 2. Serve a special image that tells the whole universe that the owner of the website they are viewing is a parasite. Because majority of the articles published on this site tend to be image-heavy, serving a special image that delivers a message will have the same impact on my bandwidth, so I chose option number 1.
In the site’s config file, I put this in the server{} context:
location ~* \.(jpg|jpeg|png)$ {
valid_referers none blocked www.linuxbsdos.com linuxbsdos.com;
if ($invalid_referer) {
return 403;
}
}
That works. Every image hotlinked from this website will just show the “alt” text on the thief’s website, with a lot of white space where the image is supposed to be. Any attempt to view the image will return a “403 Forbidden” error page. I’m pretty sure that’s the best configuration to use, but if you know of a better manner of setting it up, please post a comment.
The other option, which I did not use, is this:
location ~* \.(jpg|jpeg|png)$ {
valid_referers none blocked www.linuxbsdos.com linuxbsdos.com;
if ($invalid_referer) {
rewrite (.*)\.(jpg|jpeg|png|gif)$ http://www.linuxbsdos.com/parasite.png last;
}
}
That rewrite line can be tricky to pull off, so be careful if you want to consider using it. This screen shot shows the image I wanted to deliver. If the message and the color combination seems a bit harsh, that tells you how I feel about the offender. For now, a “403 Forbidden” will do.