Aside from revealing the names of specific programs that the government has been using to violate the privacy of all and sundry, to most people who have been keeping track of what’s going on over the past twenty years or more, nothing Edward Snowden has so far revealed is news.
I know that a significant percentage of the population don’t care, because as far as they are concerned, “If you don’t have anything to hide, what’s the problem?”
To those people, there’s nothing you can say to convince them that a violation of privacy is a violating of privacy, whether the victim(s) have something to hide or not. But worse than that, they fail to see that this matter has implications that go beyond personal privacy.
I’ve read many articles that try to educate people on this very subject, and just came across one today. It was written by Dan Tobon of Cyphertite, a company that offers host-proof Cloud storage services. This article was published almost two months, but it’s never too old to read. Here’s an excerpt.
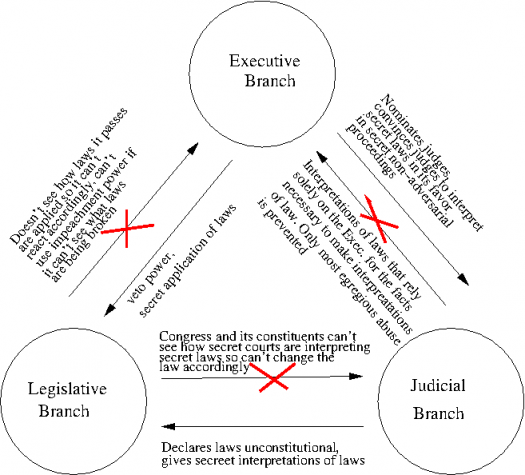
This is essentially a matter of the complete circumvention of the checks and balances which are the requisite safeguards in our representative democracy. Viewed from this perspective the issue becomes far more worrisome. In essence if the executive branch1 is able to effectuate a process that enables it to seemingly comply, but in effect avoid, these institutional checks on power the entire system fails its operative function.
The recent actions of the Executive branch, through the DOJ and the intelligence services, and its confederates in the secret Foreign Intelligence Surveillance Court (FISC) have seemingly engineered this very use case.
…
…FISA theoretically purported to set in place a system of judicial safeguards which would monitor and prevent Executive overreach and abuse of power. In practice what has occurred is the blanket legitimization of all but the most egregious domestic surveillance activity on the part of the government. Due to the governments prior indiscretions FISA was passed in order prevent unwarranted surveillance of Americans.
Instead it has effectuated a process by which the Executive can escape meaningful scrutiny and circumvent the institutional checks on its power provided for in our Constitution. Ostensibly, it is like catching a criminal in the process of committing a crime and then appointing him and his friends to be the judge and jury at his trial.
You may read the complete article here.